Author: Cybernoz
Today, mental health, thankfully, is more widely understood as a vital aspect of overall well-being. It impacts our emotional, psychological,…
Financial services and other businesses across the world will spend hundreds of billions on regtech in 2028 as “increasingly complex”…
What do businesses need to do to comply with the Children’s Online Privacy Protection Act (COPPA) in the US? Here…
Hours after reports of the alleged CoWIN data breach surfaced, the Indian government refuted the claims stating that the Health…
Progress Software, the operator of the MOVEit Transfer managed file transfer product, has released a second patch for a newly…
FIIG Securities, Australia’s largest fixed income specialist with over 6,000 investors and $5 billion of funds under advice, has fallen…
Questions remain about the potential impact on datacentres from generative artificial intelligence (AI) adoption, even when it comes to the…
Extreme Networks has disclosed that it is the latest technology company affected by the fast-developing MOVEit cyber attack, with downstream…
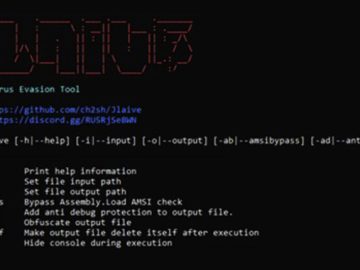
Jun 12, 2023Ravie LakshmananEndpoint Security / Malware A fully undetectable (FUD) malware obfuscation engine named BatCloak is being used to…
The latest “technology pulse” poll from EY reports that 78% of tech executives are more concerned about the cyber security…
Molly Greene, The Appeal’s strategy and legal director, calls the censorship alarming. “It’s incredibly concerning to hear readers say they…
Jun 12, 2023The Hacker NewsAttack Surface Management The term “attack surface management” (ASM) went from unknown to ubiquitous in the…