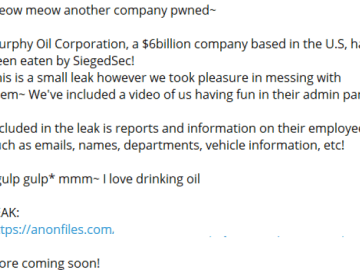
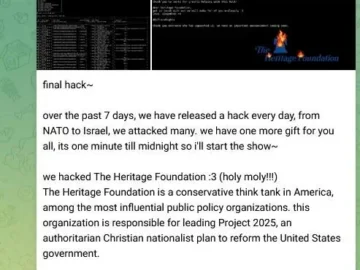
When a CEO’s deepfake appears in a fraudulent investor call, when stolen credentials surface on dark web marketplaces, or when executive impersonation attempts trick employees into wire transfers, the damage isn’t just technical—it’s existential. Yet most organizations treat executive protection as an afterthought, if they think about it at all.
Here’s the uncomfortable reality; your executives aren’t just high-value employees. They’re walking attack vectors. Their social media presence, their public speaking engagements, their digital footprints across platforms—all of it creates opportunities for threat actors. And unlike technical vulnerabilities that can be patched, executive exposure is permanent, cumulative, and growing by the day.
Executives understand visibility as a business necessity for leadership, brand building, and investor confidence. What they often lack is executive security intelligence that shows how attackers weaponize that visibility.
The question isn’t whether your leadership team needs executive monitoring. It’s whether you can afford not to have it.


The Executive Blind Spot Nobody Talks About
Traditional security frameworks focus on perimeter defense, endpoint protection, and network monitoring. Executive monitoring exists in a different dimension entirely—one that bridges digital risk, physical security, and reputational management in ways most security teams aren’t equipped to handle.
Consider what attackers see when they target executives: comprehensive LinkedIn profiles detailing career histories and professional networks, conference schedules announcing travel plans weeks in advance, published interviews revealing decision-making processes and strategic priorities, social media posts exposing family members and personal interests, and professional email addresses easily harvested for spear-phishing campaigns. This isn’t reconnaissance requiring sophisticated hacking. It’s open-source intelligence gathering anyone can perform in an afternoon.


The real vulnerability is that executives themselves rarely understand their exposure. They view public visibility as part of the job—necessary for thought leadership, investor relations, and business development. They’re not wrong. But they’re also not thinking like attackers.
Why Executive Threats Are Business Continuity Issues
A compromised server gets fixed. A breached database gets contained. But when executives become attack targets, the damage radiates through the organization in ways that don’t show up in incident reports.
Business email compromise attacks targeting executives cost organizations an average of $4.1 million per incident. That’s not counting the reputational damage, the eroded stakeholder trust, or the board-level questions about why leadership wasn’t better protected. Deepfake technology has matured to the point where realistic video and audio impersonations can be generated in hours, not days. When a fake CEO video circulates making false claims about company performance, markets react before PR teams can even draft responses.
Executive credential leaks create cascading risks. Unlike typical employee accounts, executive credentials often have elevated privileges, access to sensitive strategic information, and the authority to approve high-value transactions. A single compromised executive account can become the fulcrum for devastating attacks.
This is where standard security tools fall short. They protect infrastructure—but they don’t deliver real-time executive protection. They don’t monitor the dark web for leaked executive credentials, track impersonation accounts on social platforms, or identify deepfakes before they go viral.
That gap is precisely what executive monitoring solutions are designed to fill.
Interested in exploring how executive monitoring can strengthen your leadership protection and enable strategic growth? Learn more about comprehensive executive threat intelligence solutions at Cyble.com.
The Growth Multiplier Effect
Here’s the business case that gets overlooked in security discussions; executive monitoring doesn’t just prevent damage—it enables growth.
When leaders can engage publicly with confidence, thought leadership accelerates. When executives travel internationally backed by executive protection services, deal-making and partnerships move faster. When boards know that leadership exposure is continuously monitored, governance concerns diminish and strategic focus increases.
Organizations with robust executive monitoring platforms demonstrate operational maturity that resonates with investors, partners, and enterprise clients. It signals that security isn’t just an IT function—it’s embedded in how the business operates at the highest levels. For companies pursuing M&A activity, executive protection becomes due diligence table stakes. Acquiring companies want assurance that leadership teams come without hidden security liabilities.
The velocity of business decisions improves when executives aren’t second-guessing their digital exposure. Strategic communications happen more freely. Competitive intelligence can be gathered more aggressively. Innovation discussions occur with less fear of leakage.
What Effective Executive Monitoring Actually Looks Like
The difference between security theater and genuine protection is specificity. Generic threat intelligence doesn’t translate to executive protection. What matters is real-time monitoring across the specific vectors where executive threats emerge.
Effective platforms monitor dark web forums and cybercrime marketplaces for executive PII leaks, tracking when credentials, personal data, or sensitive information surfaces in underground channels. They deploy AI-driven deepfake detection across social media and video platforms, identifying manipulated content before it gains distribution. Social media impersonation tracking identifies fake accounts masquerading as executives, often used for business email compromise setup. Compromised credential monitoring alerts when executive email addresses or passwords appear in breach databases, enabling immediate password resets before exploitation.
The challenge is scale and speed. Manual monitoring can’t keep pace with how quickly threats emerge and spread. By the time a security analyst discovers an executive impersonation account, it may have already been used to contact employees or partners.
This is where platforms like Cyble’s Executive Monitoring solution demonstrate the value of automation paired with human expertise. Cyble delivers real-time executive protection across the surface web, deep web, and dark web. The platform combines real-time alerts delivered via email, SMS, or WhatsApp with AI-powered threat detection that identifies deepfakes, impersonations, and credential leaks across surface web, deep web, and dark web sources. It provides unified dashboard visibility that consolidates executive threats into a single view rather than fragmenting them across multiple tools, and integrates physical security intelligence for executives traveling to high-risk locations with contextualized threat assessments.
What separates effective solutions from basic monitoring is context. Alerting about every potential threat creates noise. Understanding which threats pose genuine risk to specific executives based on their role, public profile, and current activities—that’s intelligence.
Cyble’s approach emphasizes actionable insights over data dumps. When an executive’s credentials appear in a breach, the platform doesn’t just alert—it provides context about the source, potential impact, and recommended response actions. When deepfakes are detected, automated takedown processes can be initiated, removing fraudulent content before it spreads widely.
Also read: How Cyble is Leading the Fight Against Deepfakes with Real-Time Detection & Takedowns
Instead of flooding teams with noise, Cyble provides insight into severity, relevance, and recommended actions—turning raw data into Executive Security Intelligence.
The ROI Nobody Calculates
Traditional security investments justify themselves through prevented breaches and avoided downtime. Executive monitoring ROI is harder to quantify precisely because it’s impossible to measure attacks that never happened due to deterrence and early intervention.
But consider the inverse calculation: what’s the cost of not having it? A single successful executive impersonation attack costs millions. A leaked executive credential that enables a broader breach amplifies damage exponentially. A deepfake crisis that damages brand reputation takes years to repair. The question shifts from “can we justify the investment” to “can we justify the exposure.”
Organizations serious about growth recognize that executive security is growth infrastructure, not a cost center. It’s the same logic that drives investments in executive coaching, strategic advisors, and leadership development. You’re protecting and amplifying the most valuable assets in the organization—the people making decisions.
Building Protection That Scales With Ambition
The final insight that separates mature organizations from reactive ones is that executive monitoring isn’t static. As companies grow, executive profiles rise. As leadership becomes more publicly visible, attack surfaces expand. As strategic importance increases, threat actor interest intensifies. Effective senior executive threat protection must scale alongside ambition.
Scalable executive protection means platforms that grow with organizational complexity, handling increased numbers of monitored executives as leadership teams expand. They adapt to evolving threat vectors, continuously updating detection capabilities as attack techniques mature. They integrate with existing security infrastructure rather than creating isolated silos, and provide graduated protection levels matching executive risk profiles rather than one-size-fits-all approaches.
This requires platforms built on threat intelligence foundations, not bolt-on features added to existing security suites. Cyble’s Executive Monitoring exists within a broader threat intelligence ecosystem that includes dark web monitoring, brand protection, and attack surface management. This integration means executive threats aren’t isolated signals—they’re correlated with broader organizational risk patterns.
When an executive’s name appears in dark web discussions alongside mentions of your company’s infrastructure, that correlation matters. When brand impersonation campaigns coincide with executive travel to specific regions, that context informs protective measures.
The Strategic Imperative
Executive monitoring represents a fundamental shift in how organizations think about security. It acknowledges that protecting infrastructure isn’t enough when people are targets. It recognizes that reputational risk and operational risk intertwine at the leadership level. It accepts that digital threats demand digital surveillance, not just digital defenses.
For organizations pursuing growth, executive protection isn’t optional anymore. It’s foundational. The businesses that will dominate their markets in the coming decade aren’t just those with the best products or strongest financials—they’re the ones whose leadership can operate with confidence, visibility, and strategic aggression because their digital exposure is being actively managed.
The threat landscape has evolved. Executive protection must evolve with it. The question is whether your organization will adapt proactively or learn these lessons the expensive way.
Interested in exploring how executive monitoring can strengthen your leadership protection and enable strategic growth? Learn more about comprehensive executive threat intelligence solutions at Cyble.com.