Author: Cybernoz
A new wave of cyber threats is emerging as criminals increasingly weaponize AdaptixC2, a free and open-source Command and Control…
WhatsApp has announced a significant security upgrade that makes protecting your chat backups simpler and more secure than ever before….
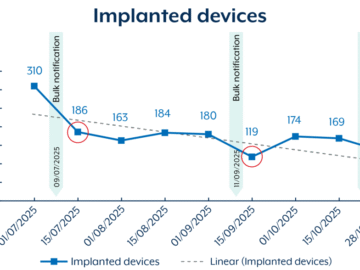
BadCandy, a Persistent Access Threat to Network Edge Devices BadCandy is a Lua-based web shell implant deployed on compromised Cisco…
A Ukrainian national believed to be a member of the Conti ransomware operation has been extradited to the United States…
Threat actors operating under the control of North Korea’s regime have demonstrated continued technical sophistication by introducing advanced malware toolsets…
Threat intelligence researchers have uncovered a growing campaign where cybercriminals are weaponizing AdaptixC2, a legitimate open-source Command and Control framework…
Oct 31, 2025Ravie LakshmananVulnerability / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and National Security Agency (NSA),…
India’s cybersecurity landscape is witnessing rapid growth, with the Indian Computer Emergency Response Team (CERT-In) playing a central role in driving this transformation. According…
Suspected Chinese actors compromise U.S. Telecom firm Ribbon Communications Pierluigi Paganini October 31, 2025 A nation-state actor, likely a China-nexus…
Chinese-affiliated threat actor UNC6384 has been actively leveraging a critical Windows shortcut vulnerability to target European diplomatic entities across Hungary,…
Michael Calore: Yeah. My favorite indiscreet product placement was in the show Entourage from HBO. It was on TV, I…
Progress Software has released security patches to address a high-severity vulnerability in its MOVEit Transfer platform discovered on October 29,…