A recent investigation unveiled a trend of fake trading apps on Google Play and the App Store designed to trick unsuspecting users out of their hard-earned money.
This article delves into the mechanics of these scams, highlighting the urgent need for vigilance among digital finance users.
Surge in Pig-Butchering Scam
The term “pig-butchering scam” might sound peculiar, but its implications are far from benign.
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox:
Originating in Southeast Asia, this scam involves fattening the pig (the victim) by building a relationship and trust over time, only to slaughter it financially in the end.
India has witnessed a significant surge in such scams, with cybercriminals deploying sophisticated social engineering tactics to lure victims into their traps.

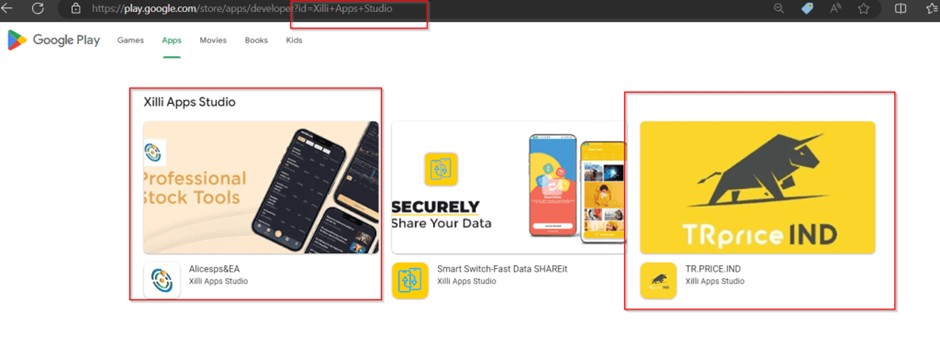
A startling revelation in the investigation is the compromise of legitimate developer accounts on popular app stores.
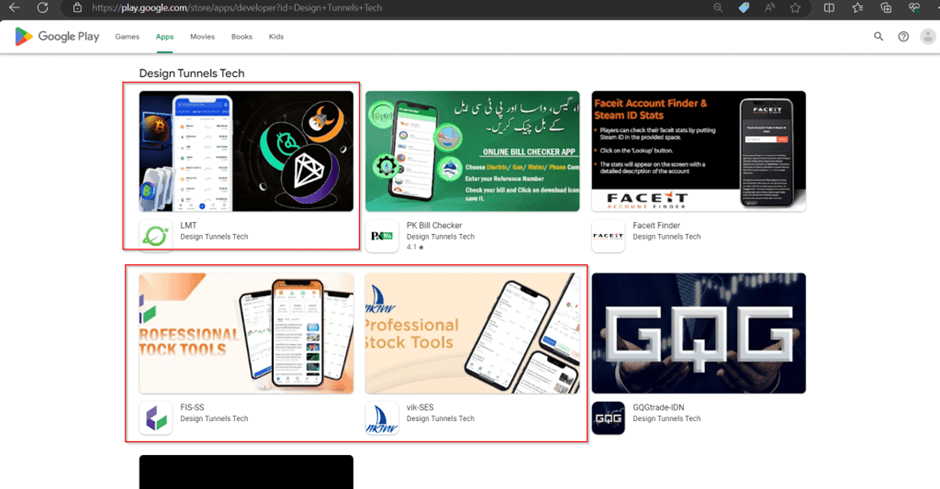
Cybercriminals have infiltrated these accounts, using them as a launchpad to publish malicious trading apps.
This breach undermines the security protocols of major app stores and puts countless users at risk of financial theft.
Counterfeit Trading Applications
The core of this scam lies in counterfeit trading applications meticulously designed to mimic legitimate ones.
These apps offer enticing features and promises of high returns, drawing users into a web of deceit.
Once installed, they serve as conduits for financial and personal data theft, leading to substantial monetary losses for the victims.
Cyble Research and Intelligence Labs (CRIL) has observed a noteworthy surge in pig-butchering scams targeting Indian investors who want to profit from the stock market.
Adding a layer of authenticity to their scheme, scammers have resorted to creating fabricated articles and news stories.
These pieces often feature fake endorsements from celebrities or reputed financial experts, further misleading potential victims.
The sophistication of these articles makes it increasingly difficult for users to distinguish between legitimate and fraudulent sources.

The digital finance landscape is fraught with risks, underscored by the alarming rise in fake trading apps and pig-butchering scams.
Users must exercise utmost caution, verifying the legitimacy of any app before downloading and refraining from sharing personal or financial information online.
It’s imperative for app stores to enhance their security measures and for authorities to take decisive action against these cybercriminals.
In the meantime, awareness and vigilance are the best defenses against these digital predators.
IOCs
| Indicators | Indicator Type |
| faf7a001250ef1dbd2d6eaf8eabbd8d589c0960e871325808a7a1a76619c4b4f 87196e5cda572d63c43d52df200e823a9811e33a ecce84056298bc3bcc8c17d6ed12a29b |
SHA256 SHA1 MD5 |
| app[.]panth-ss[.]vip | Domain |
| 0a2fffb84d58dbf3cb2a50fd15d3cda9b3998c85c0424e29bf0964cc6bbda920 2288add2292e026cb32933943d2c9f105e57ed8d a522af373e24042e4b1995a186cfed6a |
SHA256 SHA1 MD5 |
| app[.]yongljt[.]com | Domain |
| 52c36d2e1c5df64b96e017625fdd2d1c07e2a0b741c155735d09c068b23d54ad 53c40428b48050ecd851f58b020629f58b6bd18f e1b935f23c49ac0b1176c3b650e5bc12 |
SHA256 SHA1 MD5 |
| hxxps://www[.]inueyd[.]com/?v=3 | Domain |
| Giottusmh[.]com giottusmk[.]com |
Domain |
| 34.131.1[.]213 | IP |
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
