Author: Cybernoz
Google Cloud Platform (GCP) lets G Suite and Cloud Identity users create what are called “Organizations”. GCP organizations can be…
Thank you for joining! Access your Pro+ Content below. 14 March 2023 Digital dedication – the transformation of Guinness World…
14 March, 2023; Dubai, United Arab Emirates – Microsoft today brought a message of collaboration and resilience to GISEC 2023,…
A good friend of mine and successful bug bounty hunter, Corben Leo, discussed in a blog post how he spotted…
Recently, the cybersecurity researchers at eSentire have identified a shady piece of malware downloader, BatLoader, that has been engaged in…
Hopefully, you’ve been working with the Center for Internet Security (CIS) on securing your cloud infrastructure for a while now….
Ring, a popular home security company, has allegedly been the target of a data breach by the ALPHV ransomware group….
External Attack Surface Management (EASM) is the continuous discovery, analysis, and monitoring of an organization’s public facing assets. A substantial…
Offensive security released Kali Linux 2023.1 with new tools for purple and blue teamers for defensive security. On March 13th…
Managing user access in applications has always been a headache for any developer. Implementing policies and enforcing them can prove…
Mar 14, 2023Ravie LakshmananNetwork Security / Cyber Attack Government entities and large organizations have been targeted by an unknown threat…
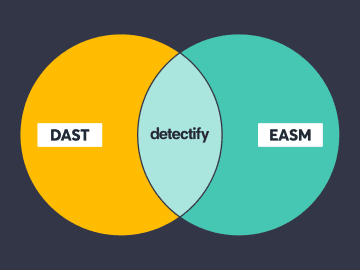
There’s often a lack of understanding when it comes to DAST as a methodology versus DAST as a tool. How…