Bitwarden’s credentials autofill feature contains a risky behavior that could allow malicious iframes embedded in trusted websites to steal people’s credentials and send them to an attacker.
The issue was reported by analysts at Flashpoint, who said Bitwarden first learned of the problem in 2018 but chose to allow it to accommodate legitimate sites that use iframes.
Although the auto-fill feature is disabled on Bitwarden by default, and the conditions to exploit it aren’t abundant, Flashpoint says there are still websites that meet the requirements where motivated threat actors can attempt to exploit these flaws.
(Un)conditional auto-fill
Bitwarden is a popular open-source password management service with a web browser extension that stores secrets like account usernames and passwords in an encrypted vault.
When its users visit a website, the extension detects if there’s a stored login for that domain and offers to fill in the credentials. If the auto-fill option is enabled, it fills them automatically upon the page load without the user having to do anything.
While analyzing Bitwarden, Flashpoint’s researchers discovered that the extension also auto-fills forms defined in embedded iframes, even those from external domains.
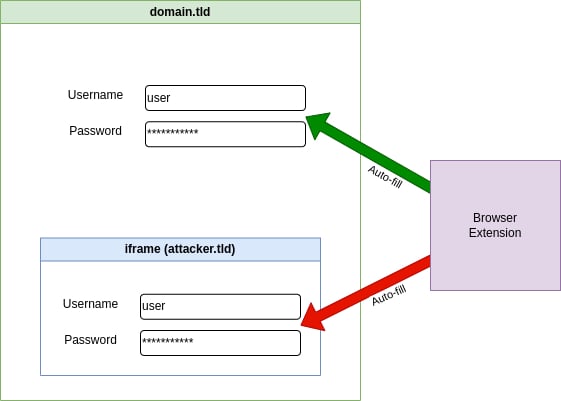
“While the embedded iframe does not have access to any content in the parent page, it can wait for input to the login form and forward the entered credentials to a remote server without further user interaction,” explains Flashpoint.
Flashpoint investigated how often iframes are embedded on login pages of high-traffic websites and reported that the number of risky cases was very low, significantly decreasing the risk.
However, a second issue discovered by Flashpoint while investigating the iframes problem is that Bitwarden will also auto-fill credentials on subdomains of the base domain matching a login.
This means an attacker hosting a phishing page under a subdomain that matches a stored login for a given base domain will capture the credentials upon the victim visiting the page if autofill is enabled.
“Some content hosting providers allow hosting arbitrary content under a subdomain of their official domain, which also serves their login page,” explains Flashpoint in the report.
“As an example, should a company have a login page at https://logins.company.tld and allow users to serve content under https://
Registering a subdomain that matches the base domain of a legitimate website is not always possible, so the severity of the problem is reduced.
However, some services allow users to create subdomains to host content, such as free hosting services, and the attack is still possible through subdomain hijacking.
Bitwarden’s response
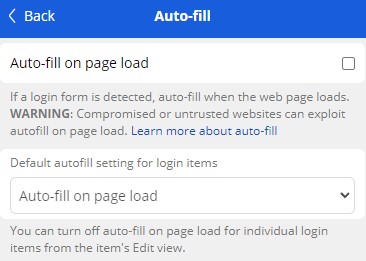
Bitwarden highlights that the autofill feature is a potential risk and even includes a prominent warning in its documentation, specifically mentioning the likelihood of compromised sites abusing the autofill feature to steal credentials.
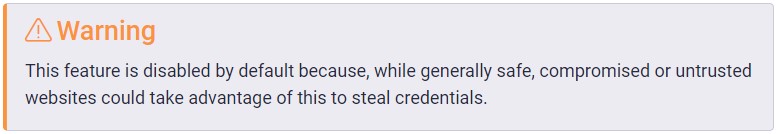
This risk was first brought to light in a security assessment dated November 2018, so Bitwarden has been aware of the security problem for some time now.
However, since users need to log in to services using embedded iframes from external domains, Bitwarden’s engineers decided to keep the behavior unchanged and add a warning on the software’s documentation and the extension’s relevant settings menu.
(BleepingComputer)
Responding to Flashpoint’s second report about the URI handling and how auto-fill treats subdomains, Bitwarden promised to block autofill on the reported hosting environment in a future update but do not plan on changing the iframe functionality.
When BleepingComputer contacted Bitwarden about the security risk, they confirmed that they have known about this issue since 2018 but have not changed the functionality as login forms on legitimate sites use iframes.
“Bitwarden accepts iframe auto filling because many popular websites use this model, for example icloud.com uses an iframe from apple.com,” Bitwarden told BleepingComputer in a statement.
“So there are perfectly valid use cases where login forms are in an iframe under a different domain.”
“The feature described for autofill in the blog post is NOT enabled by default in Bitwarden and there is a warning message on that feature for exactly this reason within the product, and within the help documentation. https://bitwarden.com/help/auto-fill-browser/#on-page-load.”
