A joint Cybersecurity Advisory (CSA) from the FBI and CISA have been published on actively exploiting the vulnerability in some versions of PaperCut NG and PaperCut MF, identified as CVE-2023-27350.
This makes it possible for an unauthenticated actor to execute malicious code remotely. In March 2023, PaperCut made a fix available.
The Bl00dy Ransomware Gang attempted to use weak PaperCut servers to attack the Education sector.
“In early May 2023, according to FBI information, the Bl00dy Ransomware Gang gained access to victim networks across the Education Facilities Subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the internet,” reads the security advisory.

“Ultimately, some of these operations led to data exfiltration and encryption of victim systems.”
The vulnerability has been actively exploited since at least April 18, 2023, roughly a month after being made public in March.
Although the issue has been fixed in PaperCut NG and MF versions 20.1.7, 21.2.11, and 22.0.9, organizations have hesitated to apply the upgrade, leaving themselves open to attacks.
Reports mention that this critical-severity remote code execution (RCE) vulnerability affects PaperCut MF and PaperCut NG, the printer management software used by almost 70,000 organizations in over 100 countries.
“PaperCut servers vulnerable to CVE-2023-27350 implement improper access controls in the SetupCompleted Java class, allowing malicious actors to bypass user authentication and access the server as an administrator. After accessing the server, actors can leverage existing PaperCut software features for remote code execution (RCE)”, CISA reports.
Attack by the Bl00dy Ransomware Gang on the Education Sector
About 68% of the PaperCut servers accessible via the internet, according to CISA, are in the Education Facilities subsector. But it’s still unclear how many vulnerable endpoints are unpatched.
Utilizing CVE-2023-27350 to circumvent user authentication and acquire administrator access to the system, the Bl00dy ransomware attacks that have been recently observed were successful against several targets in the industry.
This access was then used to generate additional ‘cmd.exe’ and ‘powershell.exe’ processes with the same high privileges to acquire remote access to the device and use it as a launchpad to expand laterally via the network.
The ransomware perpetrators take data and encrypt the target systems during this time, then leave notes requesting payment in exchange for a working decryptor and a pledge not to share or sell the stolen content.
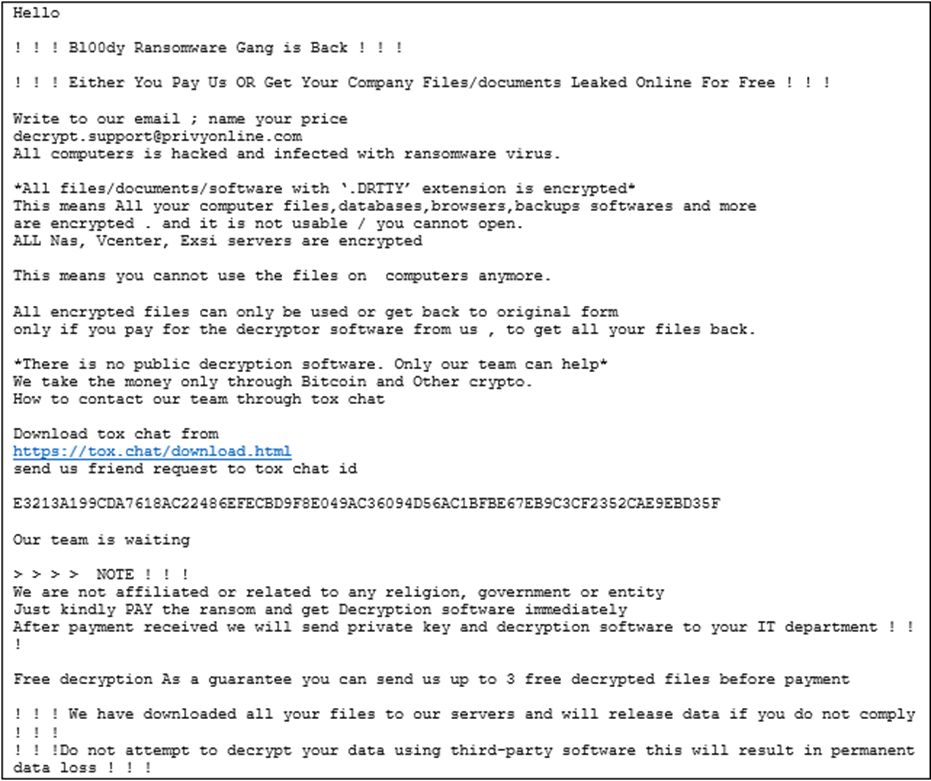
“The Bl00dy Ransomware Gang left ransom notes on victim systems demanding payment in exchange for the decryption of encrypted files”, says the report.
Notably, legitimate remote management and maintenance (RMM) software, according to FBI research, was downloaded and run on victim systems using commands sent through PaperCut’s print scripting interface.
Bl00dy Gang ransomware actors could conceal their malicious network traffic by communicating with other networks through Tor and/or other proxies within victim networks.
The FBI also discovered evidence of the download and use of command and control (C2) malware, including DiceLoader, TrueBot, and Cobalt Strike Beacons. However, It is unknown when these tools were used in the attack.
Hence, users and administrators are urged by the FBI and CISA to immediately deploy fixes and employ workarounds if that is not possible.

Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus
