Author: Cybernoz
Cloudflare released a threat report for DDoS of Q1 2023, showing that cyber threat actors use VPS-based attack vectors instead…
The Prudential Regulation Authority (PRA) at the Bank of England has fined the former CIO of TSB bank for his…
The Belgian government has recently announced a new Belgian law that will allow ethical hackers to hack any Belgian company…
Apr 14, 2023The Hacker NewsVirtual CISO / Cybersecurity In today’s fast-paced and ever-changing digital landscape, businesses of all sizes face…
Step 1 – Recovering the corrupted data According to the doc, the following stream is corrupted: 7b 0a 20 a0…
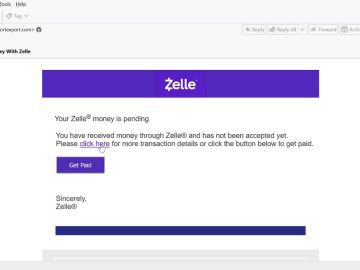
Cybercriminals have been leveraging social engineering techniques to impersonate the popular US-based digital payments network Zelle and steal money from…
Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities…
Validate security policies like you mean it Not everything on your attack surface is a vulnerability. Every organization has their…
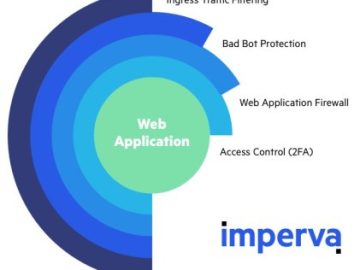
Cybercriminals are always on the lookout to exploit web application vulnerabilities. Over the years, hacking techniques and methods employed by…
What if we could send AI a message as soon as it wakes up? Created/Updated: April 3, 2023 There is…
Basic security best practices to share with your non-technical friend. Readers of my blog typically know more about technology and…
Note that during these interviews I also moderate thus quality may vary. Profile 🐝 Head of research at Portswigger University…