Cymulate Research Labs discovered a high-severity authentication bypass vulnerability in Microsoft Windows Admin Centre’s Azure AD Single Sign-On implementation that enables attackers with local administrator access on a single machine to compromise any other Windows Admin Center-managed system within the same Azure tenant.
The flaw, tracked as CVE-2026-20965, stems from improper validation of Proof-of-Possession (PoP) tokens and access tokens.
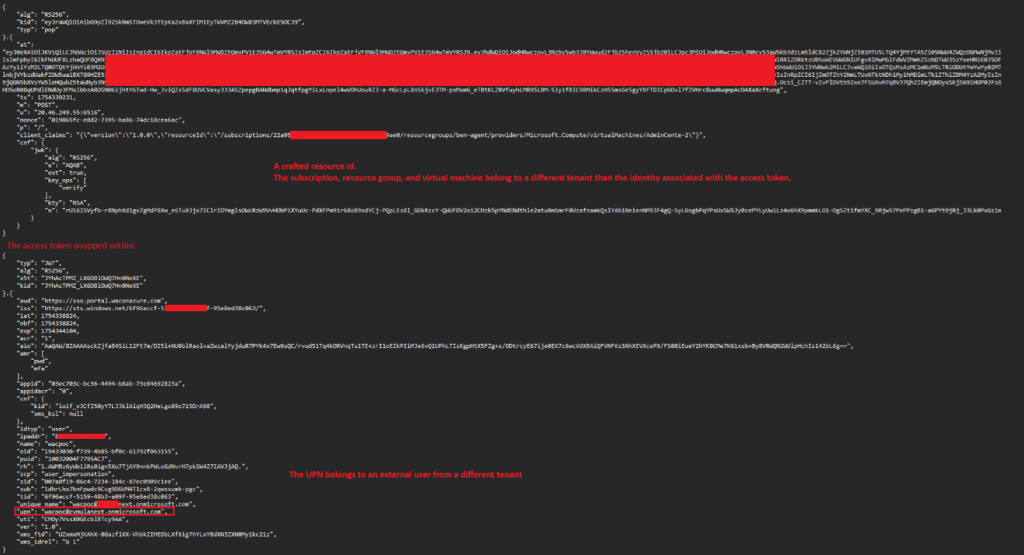
The Windows Admin Center server fails to verify that the User Principal Name (UPN) matches between the two required tokens, allowing attackers to combine a stolen privileged user’s access token with a forged PoP token from a different tenant or non-existent user.
Vulnerability Details
When administrators connect to Windows Admin Center via the Azure portal, the system requires two tokens: a WAC token.
Check the Access token, verify user permissions, and ensure a PoP-bound token is cryptographically tied to a browser-generated key pair.
However, the implementation reuses tokens across all requests regardless of HTTP method, endpoint, or nonce values, and critically, does not enforce identity binding between the two tokens.
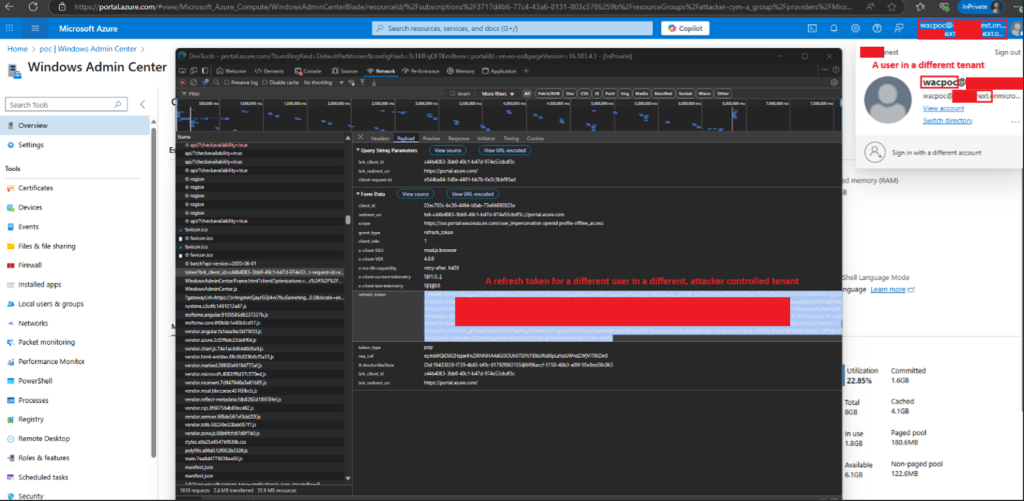
Attackers with local administrator access can dump the WAC API server certificate, impersonate the legitimate service, and harvest privileged users’ WAC.CheckAccess tokens when they connect.
These stolen tokens can then be combined with attacker-forged PoP tokens to execute remote commands on any WAC-managed machine the victim user can access.
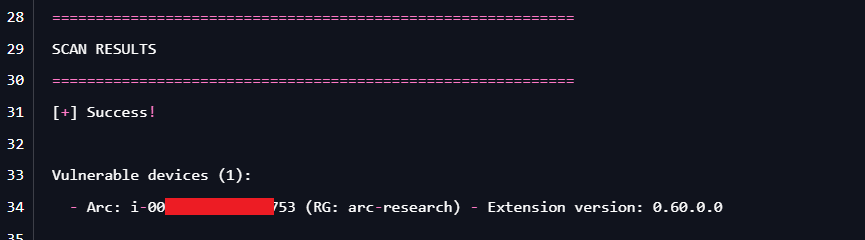
All Azure Virtual Machines and Azure Arc-connected machines running unpatched Windows Admin Center Azure Extension versions below 0.70.00 are vulnerable.
The attack requires local administrator privileges on one compromised machine and a privileged user connecting via Windows Admin Center.
Successful exploitation enables lateral movement across WAC-managed machines, privilege escalation via user impersonation, exfiltration of managed identity credentials, and cross-boundary compromise that breaks Azure resource group and subscription isolation.
Microsoft released the security update on January 13, 2026. Organizations must immediately upgrade to the Windows Admin Center Azure Extension version 0.70.00.
Cymulate’s Exposure Validation platform added a scanning scenario on January 14, 2026, to identify vulnerable deployments.
Defenders should monitor for suspicious virtual accounts created by WAC using the format [email protected], particularly those associated with unknown or external tenant domains.
KQL queries can detect anomalous logon events where AccountName contains “@” but not your organization’s tenant address.
The vulnerability demonstrates how subtle token validation failures can collapse cloud isolation guarantees, allowing attackers to pivot from single-machine compromise to tenant-wide administrative control.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




