Author: Cybernoz
When it comes to bug bounty hunting and finding exciting areas to explore, it is vital to familiarise yourself with…
The domains for Genesis Market, one of the most popular marketplaces for stolen credentials of all types, were seized by…
[ This article was originally published here ] UK government potentially skimps on senior cyber role salary as the NCSC…
Executing essential cyber security operations tasks during the threat hunting process is an increasingly challenging proposition to the vast majority…
Tl;dr: We have updated our reward system to make it easier for you to know what you might earn with…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
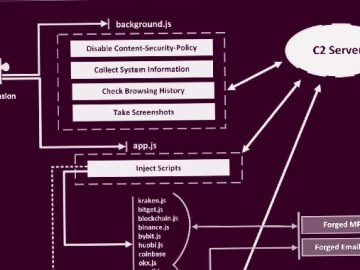
Apr 04, 2023Ravie LakshmananBrowser Security / Cryptocurrency Chromium-based web browsers are the target of a new malware called Rilide that…
HPE has re-vamped its storage-as-a-service (SaaS) offer with Greenlake for file storage, block storage, plus data protection and disaster recovery offerings….
Security teams know, bug bounty hunters, and ethical hackers know it: Large attack surfaces are hard to manage. In this…
Microsoft says Rockstar Games has addressed a known issue affecting its launcher, causing the Red Dead Redemption 2 (RRD2) game…
Researchers from Kaspersky Labs uncovered a new wave of 3CX supply chain attacks targeting cryptocurrency companies to implant Gopuram. A…
When OpenAI released GPT-3 in July 2020, it offered a glimpse of the data used to train the large language model….