A critical security vulnerability in AWS Organizations has been discovered that could allow attackers to achieve complete control over entire multi-account AWS environments through a mis-scoped managed policy.
The flaw, identified in the AmazonGuardDutyFullAccess managed policy version 1, enables privilege escalation from a compromised member account to full organizational takeover, including potential control of the management account itself.
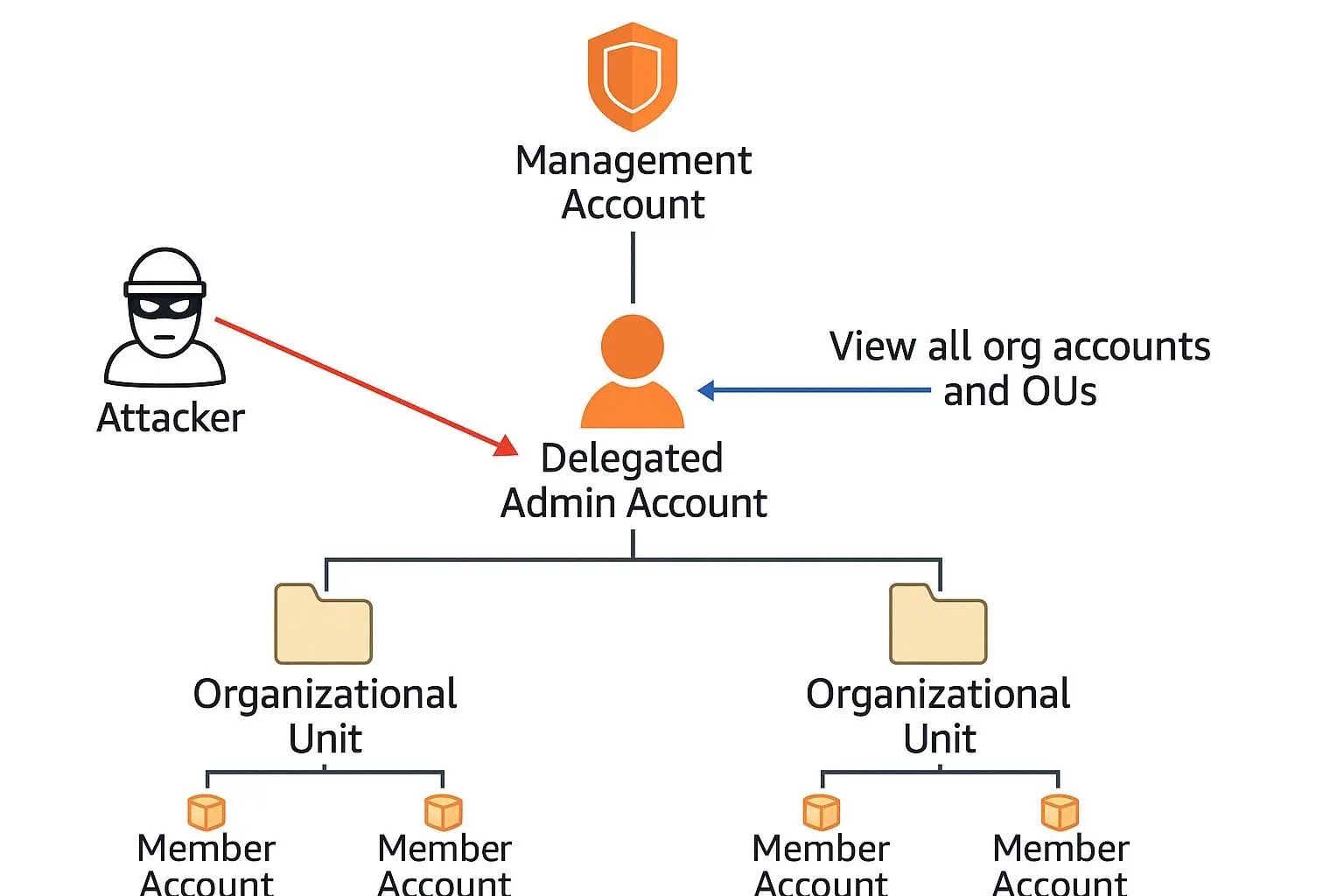
The vulnerability stems from an improperly scoped permission within the AWS-managed policy that grants the organizations:RegisterDelegatedAdministrator action with unrestricted resource access.
This oversight allows attackers who compromise a user or role in the management account with the vulnerable policy attached to register any account within the organization as a delegated administrator for sensitive services, effectively bypassing intended security boundaries.
The attack vector leverages AWS Organizations’ delegated administrator feature, which was designed to reduce reliance on highly privileged management accounts by allowing specific member accounts to administer services organization-wide.
However, the mis-scoped policy transforms this security feature into a powerful escalation mechanism.
An attacker can chain delegation privileges with control over a member account to gain administrative access to critical services such as AWS Identity and Access Management Identity Center (formerly SSO) or CloudFormation StackSets across all organizational accounts.
Cymulate researchers identified this vulnerability during their investigation of AWS Organizations cross-account pivoting and compromise scenarios.
The research team, led by Ben Zamir, discovered that the policy’s overly permissive structure could enable attackers to delegate sensitive services to accounts under their control, subsequently manipulating organization-wide identity management or deploying malicious infrastructure across the entire environment.
The technical exploitation process involves several critical steps that demonstrate the severity of this vulnerability.
Once an attacker compromises a management account identity with the vulnerable policy, they can execute the following command to register a controlled account as a delegated administrator:-
aws organizations register-delegated-administrator --account-id --service-principal Persistence and Privilege Escalation Mechanism
The most concerning aspect of this vulnerability lies in its ability to establish persistent, organization-wide access through legitimate AWS features.
.webp)
When an attacker successfully registers a compromised account as a delegated administrator for AWS Identity Center, they gain the ability to manipulate permission sets, user groups, and access configurations across all organizational accounts.
This capability allows them to add malicious identities to high-privilege groups or reset passwords of users with administrative access to the management account.
The persistence mechanism is particularly insidious because it operates through legitimate delegation channels that may not trigger traditional security alerts.
.webp)
Attackers can modify existing permission sets or create new ones with elevated privileges, ensuring continued access even if the initial compromise vector is discovered and remediated.
Additionally, the read-only organizational access granted to delegated administrators provides complete visibility into the environment structure, enabling attackers to identify high-value targets and plan sophisticated multi-account attacks.
AWS has responded to this discovery by releasing version 2 of the AmazonGuardDutyFullAccess managed policy with stricter resource constraints that eliminate the escalation path.
However, existing roles and users attached to version 1 remain vulnerable until administrators manually upgrade to the corrected policy.
Organizations should immediately audit all principals using the vulnerable policy and implement the updated version to prevent potential exploitation of this critical security flaw.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
