Author: Cybernoz
Hackers are adding malicious functionality to WinRAR self-extracting archives that contain harmless decoy files, allowing them to plant backdoors without…
Software supply chain attacks, in which hackers corrupt widely used applications to push their own code to thousands or even…
The Tor browser guarantees that your communication remains operational through a decentralized network of transfers maintained by volunteers located worldwide….
[ This article was originally published here ] We all learn differently. And we all have different schedules and needs…
After being in hiatus for some time, IntelBroker, a well-known initial access broker from BreachedForums, has made a comeback. This…
Attacking JWT – Header Injections Source link
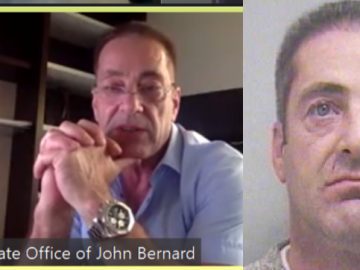
John Clifton Davies, a 60-year-old con man from the United Kingdom who fled the country in 2015 before being sentenced…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
Privileged Access Management (PAM) solutions are regarded as the common practice to prevent identity threats to administrative accounts. In theory,…
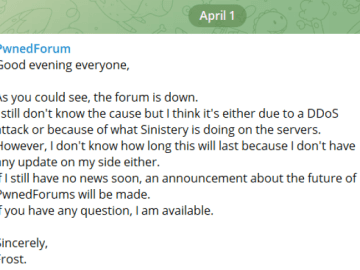
The Cyber Express, like five other news services, received an email on 2 April from a person under the alias…
Answering your questions about Superbacked Source link
According to the government’s privacy regulatory body, Italian authorities have recently placed a temporary hold on the ChatGPT due to…