Black Friday is supposed to be chaotic, sure, but not this chaotic.
While monitoring malvertising patterns ahead of the holiday rush, I uncovered one of the most widespread and polished Black Friday scam campaigns circulating online right now.
It’s not a niche problem. Our own research shows that 40% of people have been targeted by malvertising, and more than 1 in 10 have fallen victim, a trend that shows up again and again in holiday-season fraud patterns. Read more in our 2025 holiday scam overview.
Through malicious ads hidden on legitimate websites, users are silently redirected into an endless loop of fake “Survey Reward” pages impersonating dozens of major brands.
What looked like a single suspicious redirect quickly turned into something much bigger. One domain led to five more. Five led to twenty. And as the pattern took shape, the scale became impossible to ignore: more than 100 unique domains, all using the same fraud template, each swapping in different branding depending on which company they wanted to impersonate.
This is an industrialized malvertising operation built specifically for the Black Friday window.
The brands being impersonated
The attackers deliberately selected big-name, high-trust brands with strong holiday-season appeal. Across the campaign, I observed impersonations of:
- Walmart
- Home Depot
- Lowe’s
- Louis Vuitton
- CVS Pharmacy
- AARP
- Coca-Cola
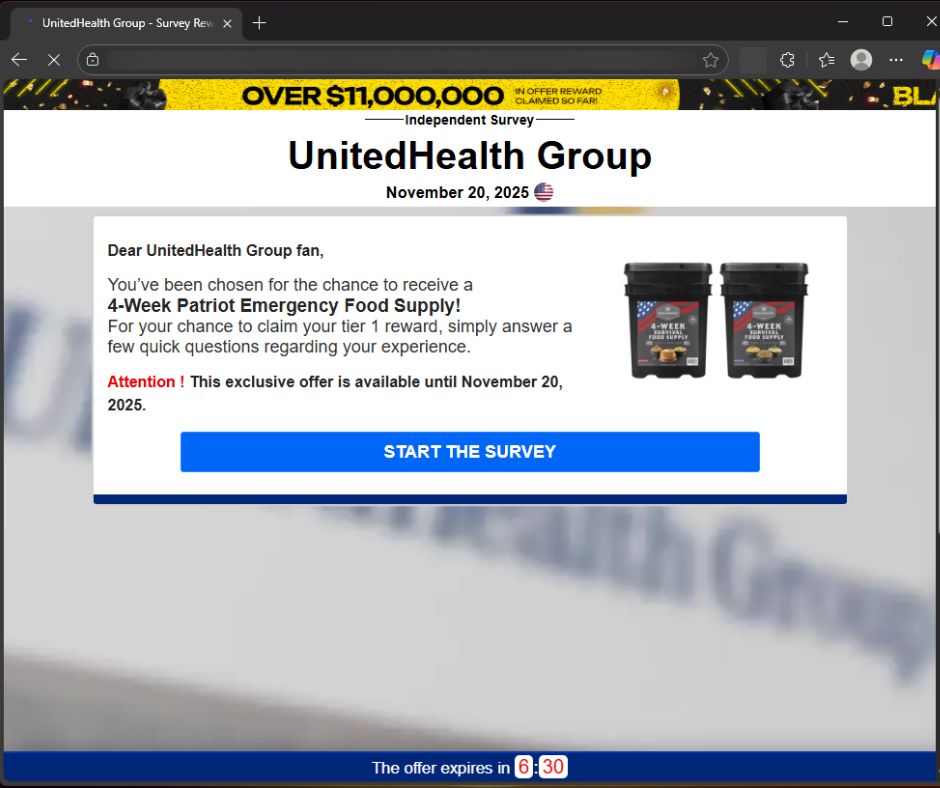
- UnitedHealth Group
- Dick’s Sporting Goods
- YETI
- LEGO
- Ulta Beauty
- Tourneau / Bucherer
- McCormick
- Harry & David
- WORX
- Northern Tool
- POP MART
- Lovehoney
- Petco
- Petsmart
- Uncharted Supply Co.
- Starlink (especially the trending Starlink Mini Kit)
- Lululemon / “lalubu”-style athletic apparel imitators
These choices are calculated. If people are shopping for a LEGO Titanic set, a YETI bundle, a Lululemon-style hoodie pack, or the highly hyped Starlink Mini Kit, scammers know exactly what bait will get clicks.
In other words: They weaponize whatever is trending.
How the scam works
1. A malicious ad kicks off an invisible redirect chain
A user clicks a seemingly harmless ad—or in some cases, simply scrolls past it—and is immediately funneled through multiple redirect hops. None of this is visible or obvious. By the time the page settles, the user lands somewhere they never intended to go.
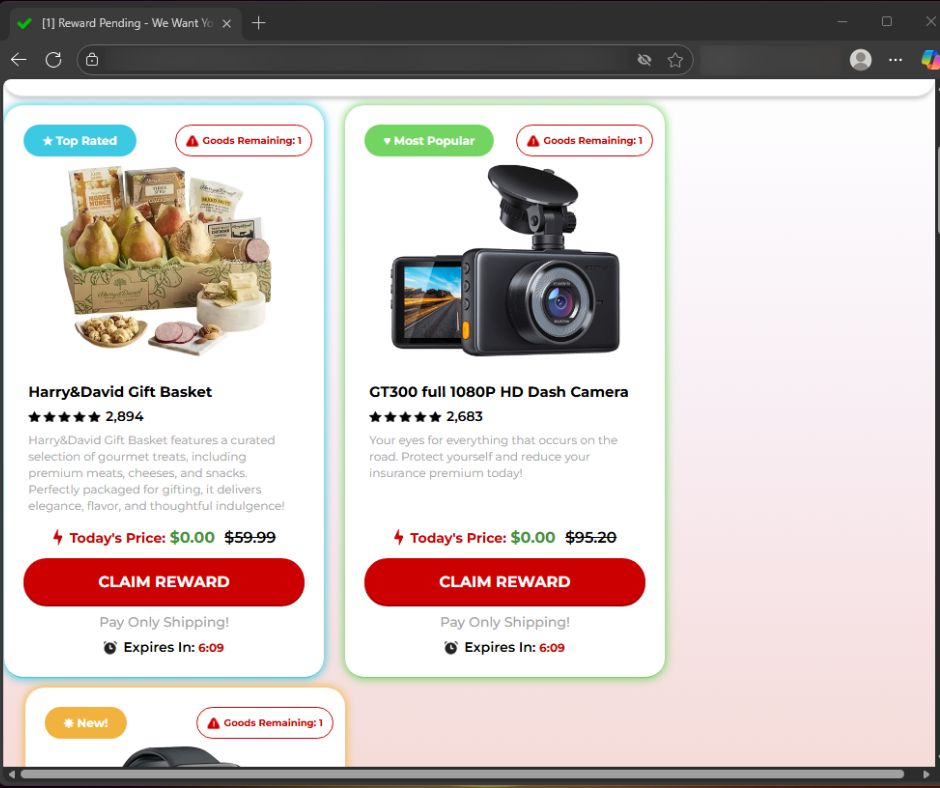
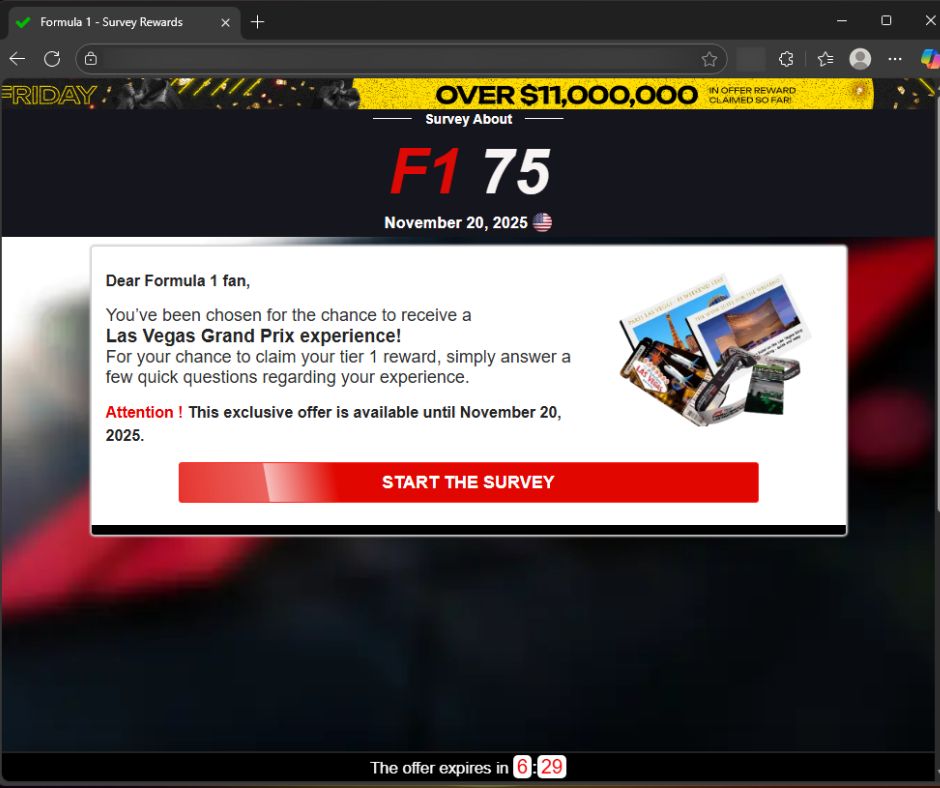
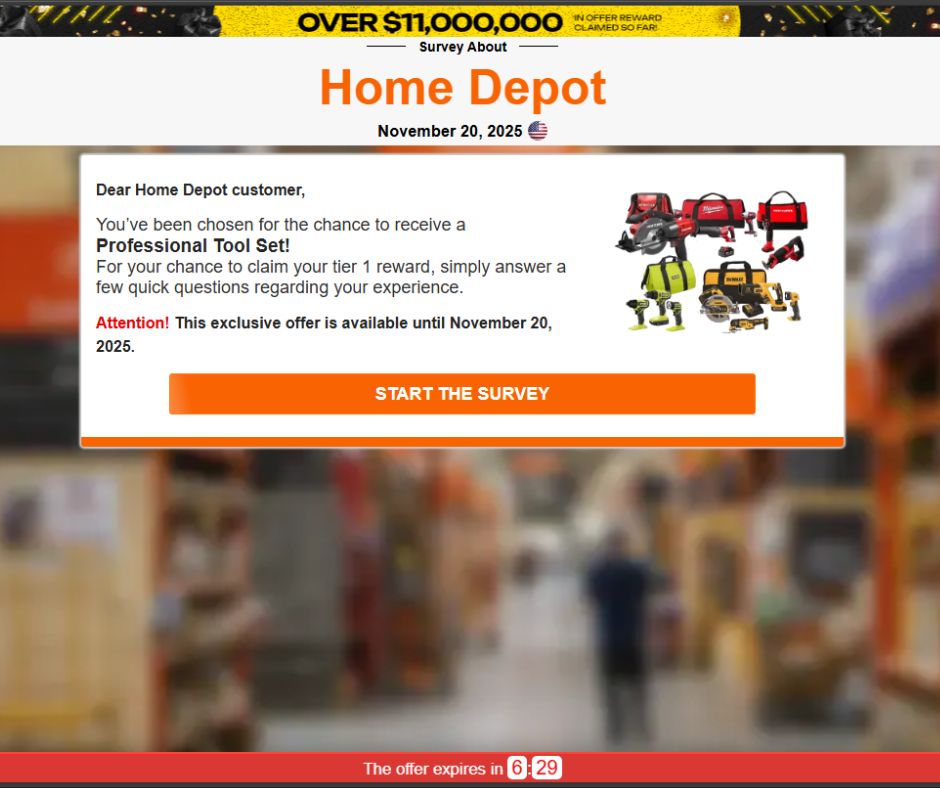
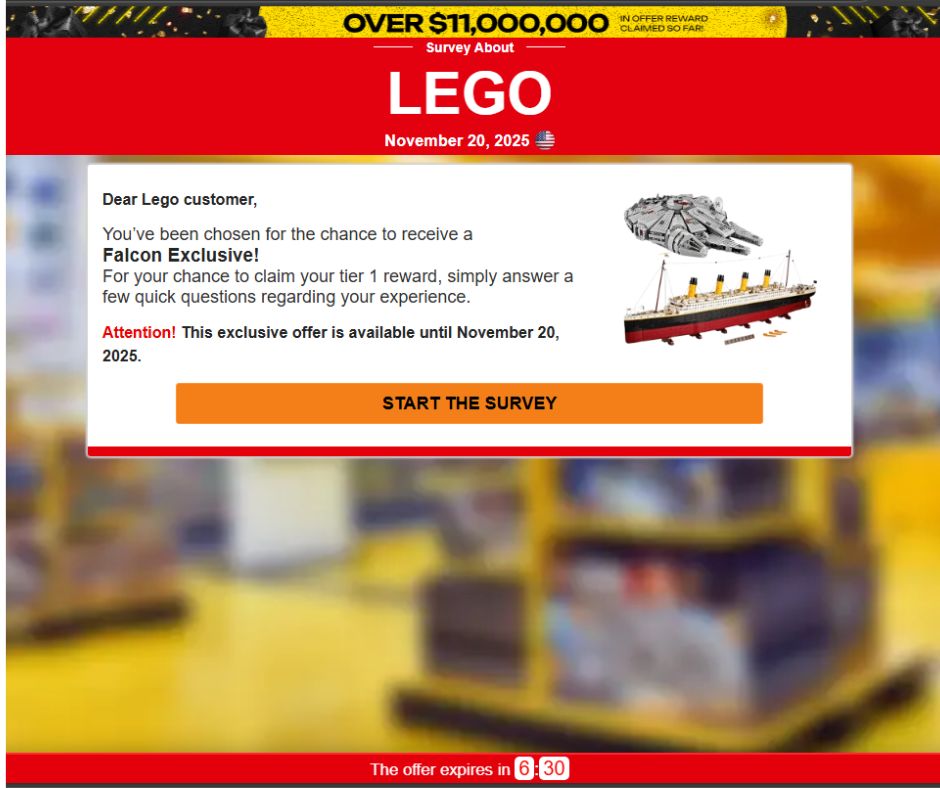
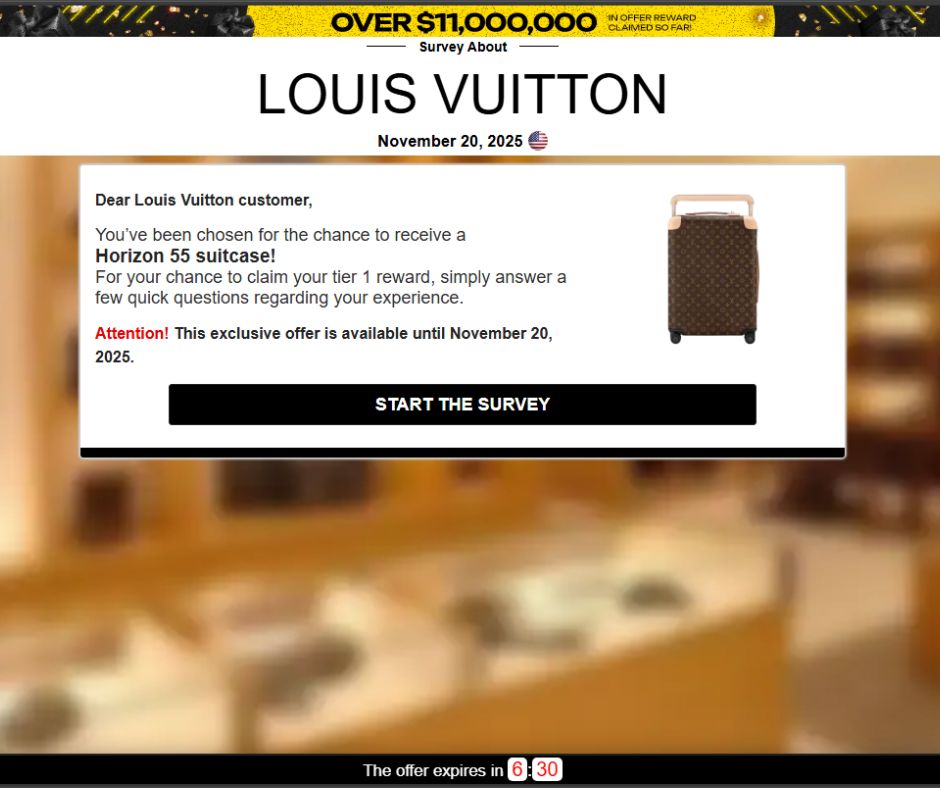
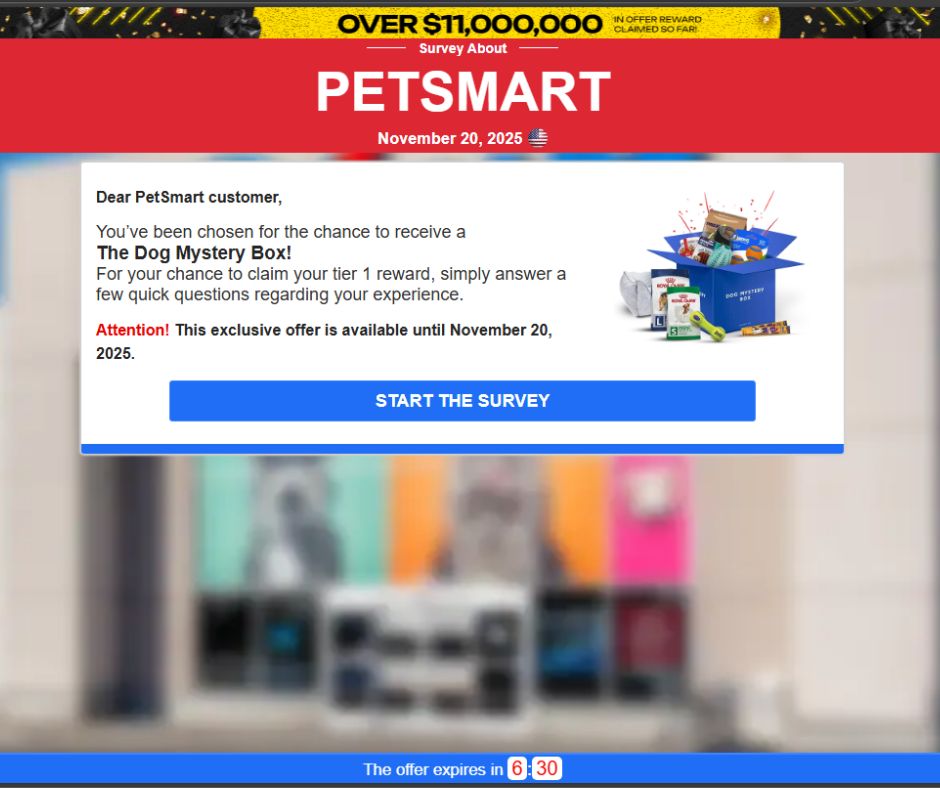
2. A polished “Survey About [Brand]” page appears
Every fake site is built on the same template:
- Brand name and logo at the top
- A fake timestamp (“Survey – November X, 2025 ”)
- A simple, centered reward box
- A countdown timer to create urgency
- A blurred background meant to evoke the brand’s store or product environment
It looks clean, consistent, and surprisingly professional.
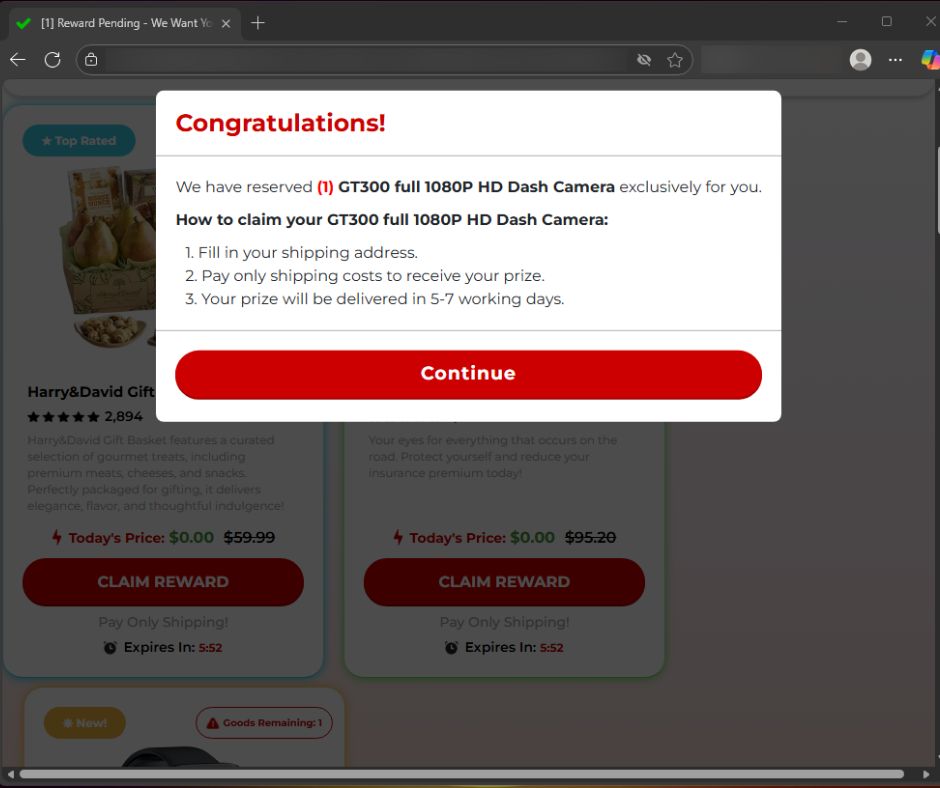
3. The reward depends on which brand is being impersonated
Some examples of “rewards” I found in my investigation:
- Starlink Mini Kit
- YETI Ultimate Gear Bundle
- LEGO Falcon Exclusive / Titanic set
- Lululemon-style athletic packs
- McCormick 50-piece spice kit
- Coca-Cola mini-fridge combo
- Petco / Petsmart “Dog Mystery Box”
- Louis Vuitton Horizon suitcase
- Home Depot tool bundles
- AARP health monitoring kit
- WORX cordless blower
- Walmart holiday candy mega-pack
Each reward is desirable, seasonal, realistic, and perfectly aligned with current shopping trends. This is social engineering disguised as a giveaway. I wrote about the psychology behind this sort of scam in my article about Walmart gift card scams.
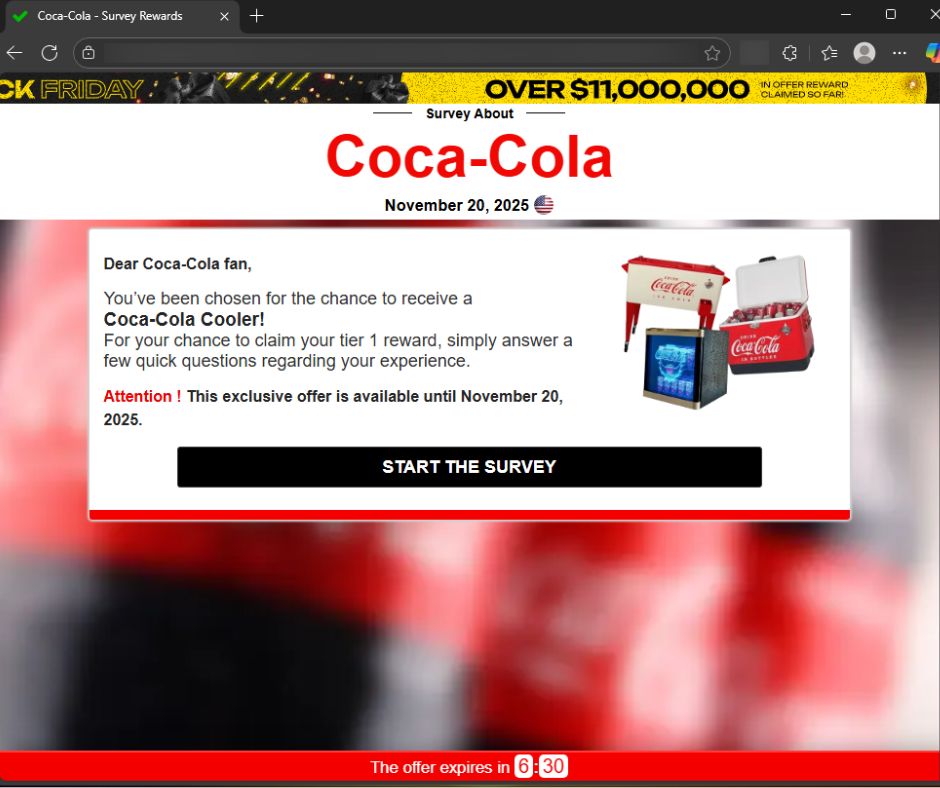


4. The “survey” primes the victim
The survey questions are generic and identical across all sites. They are there purely to build commitment and make the user feel like they’re earning the reward.
After the survey, the system claims:
- Only 1 reward left
- Offer expires in 6 minutes
- A small processing/shipping fee applies
Scarcity and urgency push fast decisions.
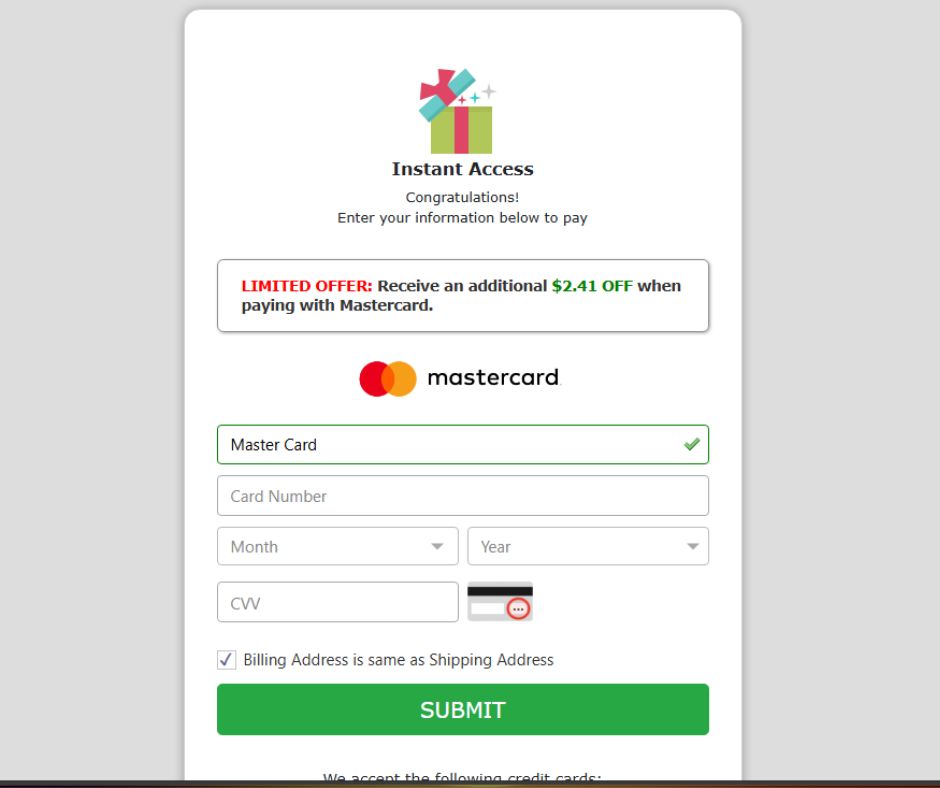
5. The final step: a “shipping fee” checkout
Users are funneled into a credit card form requesting:
- Full name
- Address
- Phone
- Complete credit card details, including CVV
The shipping fees typically range from $6.99 to $11.94. They’re just low enough to feel harmless, and worth the small spend to win a larger prize.
Some variants add persuasive nudges like:
“Receive $2.41 OFF when paying with Mastercard.”
While it’s a small detail, it mimics many legitimate checkout flows.
Once attackers obtain personal and payment data through these forms, they are free to use it in any way they choose. That might be unauthorized charges, resale, or inclusion in further fraud. The structure and scale of the operation strongly suggest that this data collection is the primary goal.
Why this scam works so well
Several psychological levers converge here:
- People expect unusually good deals on Black Friday
- Big brands lower skepticism
- Timers create urgency
- “Shipping only” sounds risk-free
- Products match current hype cycles
- The templates look modern and legitimate
Unlike the crude, typo-filled phishing of a decade ago, these scams are part of a polished fraud machine built around holiday shopping behavior.
Technical patterns across the scam network
Across investigations, the sites shared:
- Identical HTML and CSS structure
- The same JavaScript countdown logic
- Nearly identical reward descriptions
- Repeated “Out of stock soon / 1 left” mechanics
- Swappable brand banners
- Blurred backgrounds masking reuse
- High-volume domain rotation
- Multi-hop redirects originating from malicious ads
It’s clear these domains come from a single organized operation, not a random assortment of lone scammers.
Final thoughts
Black Friday always brings incredible deals, but it also brings incredible opportunities for scammers. This year’s “free gift” campaign stands out not just for its size, but for its timing, polish, and trend-driven bait.
It exploits, excitement, brand trust, holiday urgency, and the expectation of “too good to be true” deals suddenly becoming true.
Staying cautious and skeptical is the first line of defense against “free reward” scams that only want your shipping details, your identity, and your card information.
And for an added layer of protection against malicious redirects and scam domains like the ones uncovered in this campaign, users can benefit from keeping tools such as Malwarebytes Browser Guard enabled in their browser.
Stay safe out there this holiday season.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!
