Author: Cybernoz
A man from Tracy, California, has been charged with a computer attack on the Discovery Bay water treatment facility. Rambler…
When the marital infidelity website AshleyMadison.com learned in July 2015 that hackers were threatening to publish data stolen from 37…
07 Jul Global Ransomware Damage Costs Predicted To Exceed $265 Billion By 2031 Posted at 15:08h in Blogs, Videos by…
CISA ordered federal agencies today to patch a high-severity Arm Mali GPU kernel driver privilege escalation flaw added to its list of…
Jul 07, 2023Swati KhandelwalMobile Security / Malware Researchers have issued a warning about an emerging and advanced form of voice…
Progress released security patches for a new critical SQL injection vulnerability affecting its MOVEit Transfer software. Progress is informing customers…
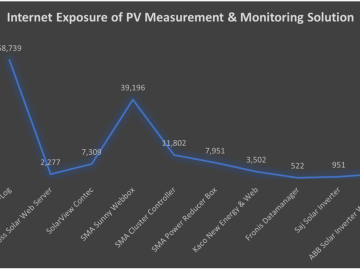
More than 130,000 photovoltaic monitoring and diagnostic solutions are accessible from the public internet, which could make them susceptible to…
The July 2023 security patches have been released by Android and more than 43 vulnerabilities in the Android Operating System…
Microsoft and Amazon Web Services (AWS) are calling on communications regulator Ofcom to hold off on getting the Competition and…
The Open Source Foundation for Application Security (OWASP) announced a five-dimensional secure software development maturity reference framework (SwSec 5D) in…
Mastodon, the free and open-source decentralized social networking platform, has patched four vulnerabilities, one of them critical that allows hackers…
An authentication bypass vulnerability exists in VMware SD-WAN (Edge). Upon successful exploitation, unauthorized attackers gain access to the application’s Diagnostic…