BBTok is a banking malware first identified in 2020 and it primarily targets users in Latin America (particularly Mexico and Brazil).
It employs sophisticated tactics like phishing emails that lead to the download of malicious files, which can replicate the interfaces of over 40 banks.

GDataSoftware researchers recently discovered that BBTok banking malware had been actively attacking organizations using PowerShell, Python, and Idlib.
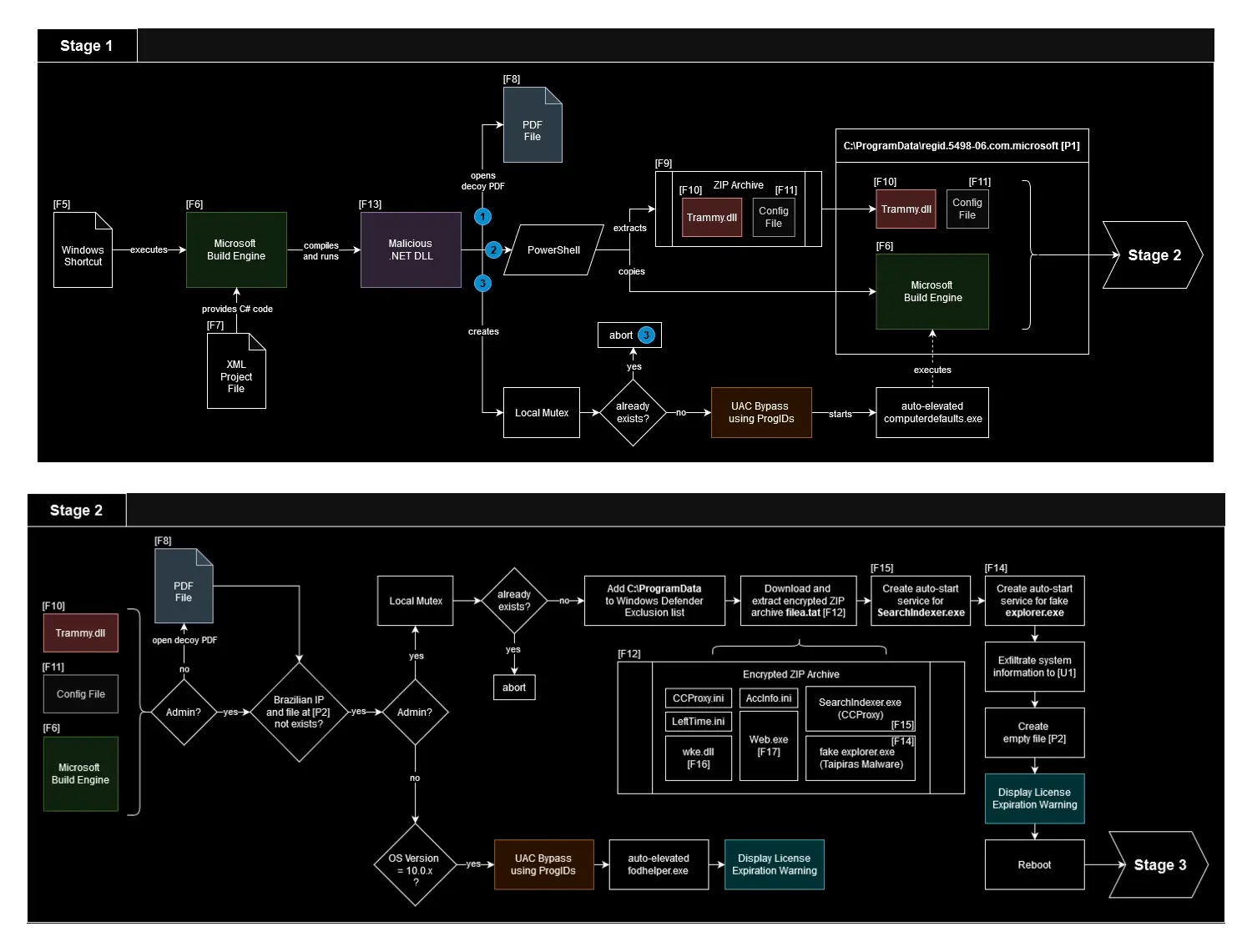
This sophisticated malware begins its infection chain via an email-delivered ‘ISO image,’ targeting ‘Brazilian entities.
‘The ‘ISO’ contains a “Windows shortcut (LNK) file” disguised as a “PDF invoice (DANFE).”

To compile malicious ‘C#’ code on the machine of the victim, this executes the Microsoft Build Engine (“MSBuild.exe”).
The resulting ‘.NET DLL’ employs a ‘UAC bypass’ using “ProgIDs” and “computerdefaults.exe” to run “Trammy.dll,” which is an obfuscated loader.
Trammy.dll utilizes AppDomain Manager Injection, and it’s a technique that executes malicious code by overriding the “InitializeNewDomain()” method.
The loader is obfuscated with a “ConfuserEx variant,” which requires a multi-step deobfuscation process.
Now, retrieving encoded strings involves tools like “NoFuserEx,” “de4dot-cex,” and “custom scripts.”
Leveraging AI for enhanced security => Free Webinar
On the infected machines, the malware writes obfuscated log files, and this necessitates an interpretation table for incident responders.
The GDataSoftware report states that this complete attack chain illustrates the advanced evasion techniques that were found leveraging legitimate Windows components and complex obfuscation methods.
All these methods were exploited to make the analysis and detection more challenging and complicated.
Trammy.dll initiates its execution through the InitializeNewDomain() method in SacApp.SacApp, having been designated as the AppDomainManager in the configuration.
It first opens a decoy PDF file, and then verifies two conditions before proceeding, “absence of a specific file (C:ProgramDatainternal_drive_version2.3.4.txt),” and “confirmation of a Brazilian IP address.”The malware logs its activities in “C:ProgramDatalog.txt,” using keywords like “START” and “ADMIN” to indicate progress.
It collects system information via “WMI,” and send the data to a “remote server.”
While it collects the following information:-
- OSVersion
- CSName
- Caption
- Version
- SerialNumber
- BuildNumber
- OsArchitecture
For persistence, it downloads and installs CCProxy, masquerading it as “Searchlndexer.exe” (note the lowercase ‘L’), and sets up a service for a Delphi-compiled payload (explorer.exe).CCProxy is configured to accept HTTP connections on localhost:8118, serving to disguise communication with the command and control (C2) server.
The malware also adds C:ProgramData to Windows Defender’s exclusions. After establishing persistence, it creates the previously checked file to prevent re-execution, displays a Windows license expiration warning, and reboots the system.
Upon restart, the CCProxy and Delphi payload activate, with the latter communicating with the C2 server through CCProxy using the Realthinclient SDK.
Free Webinar on How to Protect Small Businesses Against Advanced Cyberthreats -> Free Webinar