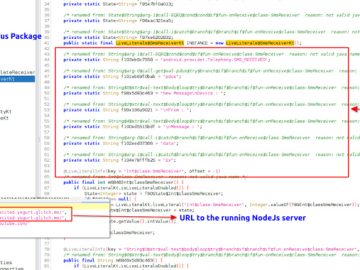
Author: Cybernoz
CTF (Capture The Flag) exercises have existed for several years. These CTF exercises provide a great challenge and provide great…
Sometimes information is available, but not exactly easy to find. This should never be the case for a Security Team’s…
Law firms and cybersecurity are terms we coin only when it comes to litigation. However, an increasing number of law…
Better bug reports = better relationships = better bounties. Whether you are new to bounty programs or a bounty veteran,…
Today we are kicking off our new competition, Hack The World 2016! Not only can you win some awesome prizes…
Thank you for joining! Access your Pro+ Content below. 30 May 2023 Can the UK cash in on chips? Share…
The RaidForums data leak story continues. A user going by the alias Impotent claimed to have data from RaidForums, which…
The best hackers use their creativity to find vulnerabilities. They are not bound to the vulnerability types that they already…
NoName hackers attacked Lithuania, as their DDoS attacks continue. Among the victims are the e-services of the Seimas, Lithuania’s parliament,…
May 30, 2023Ravie LakshmananMobile Security / Android A new open source remote access trojan (RAT) called DogeRAT targets Android users…
Hacker cinema from the 1990’s upon original release was criticized as being “dubious,” “unrealistic,” and “implausible.” Blast ahead 20 years…
We recently launched the Hack The World competition to challenge you all to find as many vulnerabilities as possible over…