Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office (SOHO) routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service.
This allows its operators to hide a wide spectrum of malicious activities, from digital advertising fraud to password spraying.
According to Lumen’s Black Lotus Labs threat research team, while the AVrecon remote access trojan (RAT) compromised over 70,000 devices, only 40,00 were added to the botnet after gaining persistence.
The malware has largely managed to evade detection since it was first spotted in May 2021 when it was targeting Netgear routers. Since then, it went undetected for over two years, slowly ensnaring new bots and growing into one of the largest SOHO router-targeting botnets discovered in recent years.
“We suspect the threat actor focused on the type of SOHO devices users would be less likely to patch against common vulnerabilities and exposures (CVEs),” Black Lotus Labs said.
“Instead of using this botnet for a quick payout, the operators maintained a more temperate approach and were able to operate undetected for more than two years. Due to the surreptitious nature of the malware, owners of infected machines rarely notice any service disruption or loss of bandwidth.”
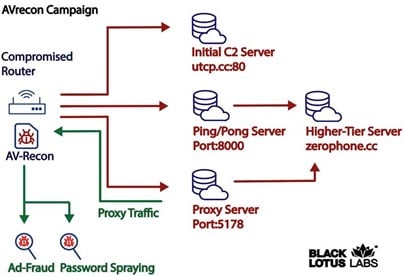
Once infected, the malware sends the compromised router’s info to an embedded command-and-control (C2) server. After contact making contact, the hacked machine is instructed to establish communication with an independent group of servers, known as second-stage C2 servers.
The security researchers found 15 such second-stage control servers, which have been operational since at least October 2021, based on x.509 certificate information.
Lumen’s Black Lotus security team also addressed the AVrecon threat by null-routing the botnet’s command-and-control (C2) server across their backbone network.
This effectively severed the connection between the malicious botnet and its central control server, significantly impeding its capacity to execute harmful activities.
“The use of encryption prevents us from commenting on the results of successful password spraying attempts; however, we have null-routed the command and control (C2) nodes and impeded traffic through the proxy servers, which rendered the botnet inert across the Lumen backbone,” Black Lotus Labs said.
In a recently issued binding operational directive (BOD) published last month, CISA ordered U.S. federal agencies to secure Internet-exposed networking equipment (including SOHO routers) within 14 days of discovery to block potential breach attempts.
Successful compromise of such devices would enable the threat actors to add the hacked routers to their attack infrastructure and provide them with a launchpad for lateral movement into their internal networks, as CISA warned.
The severity of this threat stems from the fact that such devices typically reside beyond the confines of the conventional security perimeter, greatly diminishing defenders’ ability to detect malicious activities.
“Threat actors are using AVrecon to proxy traffic and to engage in malicious activity like password spraying. This is different from the direct network targeting we saw with our other router-based malware discoveries,” said Michelle Lee, threat intelligence director of Lumen Black Lotus Labs.
“Defenders should be aware that such malicious activity can originate from what appears to be a residential IP address in a country other than the actual origin, and traffic from compromised IP addresses will bypass firewall rules such as geofencing and ASN-based blocking.”
