Email hacking and fraud have become common these days. Cybercriminals can easily break into and take control of mail accounts if they are not protected.
They can do so through phishing attacks, vulnerable apps, and data breaches. Globally, people send about 347.3 billion emails daily, all of which carry sensitive data.
Online criminals send about 3.4 billion phishing emails daily, using many tricks to make them look genuine. Conducting best practices for email security headers can help increase your cyber defenses. You need to be aware of the attacks you are dealing with. Create awareness within your team and manage passwords well.
Email security headers consist of parts that you cannot see. These hidden parts feature crucial data that authenticates and identifies messages. They are essential parts of protocol since they provide safety against attacks.
Security headers tell about where the message is coming from and its integrity. Implementing email security best practices ensures your data does not leak through emails. Your team benefits from real-time defense.
You prevent fraud that could impact your organization. Cyber attackers seek to control your email communication in all ways. Email security best practices can prevent and control attacks. Different strategies can help organizations keep their mail communication safe.
Encrypt Emails
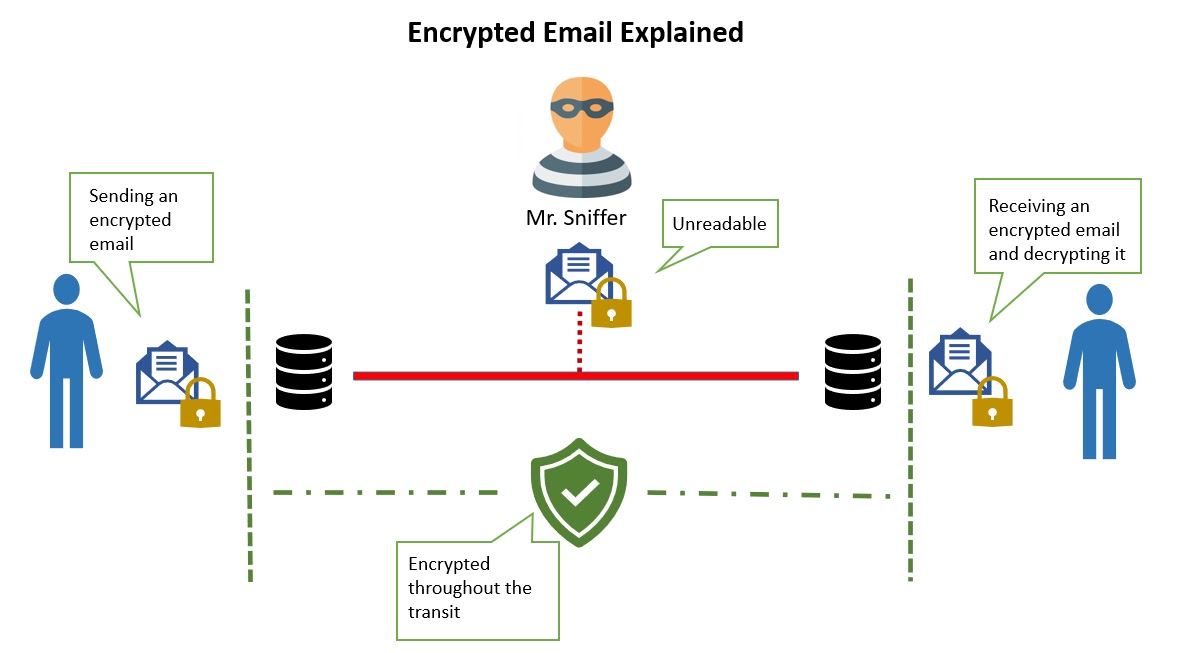
Encrypting mail is a type of authentication that prevents unauthorized people from reading your mail during delivery. To understand what does encrypting an email mean, think about how a disguised or coded message would look like.
Encryption converts the message into an illegible text. Even if a cyber attacker accessed it, it would be of no use to them. Anyone who uses mail communication should know how to encrypt email.
It is especially important when sending sensitive mails. Different email programs require different encryption methods. It is necessary to know how to encrypt email in each. Understand how to send an encrypted email in Yahoo and how to encrypt an email in Gmail.
You may encrypt emails directly on a mail program or use encryption software. When you are encrypting in the program, compose the mail first. Once done, change the security settings and select encrypted content and attachments.
If you want to use third-party software, create the settings during installation. There are many types of encryption software you can choose from. Be keen on the safety of the software before using it.
Understand the email threats you are dealing with
Every time you send or receive mail, you face different threats. Research shows that cyberattacks have increased threefold since 2020. Individuals and organizations need to know the types of common attacks.
This way, they can implement the best practices for securing mail. The most common threats include the following.
Phishing threats. Online criminals send about 3.4 billion phishing emails daily. They aim to steal your data.
Malspam threats. These are spam mails that contain malware. Cybercriminals add links or attachments to them. The latest data shows criminals send about 162 million spam mails daily.
Spoofing. Online criminals send emails with features that make them look genuine. The available spoofing attack data show about 30,000 attacks happen daily.
Ransomware threats. Cybercriminals encrypt your emails, making them impossible to read. Then, they demand a ransom to remove the encryption. Data shows that ransomware attacks in 2024 will stand at 37,700 attacks per hour. In a day, organizations can cumulatively receive over 900,000 attacks daily.
Conduct Password Management Best Practices
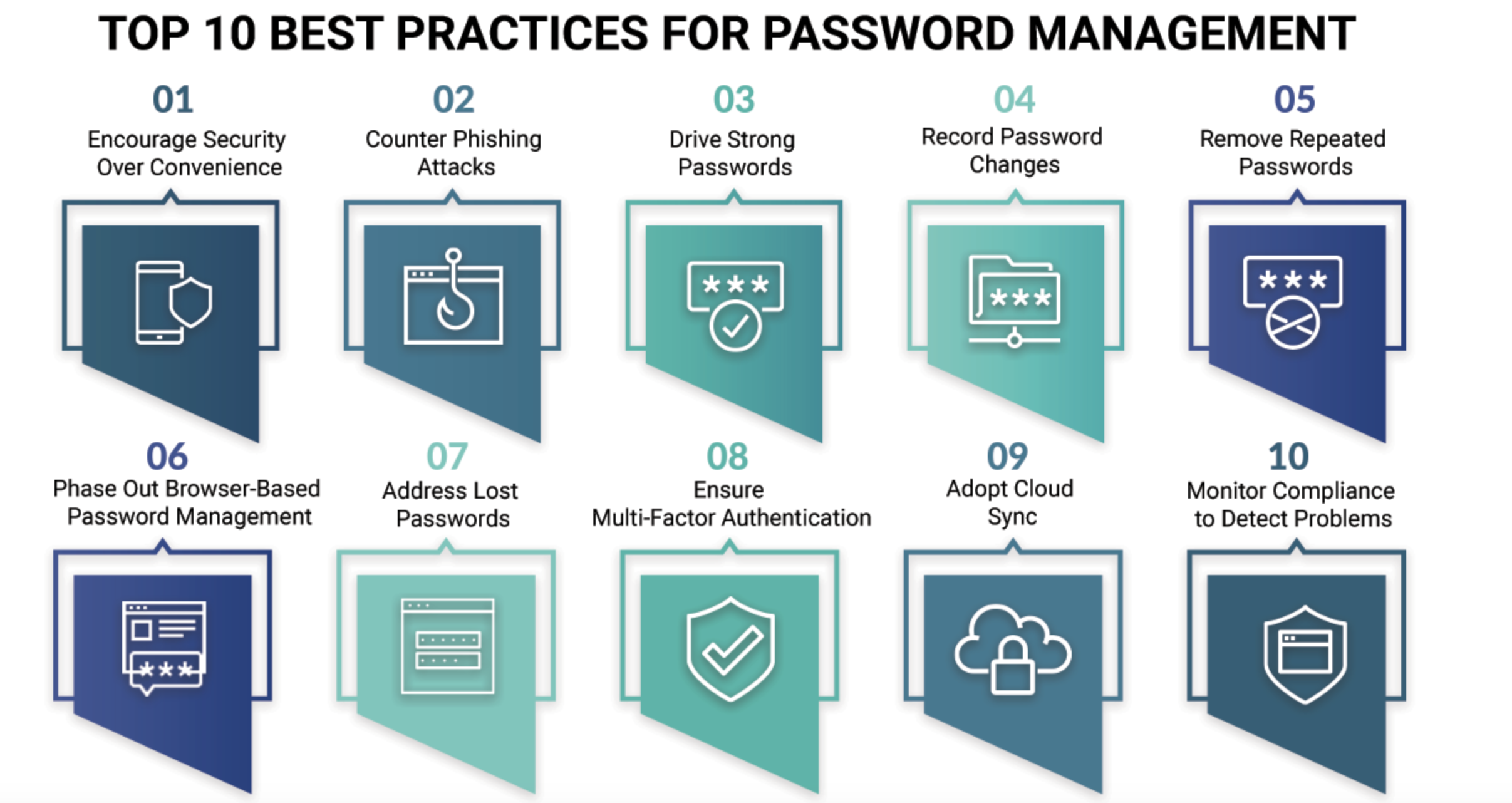
Password management is a practice that ensures you create, store, and use your passwords safely. It aims to boost the usability and safety of passwords. Users must use different mail protection tips.
This helps them create unique and complex login data. They also need to use methods that make it easier to remember the login data. There are different email protection tips for this.
● Use password management software. They are apps that help manage all login data in one place.
● Let the login information be complex. Create passwords that are complex yet easy to remember.
● Avoid sharing passwords. Do not share your logins with people unless very necessary.
● Add an authentication layer. Have an extra security layer by using two-factor authentication.
Conduct employee training
Employee training should be prioritized in every organization. Training provides workers with knowledge about email security. This helps them keep the system secure and prevent attacks. Training allows them to know the potential threats that exist. They learn how to prevent and identify them. Different strategies can help with worker training on securing mail.
● Train them about their role in security and the common threats.
● Create a culture of quick reporting of any suspicion. Take action when a report is done and recognize the person.
● Create a phishing scenario by phishing workers. It can help test decide if they understand how phishing occurs.
● Provide support by ensuring employees have all the tools they need for safe communication.
● Measure progress and monitor the training’s success.
Implement authentication protocols
Email authentication protocols are behind-the-scenes activities that improve security. They ensure all outgoing and incoming mail is safe. They are types of secure email security header verification methods. Authentication protocols ensure the email is from the right source. The protocols may block some mails or send them to the spam folder if they look suspicious. Here are the different authentication protocols you can use.
SPF (Sender Policy Framework): SPF allows organizations to create a list of approved IP addresses. Mail from a different IP address fails the authentication test.
DKIM (Domain Keys Identified Mail): DKIM adds digital header signatures. Receiving servers use signatures to verify that the mail is authentic.
TLS (Transport Layer Security): TLS encrypts email to ensure it is safe during delivery.
DMARC (Domain Message Authentication Reporting and Conformance): DMARC uses SPF and DNS to verify if email senders are genuine. It is a good strategy to prevent hackers from using spoofing.
Add brand logo to emails
Logo branding is important for increasing user trust. Logos show a higher level of professionalism and increase email open rates. Emails with a verified logo make it easier for recipients to identify the sender. It minimizes the chances of opening phishing and malware emails. When recipients feel confident with a brand, most will open their emails.
The brand gains high online traffic, which increases ROI. Brands need to maintain logo consistency in their mail structure. You may add the logo in the email header, footer, or sender ID photo. A good email signature should offer an excellent logo design. You need to get the colors, letters, and symbols right.
It must include all important but relevant information. These may include email, telephone, and contact person. Add a call to action to direct recipients on what to do if they need help. Create and add useful links. They can be links to click to make orders, book, or visit the online store/catalog.
Implement Defenses
Email defenses are actions that help keep your system and emails safe. They are actions that go beyond passwords, email protocols, and training. They protect not only emails but the entire system from breaches. Implementing defenses significantly minimizes the chances of threats. The important defense activities may include the following.
● Create mail backups for all sensitive mail communication.
● Activate anti-malware and anti-spam filters
● Monitor all mail accounts closely and test for security from time to time.
● Install antivirus and online security software.
Conclusion
Implementation of mail security helps protect you from unauthorized access. Protection measures include email encryption and the use of email authentication protocols. Provide email security training to workers and offer them the tools they need for protection. Understand the types of threats you are dealing with and how to prevent them. The entire organization should use the best password management practices.
