Author: Cybernoz
Customers of 3CX, a unified communications technology supplier, are being targeted by a North Korea-linked advanced persistent threat (APT) actor…
Sean Burns | 08 December 2022 at 10:45 UTC If you follow the Burp Suite roadmap, then you’ll know that…
A new modular toolkit called ‘AlienFox’ allows threat actors to scan for misconfigured servers to steal authentication secrets and credentials…
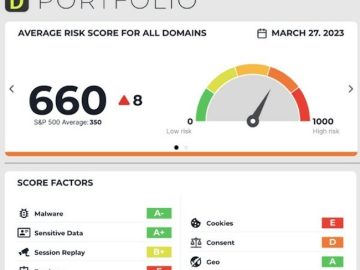
LOKKER has released its LOKKER Web Privacy Risk Score, the assessment tool that provides businesses with a clear, numeric rating…
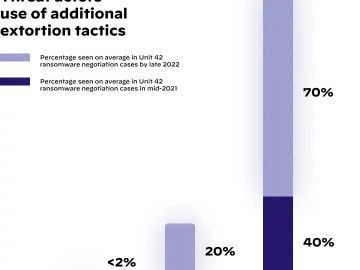
Multi-extortion has been increasing, and companies are harassed in many ways to extract a ransom payment in return. Ransomware attacks…
The World’s 1st Open Source Bug Bounty Guide – Methodology, Tools, Resources by Mik317 (50+ CVEs) Source link
H0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus to… you. That…
Mar 30, 2023Ravie LakshmananSupply Chain / Software Security 3CX said it’s working on a software update for its desktop app…
Cloud Hacking: The Basics Source link
As Europe’s enterprises return to normal following the COVID-19 pandemic’s impact, they are looking for innovative and cost-effective ways to…
UK on AI: The UK government today published a white paper outlining a “pro-innovation approach” to regulating artificial intelligence (AI),…
Cyber Security Challenge Germany (2023) Source link