Author: Cybernoz
Microsoft has decided to allow customers to choose when the last bits of Internet Explorer 11 (IE11) will be removed…
Malware is an umbrella term for viruses, trojans, spyware, adware etc. It is an abbreviation of “malicious software”. Spyware, as the…
Group-IB’s cybersecurity researchers made a significant discovery, revealing undisclosed attack infrastructure employed by the highly active state-sponsored group SideWinder. Their…
On May 16, Google announced new plans to delete accounts that have been inactive for two years, as well as…
Tam Cymru researchers have recently revealed noteworthy patterns and irregularities from their continuous monitoring of QakBot’s command and control infrastructure. …
The Department of Justice revealed today that an 18-year-old man named Joseph Garrison from Wisconsin had been charged with hacking…
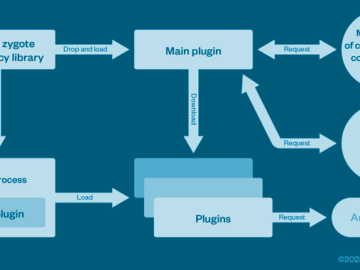
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious…
Hacking can be tedious work. Sometimes you’ve been looking for hours, perhaps days, and you’re unable to find a security vulnerability….
Hackers are now actively probing for vulnerable Essential Addons for Elementor plugin versions on thousands of WordPress websites in massive…
Security misconfiguration is the fifth vulnerability on OWASP‘s list of the ten most common vulnerabilities. A proof of concept video…
To all those who are eagerly searching for ChatGPT login and Midjourney web pages, here’s an alert that needs your…
Bitwarden released Bitwarden Passwordless.dev, the developer toolkit with an extensive, easy-to-deploy API for integrating FIDO2 WebAuthn-based passkeys into consumer websites…