Author: Cybernoz
Researchers warn that the Gafgyt botnet is actively exploiting a vulnerability impacting the end-of-life Zyxel P660HN-T1A router. A variant of…
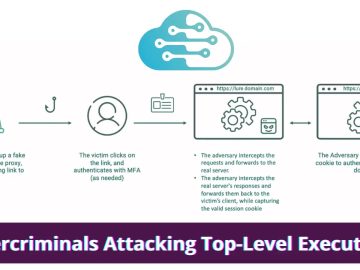
The top-level executives at more than 100 global organizations have been shaken by cloud account takeover incidents. Leveraging the power…
A threat actor known as ‘Fredens-of-security’ on BreachForums has reportedly taken credit for exposing sensitive data linked to India’s Ministry…
Artificial intelligence is disrupting global business and economies in unprecedented ways, a trend set to become more pronounced over the…
As per reports, Microsoft .NET core and Visual Studio were found with a Denial of Service, which can be exploited…
The Second quarter of 2023 has shown a significant increase in the overall cyber-threat risks. The blocking of unique web…
A sophisticated cyber attack orchestrated by unidentified cyber criminals has resulted in the unlawful acquisition of $6 million from a…
Malware, being one of the most prevalent and pervasive initial threat vectors, continues to adapt and become more sophisticated, according…
The ThreatSec hacker group has taken responsibility for infiltrating a data center under the jurisdiction of the Indonesian government. According…
Germany’s Federal Office for the Protection of the Constitution (BfV) warns that the Charming Kitten APT group targeted Iranian dissidents…
Ransomware groups often recycle tools, techniques, and procedures. Even some of them also provide playbooks for affiliates as well. Numerous…
In today’s digital age, where mobile devices have become an integral part of healthcare delivery and patient management, maintaining the…