Cybersecurity firm Group-IB, alongside the Royal Thai Police and Singapore Police Force, announced the arrest of a prolific hacker linked to over 90 major data breaches across 25 countries, including 65 attacks in the Asia-Pacific region.
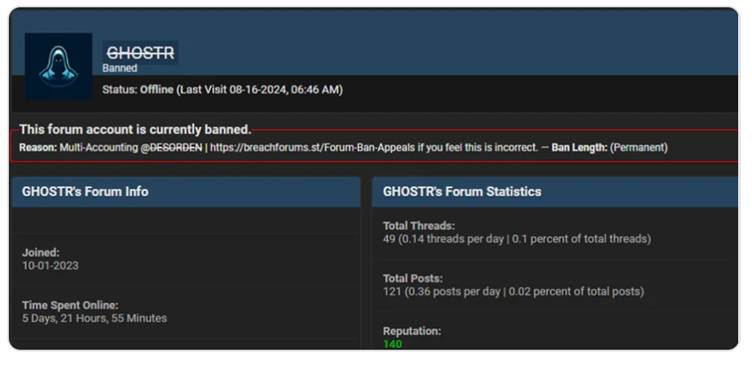
The cybercriminal, operating under aliases ALTDOS, DESORDEN, GHOSTR, and 0mid16B, exfiltrated 13 terabytes of sensitive data between 2020 and 2025, targeting industries from healthcare to government agencies.
The arrest marks a critical victory in global efforts to combat dark web crime syndicates and protect digital infrastructure.
The Operation and Arrest
The joint investigation, spearheaded by Group-IB’s Digital Crime Resistance Centers (DCRCs) in Thailand and Singapore, culminated in a raid on the hacker’s Thailand-based hideout.
Authorities seized laptops, electronic devices, and luxury goods purchased with illicit profits from dark web data sales.
The Royal Thai Police confirmed the individual’s involvement in attacks on multinational corporations, small businesses, and even government databases, with victims spanning Thailand, India, Indonesia, the UK, and the United States.




Initially active under the alias ALTDOS in 2020, the hacker focused on Thai entities, employing SQL injection tools like sqlmap and exploiting insecure Remote Desktop Protocol (RDP) servers to infiltrate networks.
Unlike typical ransomware actors, he prioritized data theft over encryption, threatening victims with public exposure via media outlets or data regulators unless paid.
For example, in 2022, he leaked 8 million customer records from a Thai e-commerce platform after the company refused extortion demands, causing severe reputational damage.
By 2023, rebranding as DESORDEN, he expanded operations across Asia-Pacific, targeting healthcare providers and financial institutions.
Group-IB’s analysts noted his shift to CobaltStrike beacon deployments for persistent access, though lateral movement within networks was minimal.
This phase saw the theft of 9.5 million patient records from a regional hospital chain, later sold on forums like BreachForums for cryptocurrency.
Global Escalation and Detection Evasion
The cybercriminal’s tactics grew bolder under the GHOSTR and 0mid16B aliases in 2024, with attacks on Western entities, including a UK logistics firm and a Canadian insurance provider.
To evade detection, he frequently altered personas, communication channels, and data-sharing platforms. Group-IB’s AI-driven dark web monitoring linked the aliases through linguistic patterns, posting formats, and victim geography.
For instance, a preference for Telegram channels and consistent misspellings in leaked files helped analysts correlate attacks across time zones.
The hacker’s breaches compromised sensitive data for over 40 million individuals, including national ID numbers, medical histories, and financial records.
In one case, a Middle Eastern government agency lost 2.7 terabytes of citizen data, triggering nationwide identity theft concerns.
Legal experts predict severe penalties under Thailand’s Computer Crimes Act and Singapore’s Cybersecurity Act, which allow for up to 20 years imprisonment for aggravated offenses.
This case underscores the importance of public-private partnerships in tackling cybercrime.
As Group-IB’s CEO, Dmitry Volkov, stated, “The arrest demonstrates that even the most elusive threat actors can be unmasked through persistent intelligence-sharing and technological innovation.”
Moving forward, INTERPOL plans to leverage the operation’s insights to enhance global dark web surveillance protocols, aiming to preempt similar large-scale campaigns.
Authorities urge organizations to patch RDP vulnerabilities, audit third-party access, and adopt threat-hunting tools to mitigate risks.
For victims, the takedown offers a semblance of justice—and a stark reminder of digital vulnerabilities in an interconnected world.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



