In what seems to be a negotiation failure, the LockBit ransomware group decided to go ahead and leak the data it claimed was stolen after the Bank Syariah Indonesia cyber attack.
LockBit made an initial threat on its leak site on May 12, which was tweeted about by researchers. However, on May 15, the group published the data set allegedly from the Bank BSI data breach as surfaced on the group’s website.
The Cyber Express reached out to the Bank BSI group for comment. We are yet to receive any reply from them.
The following screenshot is from the LockBit’s leak site tweeted by a technology security company, Dark Tracer.
Bank Syariah Indonesia cyber attack: How it all began
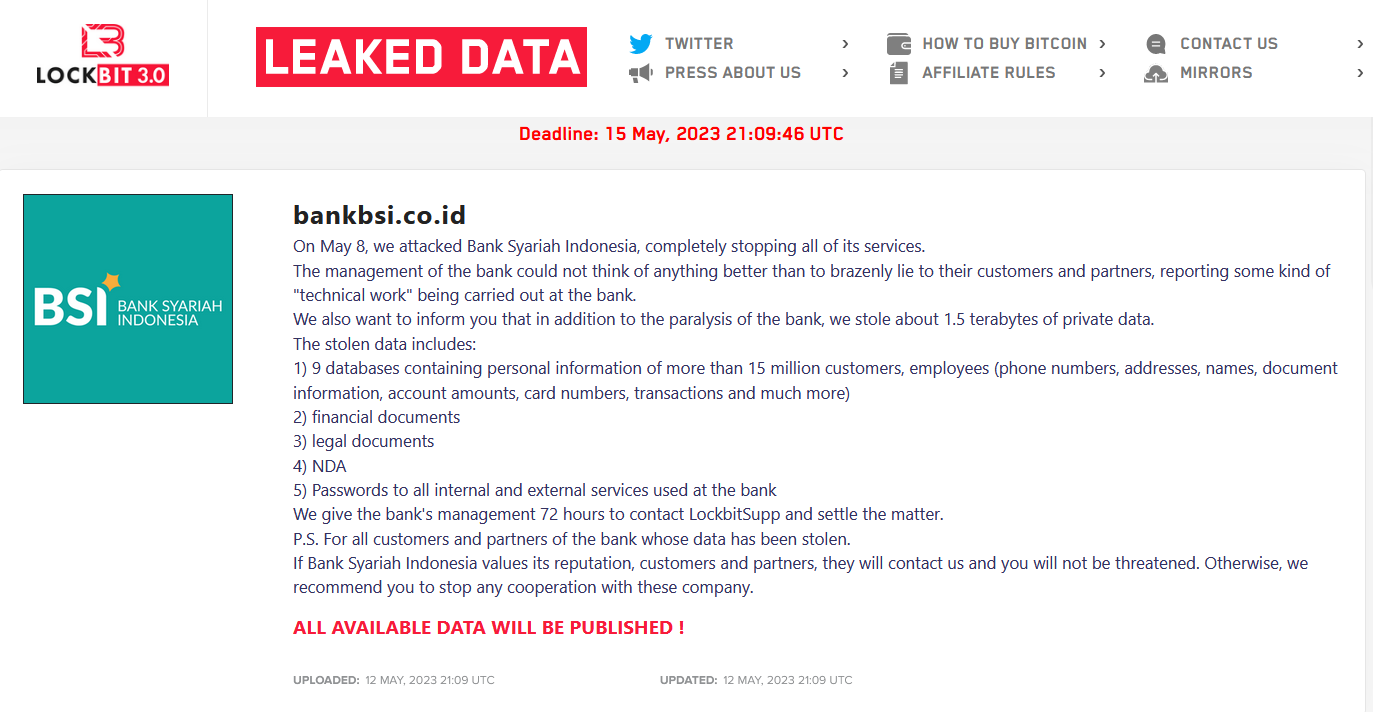
The LockBit ransomware group claimed as shown in the screenshot above, that they launched the Bank Syariah Indonesia cyber attack on May 8.
According to the ransomware group, they were able to completely stop all services after the Bank Syariah Indonesia cyber attack, following which the management ‘lied’ to their customers and partners that it was due to technical work being carried out.
The group claimed to have accessed 1.5 terabytes of confidential data after the Bank Syariah Indonesia cyber attack.
The deadline for making the ransom payment after the Bank Syariah Indonesia cyber attack was set to be 15 May. The group had the following data from the Bank BSI ransomware attack:
- Nine databases of personal information of over 15 million individuals. This included customers and employees.
- Names, phone numbers, addresses, account data, card details, transaction details, etc.
- Legal documents
- NDA
- Passwords of all internal and external services in the bank.
The post concluded with a deadline of 72 hours to make the ransom payment, and “settling the matter.” The ransomware group urged the bank’s customers and partners to stop any cooperation with the company if the ransomware target does not contact them for settlement of the ransom.
On May 16, the LockBit ransomware group posted data claiming to be pilfered after the Bank Syariah Indonesia cyber attack with the following samples:
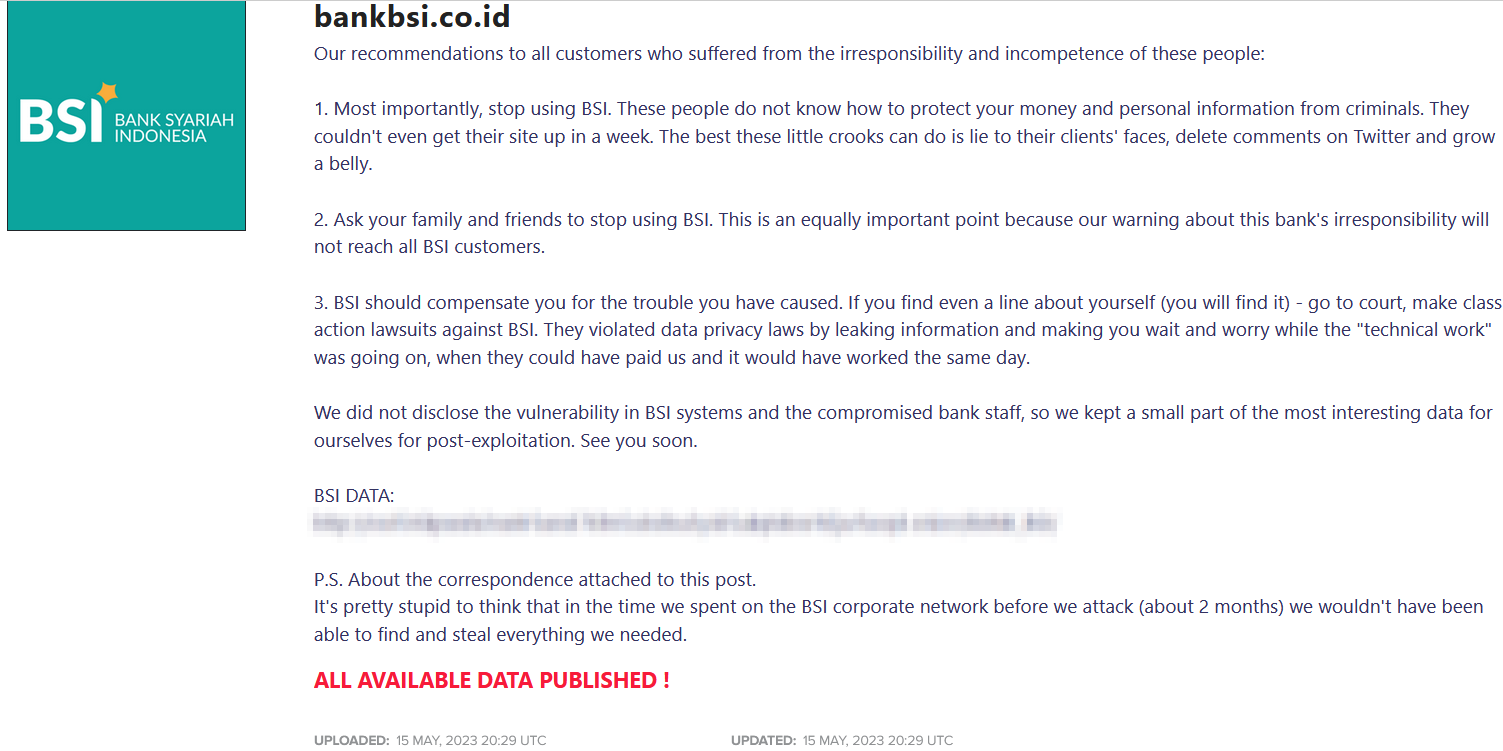
Along side the above data, the ransomware group posted a message to users of Bank BSI likely due to not receiving any ransom from the target.
Dark Tracer tweeted on May 16: “The negotiation period has ended, and the LockBit ransomware group has finally made all the stolen data from Bank Syariah Indonesia public on the dark web.”
LockBit made a rant about Bank BSI not being able to get its systems back to work even after a week of it getting taken down. They claimed that users will find their data leaked after which they should turn to ‘court, and make class action lawsuit.
“We did not disclose the vulnerability in BSI systems and the compromised bank staff, so we kept a small part of the most interesting data for ourselves for post-exploitation,” the Bank BSI data breach post read. This suggests that the group gained access to the systems of the target via a vulnerability.
The group also wrote that they already hacked the systems of Bank BSI two months in advance when they stole all the data.
Bank Syariah Indonesia cyber attack: LockBit shares negotiation chat
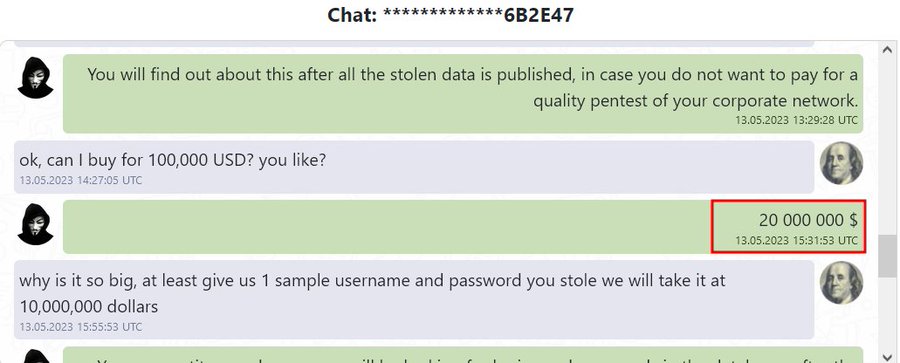
LockBit shared chat history pertaining to the Bank BSI data sale negotiations. A user on Telegram asked to buy the data for 100,000 USD from LockBit. However, the ransomware group demanded $20,000,000.
Hudson Rock’s review of the Bank BSI Systems
Screenshot showing password strength (Photo: Hudson Rock)
Alon Gal, Co-Founder & CTO at Hudson Rock shared details about the lack of cyber hygiene the cybersecurity firm found maintained by the employees of Bank BSI. Further review also confirmed that they did not have an anti-virus in place.
(Photo: Alon Gal/ Hudson Rock)
“I will also point out that the Bank Syariah appears to have a lot of employees who were compromised by info-stealers that had access to sensitive services, and that our data indicates the bank had an overall poor cyber hygiene (weak employee passwords, no anti-viruses installed on employee computers),” the LinkedIn post by Alon concluded.
The LockBit ransomware formerly known as ABCD was found in September 2019. The group maintains its cyberattack in three main stages starting with gaining access via a vulnerability.
Thereafter, the group uses post-exploitation tools, increases privileges, and completes its task after disabling security on the targeted machines.