Author: Cybernoz
Using components with known vulnerabilities is one of the vulnerability categories on OWASP‘s list of the ten most common vulnerabilities. A proof…
Disclosure is in the DNA of HackerOne. We call it Hacktivity and have supported public disclosure workflows of vulnerability reports…
Cisco warned customers today of four critical remote code execution vulnerabilities with public exploit code affecting multiple Small Business Series…
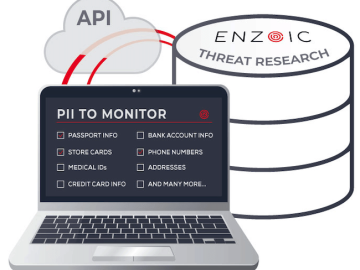
Enzoic launched an identity monitoring offering, enabling organizations to continuously track and ensure their users’- whether its customers or employees–…
Security never stands still, which is why we update our service on a regular basis to help you keep up…
Microsoft has pulled a recent Microsoft Defender update that was supposed to fix a known issue triggering persistent restart alerts…
Each year, at the request of police and intelligence agents across the country, the United States Postal Service conducts surveillance…
Meta is introducing Meta Verified on Facebook and Instagram. The popular social networking platform will now permit anyone who agrees…
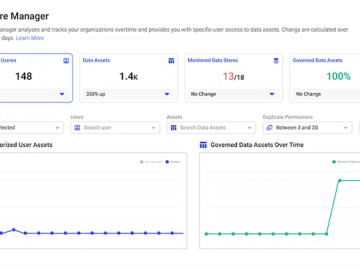
Satori has released Posture Management, a new capability within Satori’s platform that monitors the authorization of users to data across…
Recently, the cybersecurity experts at Checkpoint identified that the Chinese state-sponsored group “Camaro Dragon” employs a custom “Horse Shell” malware…
Geacon, a Cobalt Strike implementation written in Golang, is likely to attract the attention of threat actors looking for vulnerable…
It’s been over a year since Grammarly launched its first bug bounty program on HackerOne. It’s been a private, invite-only…



![[Release] New modules – Detectify Blog Beta feature: New and more consistent crawler](https://image.cybernoz.com/wp-content/uploads/2023/05/Beta-feature-New-and-more-consistent-crawler.jpg)