A sophisticated cyberattack campaign orchestrated by the notorious “Black Cat” criminal gang has been uncovered by CNCERT and Microstep Online, revealing a coordinated effort to compromise internet users through weaponized fake Notepad++ download websites.
The operation exploits search engine optimization techniques to deceive unsuspecting users into installing malware-laden software packages that deploy backdoor trojans designed to exfiltrate sensitive data.
When users search for “Notepad++” on major search engines, a meticulously crafted phishing website appears as the second-ranked result, closely mimicking legitimate download portals.
This strategic placement exploits user trust in search engine rankings, significantly increasing the likelihood of successful compromise.
The phishing infrastructure demonstrates sophisticated social engineering, featuring realistic website designs complete with tutorial articles and multiple download options to enhance credibility.
Rather than directly linking to malicious payloads, the attackers employ a multi-stage redirection process that routes victims through authentic-looking download pages styled to resemble GitHub’s interface, systematically lowering user suspicion before delivering the infected installer.
Track Record of Cryptocurrency Theft
The Black Cat group’s criminal operations date back to 2022, with a consistent focus on data theft and remote access capabilities.
The Black Cat gang has addressed search engine results by manipulating SEO algorithms to position fraudulent Notepad++ download sites prominently in search rankings.
In 2023, the organization successfully stole approximately $160,000 in cryptocurrency by impersonating AICoin, a cryptocurrency trading platform, through fake download websites.
The following year saw the gang deploy counterfeit Chrome browser installations via Bing search results, distributing both data-stealing malware and cryptocurrency mining programs to compromised systems.
By June 2025, the threat actors had expanded their targeting to include popular software applications such as QQ International and iTools, distributed through well-known domestic search engines.
This evolution demonstrates the gang’s adaptability and expanding scope, transitioning from targeting specific user demographics to compromising ordinary internet users across broader categories.
The malicious Notepad++ installer employs a multi-layered execution chain to establish persistence and evade detection.
Upon installation, the program creates a desktop shortcut pointing to a backdoor component rather than the legitimate application.
This backdoor utilizes DLL side-loading techniques, executing malicious code through encrypted files stored as M9OLUM4P.1CCE, which are decrypted and reflectively loaded into memory during execution.
The malware establishes communication with command-and-control infrastructure through the hardcoded domain sbido.com on port 2869. Domain registration records indicate sbido.com was registered on September 5, 2025, with DNS resolution analysis revealing exclusive association with Black Cat infrastructure since September 12, 2025.
The trojan’s primary functions include browser credential theft, keylogging, clipboard monitoring, and exfiltration of sensitive host data.
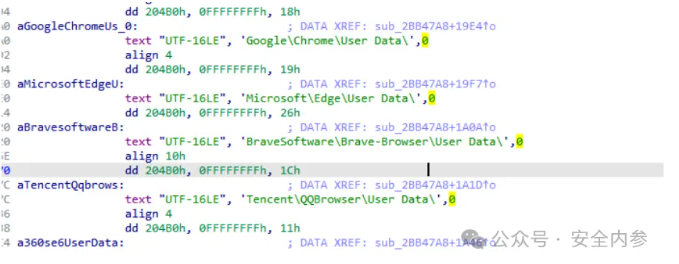
To maintain persistence, the malware creates registry-based startup entries and establishes directories for storing stolen data before transmission to attacker-controlled servers.
The backdoor represents a custom-developed data-stealing trojan unique to the Black Cat operation, distinguishing it from commodity malware available on criminal marketplaces.
Mitigations
Monitoring data reveals the campaign’s substantial impact, with approximately 277,800 compromised servers detected in China between December 7-20, 2025.
Daily botnet activity peaked at 62,167 infected systems online simultaneously, generating up to 437,700 daily command-and-control server connections.

This infection scale underscores the campaign’s effectiveness and the urgent need for defensive measures.
Security researchers recommend users download software exclusively from official websites or verified repositories, verifying file integrity through hash validation and antivirus scanning.
Organizations should deploy endpoint protection solutions with regular system scanning, while users must exercise caution with unsolicited download links and unknown software sources.
Immediate incident response procedures should be initiated upon detecting botnet infections, including forensic analysis of compromise vectors and thorough system remediation.
The Black Cat gang’s continued operations highlight the persistent threat posed by financially motivated cybercriminal organizations leveraging search engine manipulation and social engineering to compromise systems at scale.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
