BIOS/UEFI vulnerabilities in the iSeq 100 DNA sequencer from U.S. biotechnology company Illumina could let attackers disable devices used for detecting illnesses and developing vaccines.
The Illumina iSeq 100 is advertised as a DNA sequencing system that medical and research labs can use to deliver “rapid and cost-effective genetic analysis.”
Firmware security company Eclypsium analyzed the BIOS firmware in Illumina’s device and discovered that it booted without the standard write protections, leaving it open to overwrites that could “brick” the system or place implants for long-term persistence.
Old and vulnerable BIOS
The researchers found that iSeq 100 was running an outdated version of the BIOS firmware that ran in Compatibility Support Mode (CSM) to support older devices and was not protected through Secure Boot technology.
Eclypsium’s analysis identified five major issues that allowed the exploitation of nine vulnerabilities with high and medium severity scores, one as old as 2017.
Besides missing BIOS write protections, the iSeq 100 device was also vulnerable to LogoFAIL, Spectre 2, and Microarchitectural Data Sampling (MDS) attacks.
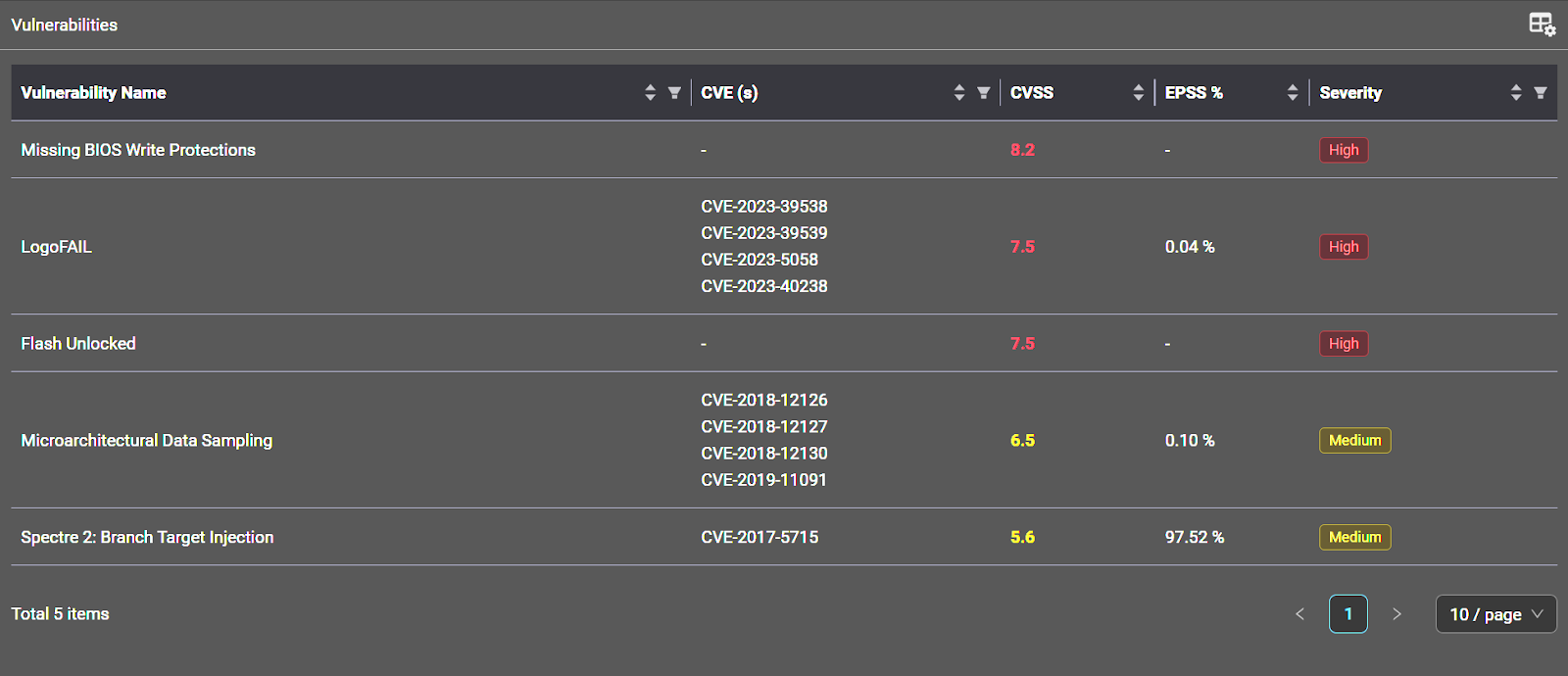
source: Eclypsium
Although booting in CSM mode permits legacy device support, it is not recommended for sensitive devices, especially if they are of a newer generation.
The researchers found that the vulnerable BIOS (B480AM12 – 04/12/2018) on iSeq 100 did not have firmware protections enabled, which allowed modifying the code for booting the device.
Combined with the lack of Secure Boot, which checks the validity and integrity of the boot code, any malicious change would remain undetected.
In a report today, Eclypsium underlines that their analysis “analysis was limited specifically to the iSeq 100 sequencer device” and that similar issues may be present in other medical or industrial devices.
The researchers explain that medical device manufacturers use outside suppliers for the computing power of the system. In the case of iSeq 100, the device relies on an OEM motherboard from IEI Integration Corp.
Since IEI Integration Corp develops multiple industrial computer products and is an Original Design Manufacturer (ODM) for medical devices, Eclypsium says that “it would be highly likely that these or similar issues could be found either in other medical or industrial devices that use IEI motherboards.”
The researchers also explain that an attacker that already compromised a device could leverage the vulnerabilities to modify the firmware to either brick the system. A threat actor with the necessary knowledge could also tamper with the test results.
“If the data is manipulated by an implant/backdoor in these devices, then a threat actor may manipulate a wide range of outcomes including faking presence or absence of hereditary conditions, manipulating medical treatments or new vaccines, faking ancestry DNA research, etc.” – Eclypsium
Eclypsium notified Illumina of the BIOS problems in iSeq 100 devices and the biotechnology company informed them that it issued a patch to affected customers.
BleepingComputer reached out to Illumina for a comment on the delivery method for the fix and an estimation of the number of iSeq 100 systems that should receive it.
A spokesperson for the company said that Illumina is following its “standard processes and will notify impacted customers if any mitigations are required.”
“Our initial evaluation indicates these issues are not high-risk,” an Illumina representative told BleepingComputer.
“Illumina is committed to the security of our products and to privacy of genomic data and we have established oversight and accountability processes, including security best practices for the development and deployment of our products.
“As part of this commitment, we are always working to improve how we deliver security updates for instruments in the field,” reads the rest of the statement.
In their report, Eclypsium’s researchers warn that a threat actor that can overwrite the firmware on iSeq 100 could “easily disable the device.”
Disrupting the business by taking out high-value systems is exactly what ransomware actors are after since their goal is to determine the victim to pay the ransom by making its recovery efforts as difficult as possible.
Apart from financially motivated attackers, Eclypsium says that state actors could also find DNA sequencing systems appealing because they “are critical to detecting genetic illnesses, cancers, identifying drug-resistant bacteria, and for the production of vaccines.”
In 2023, the Cybersecurity Infrastructure Security Agency (CISA) and the Food and Drug Administration (FDA) in the U.S. released an urgent advisory about two vulnerabilities in Illumina’s Universal Copy Service (UCS) that is present in multiple products used by medical facilities and laboratories across the world.
One of the issues (CVE-2023-1968) received the maximum severity score while the other (CVE-2023-1966) had a high severity rating. Illumina reacted at the time by providing updates and instructions on how to mitigate the security problems.





