What a round! 29 teams from 22 countries blitzed in to decide who would reach the next stage of this year’s Ambassador World Cup. The results have been groundbreaking for both hackers and customers. For reference, 673 hackers have joined the fray to bring home gold and secure the internet in this global competition.
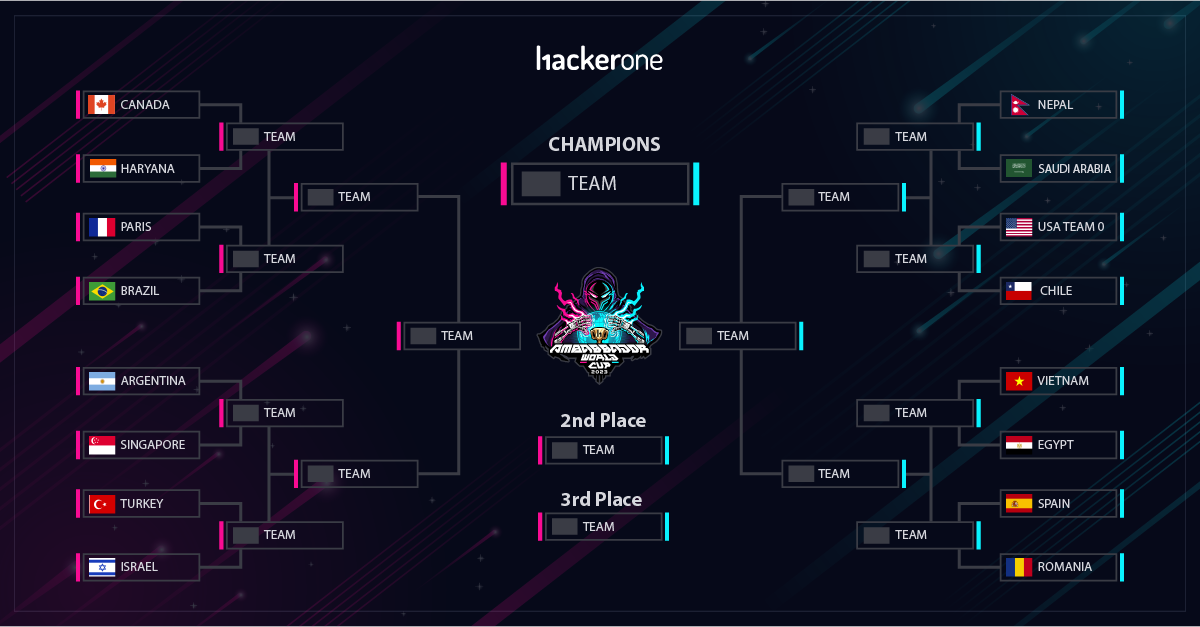
The initial group stage was drafted live with the ambassadors before the scope call. Take a look at the group stage layout below:
Discord channels have been on fire, with teams providing recon hand-offs, playing off the skills of fellow teammates, and assisting each other to score high-severity bugs! The amount of hackers joining from across the globe for this event shows what our community is all about. Regardless of the outcome, each individual played a role in making this event possible.
The programs that have joined in Round One are seeing real results, too!
“OpenSea gains so much valuable insight by working closely with the security research community. The Ambassador World Cup has increased the size and scale of this community tremendously, and we’re grateful for the ability it’s given us to improve our security practices and help make our products more secure.”
<< Cory Hardman, OpenSea's Head of Security
 [Competitors from Ireland, Romania, and Nepal hacking together]
[Competitors from Ireland, Romania, and Nepal hacking together]
During Round One of the Ambassador World Cup, 239 hackers worldwide submitted reports, identifying 262 valid bugs. As a result, over $515K has been paid to researchers thus far, with 170 bounties awarded. These remarkable achievements illustrate the exceptional talent and dedication of the participating hackers. It’s important to note that these results are just a snapshot and are likely to increase!
Congrats to all the participating programs on some incredible results. There is excitement all around about the value these programs are seeing. Check out what Shopify had to share about their success in Round One:
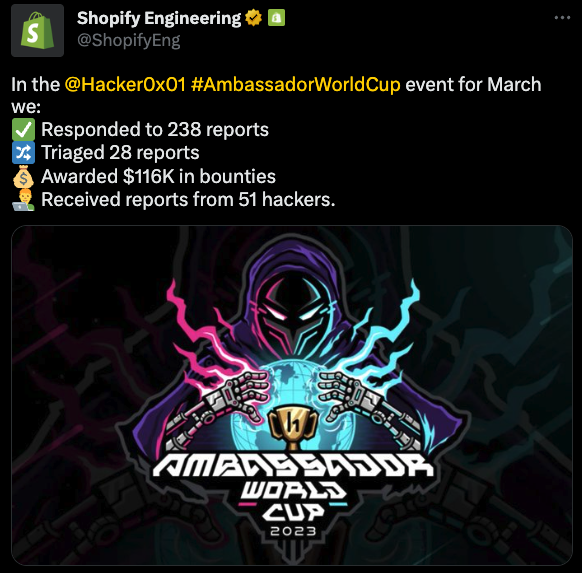
[Tweet from Shopify Engineering]
So, let’s dig into the action. We want to give it up to the following hackers for making major moves in this first round. These hackers went above and beyond to create waves. Here are some of our top players and their remarks about this round.
cdl >>
“The Ambassador World Cup gave me a reason to hack on OpenSea again after taking time off. This led to me finding three critical vulnerabilities during the event and then another critical after the event had ended!“
rhynorater >>
“The AWC was a great opportunity to collaborate with hackers in the community and focus on some different targets. The competition factor is always a great motivator and serves to keep everyone really engaged.“
0xbeefed >>
“I have limited hunting availability due to a full-time job, but this year’s event allowed me to dive into the Epic Games program. The participation witnessed for this year’s AWC was exceptional, with programs receiving hundreds of reports and supporting their already hardened scopes. Events like these increase competition among us hackers and inspire us to discover more intricate vulnerabilities.“
Every individual who participates in this event carries forward the message that hackers are here for good. We want to thank everyone who worked to surpass their limits and break records with this first round.
Now, we want to honor those who aren’t going to be with us in the next round. You’ve all put in an effort you should be proud of. You have collaborated to collect new members, helped educate each other, and brought the best out of your community. Here’s to the teams leaving but not forgotten!
Bordeaux (France)
Finland
Pakistan
Jaipur (India)
Nigeria
Pune (India)
Ireland
New Delhi (India)
Bangladesh
Kenya
Odisha (India)
Bangalore (India)
USA Team 1
We want to make a special mention to the Bordeaux team from France, champions of the 2022 Ambassador World Cup. Despite being in a group packed with heavy-hitting talent, they did amazingly well. For this group, it came down to the very wire. A single bug was the deciding factor. We will miss our former champs in the next round; here’s to an incredible showing!
Don’t worry; there’s always next year– so remember your rivals and get ready to square off again!
We witnessed some incredible performances and uncovered impactful vulnerabilities in participating customer programs, all thanks to the outstanding work of the participating hackers. That said, it’s time to gear up for the next round – the Sweet Sixteen! As the name implies, sixteen teams are moving forward to face their next competitors. Of course, the stakes are higher, and the competition is tougher, but we know these teams are up for the challenge. We will be announcing the programs for the next stage soon. The Sweet Sixteen will take the field on May 2nd for the next round. See the competitors moving forward in the brackets below!