Author: Cybernoz
Last week on Malwarebytes Labs: Update now: 9 vulnerabilities impact Cisco Small Business Series ChatGPT: Cybersecurity friend or foe? Webinar…
While hunting for bug bounties, attack surface plays a major role. Hacking on mobile adds more juicy attack surface and…
High quality reports result in higher bounties and happier security teams. The best vulnerability reports provide security teams with all…
Hello friends, and welcome to HackerOne’s first edition of “Fact or Fiction,” where we review shows and talk about how…
Today, we are excited to share HackerOne’s 2016 Bug Bounty Hacker Report. Bug bounty programs are flourishing, but without a…
The HackerOne founders in their previous company. We’ve seen phenomenal participation in the Hack The World 2016 contest since we…
Welcome to HackerOne’s second edition of “Fact or Fiction,” where we review hacking entertainment and discuss how realistic (or not!)…
The first week of your bounty program can be the most critical. The decisions you make around bounties, how long…
In February 2023, JPCERT/CC confirmed malware attacks on routers in Japan, specifically targeting Linux routers with a new Golang RAT…
The more you let friendly hackers hack you, the less the criminals can hack you. Bug bounty programs are revolutionizing…
With your on-premise security solution comprising hardware, software, signatures, rules, and even machine learning, you may think your applications are…
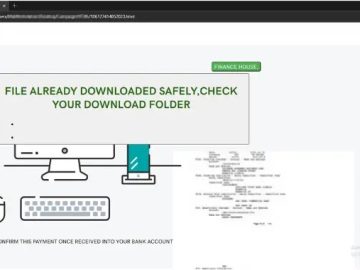
The creator of this Invicta malware is heavily active on social networking sites, using them to advertise their information-stealing malware…