Russia-linked ransomware gang Black Basta has raked in at least $100 million in ransom payments from more than 90 victims since it first surfaced in April 2022, according to joint research from Corvus Insurance and Elliptic.
Over 329 victims worldwide were targeted by the cybercrime operation in double extortion attacks where the gang’s affiliates steal sensitive data from compromised systems before deploying ransomware payloads across the targets’ networks to encrypt hacked systems.
The stolen data is then used to pressure victims into paying the ransoms under the threat of publishing it on Black Basta’s dark web leak site.
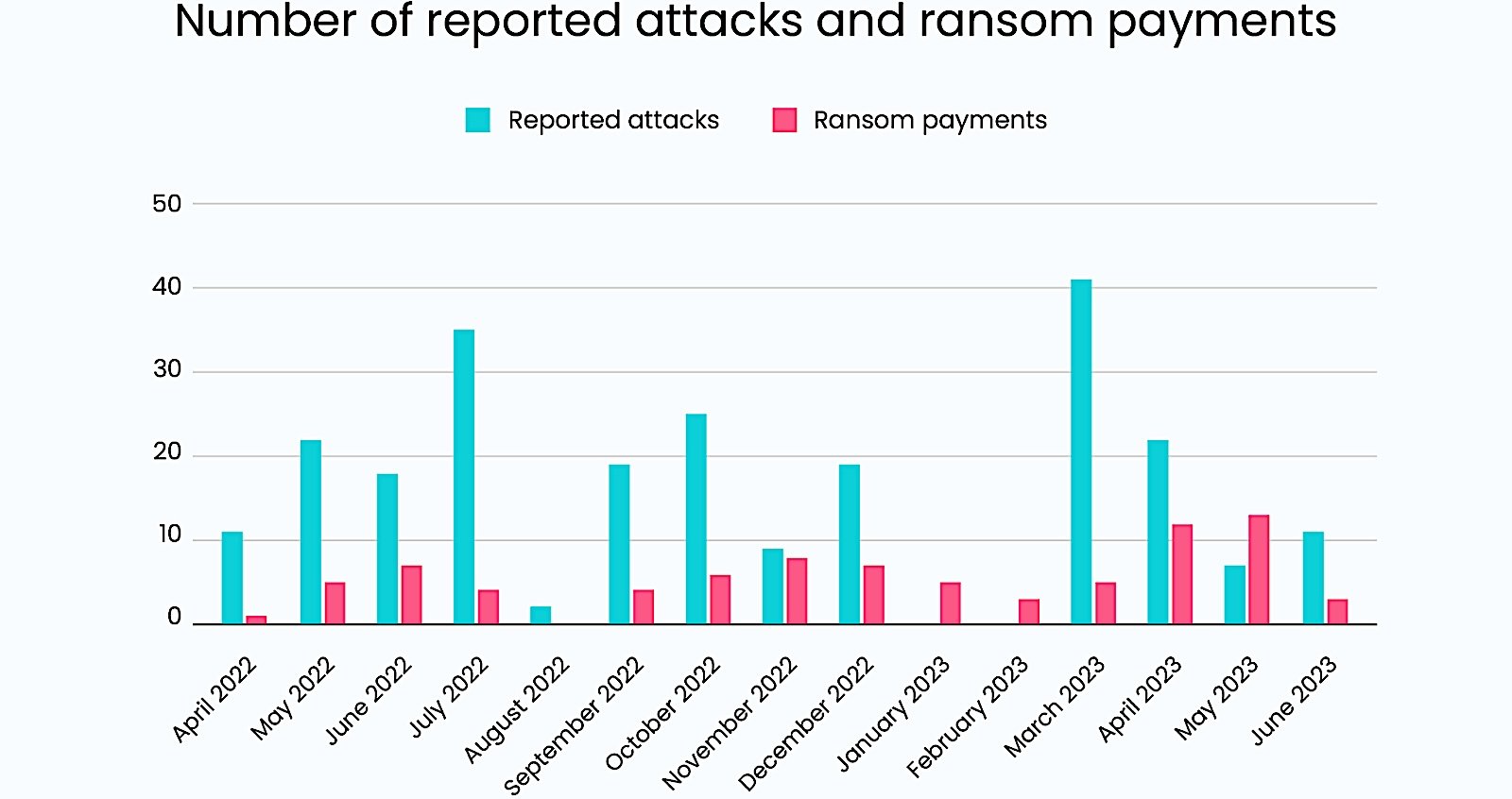
“Our analysis suggests that Black Basta has received at least $107 million in ransom payments since early 2022, across more than 90 victims. The largest received ransom payment was $9 million, and at least 18 of the ransoms exceeded $1 million. The average ransom payment was $1.2 million,” the Corvus Threat Intel team said.
“Based on the number of known victims listed on Black Basta’s leak site through Q3 of 2023, our data indicates that at least 35% of known Black Basta victims paid a ransom.”
This is consistent with ransomware negotiation company Coveware’s findings that, despite record-low ransomware payments in 2022, roughly 41% of all ransomware victims have paid a ransom.
Black Basta surfaced as a Ransomware-as-a-Service (RaaS) operation in April 2022, targeting corporate entities worldwide in double-extortion attacks.
After the notorious Conti ransomware gang shut down operations in June 2022 due to a series of embarrassing data breaches, the cybercrime syndicate split into multiple groups, with one faction believed to be Black Basta.
“The threat group’s prolific targeting of at least 20 victims in its first two weeks of operation indicates that it is experienced in ransomware and has a steady source of initial access,” the Department of Health and Human Services security team said in a March report.
“The level of sophistication by its proficient ransomware operators, and reluctance to recruit or advertise on Dark Web forums, supports why many suspect the nascent Black Basta may even be a rebrand of the Russian-speaking RaaS threat group Conti, or also linked to other Russian-speaking cyber threat groups.”
Furthermore, Black Basta has also been linked with the Russian-speaking FIN7 hacking group, a well-known financially motivated cybercrime group active since at least 2015, also tracked as Carbanak.
Since it emerged, this ransomware gang has infiltrated and extorted many high-profile victims, including the American Dental Association, Sobeys, Knauf, Yellow Pages Canada, Toronto Public Library, and the German defense contractor Rheinmetall.
Black Basta’s victim list also includes Capita, a U.K. technology outsourcing firm earning billions of dollars from U.K. government contracts, and ABB, an industrial automation company and contractor for the U.S. government, with revenues surpassing $29 billion. Neither of them has publicly disclosed whether they paid Black Basta’s ransoms.
