ESET researchers have uncovered a series of malicious tools deployed by BladedFeline, an Iran-aligned advanced persistent threat (APT) group, targeting Kurdish and Iraqi government officials.
Active since at least 2017, BladedFeline has been linked with medium confidence to the notorious OilRig APT group, known for cyberespionage across the Middle East.
Sophisticated Cyberespionage Campaign
The group’s latest arsenal, discovered in 2024, includes the Whisper backdoor and the PrimeCache malicious IIS module, which exploit Microsoft Exchange servers and Internet Information Services (IIS) to maintain persistent access to compromised systems.
This campaign not only highlights BladedFeline’s evolving technical prowess but also underscores the strategic importance of their targets, including the Kurdistan Regional Government (KRG), Iraqi government officials, and a telecommunications provider in Uzbekistan.
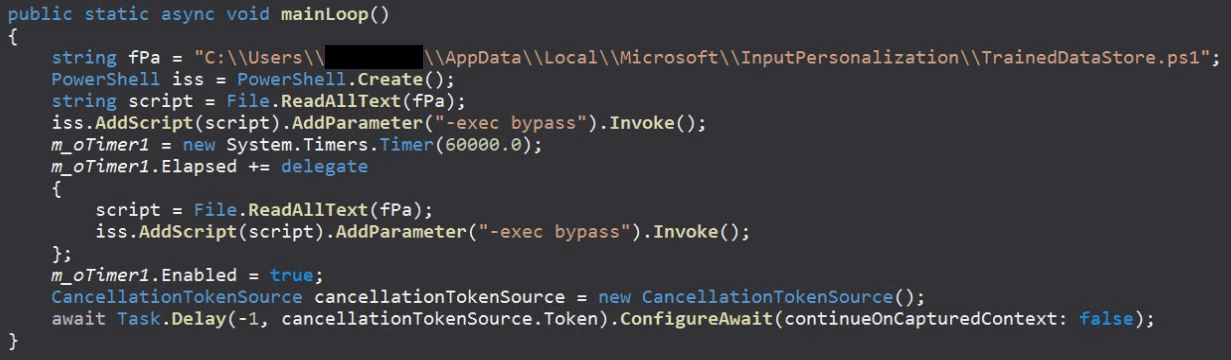
Delving into the technical underpinnings, the Whisper backdoor operates by infiltrating Microsoft Exchange servers through compromised webmail accounts, using email attachments as a covert channel for command-and-control (C&C) communication.
Written in C#/.NET, Whisper logs into these accounts, sets up inbox rules to filter specific messages, and executes commands such as file manipulation and PowerShell script execution, transmitting results back to attackers via encrypted attachments.
Its configuration, stored in an XML file with base64-encoded credentials, ensures seamless operation without user intervention.
Technical Intricacies of Whisper
On the other hand, PrimeCache, a native IIS module, functions as a passive backdoor by filtering HTTP requests with specific cookie headers to process operator commands.
Unlike its predecessors, it splits actions into multiple requests, storing parameters globally before execution, and employs RSA and AES-CBC encryption for secure C&C communication.
The similarities between PrimeCache and OilRig’s RDAT backdoor, including shared code structures and the use of the Crypto++ library, further cement the connection between BladedFeline and OilRig.
According to ESET researchers, the scope of BladedFeline’s operations reveals a calculated effort to sustain access to high-value targets.
Since 2017, the group has deployed various tools like the Shahmaran backdoor and reverse tunnels such as Laret and Pinar on KRG systems, alongside targeting Iraqi officials with tools uploaded to VirusTotal.
Their exploitation tactics, potentially involving vulnerabilities in internet-facing web servers, have allowed deployment of webshells like Flog, enhancing their foothold.
The geopolitical motivations are clear access to KRG’s diplomatic ties and Iraq’s strategic landscape post-US occupation offers significant espionage opportunities for Iran-aligned actors.
BladedFeline’s continuous development of malware, evidenced by tools like Slippery Snakelet and supplementary utilities, indicates a persistent threat that demands robust countermeasures.
Indicators of Compromise (IoCs)
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 01B99FF47EC6394753F9CCDD2D43B3E804F9EE36 | Avamer.pdf.exe | Python/TrojanDropper.Agent.GI | Python-compiled dropper for Spearal |
| 562E1678EC8FDC1D83A3F73EB511A6DDA08F3B3D | LogonUl.exe | Win64/OilRig_AGen.A | RDAT backdoor |
| 6973D3FF8852A3292380B07858D43D0B80C0616E | VeeamUpdate.exe | MSIL/Agent.ERR | Whisper backdoor |
| 73D0FAA475C6E489B2C5C95BB51DEDE4719D199E | winhttpproxy.exe | MSIL/HackTool.Agent.XY | Pinar, a reverse tunnel |
| BE0AD25B7B48347984908175404996531CFD74B7 | videosrv.exe | Generik.BKYYERR | VideoSRV, a reverse shell |
Exclusive Webinar Alert: Harnessing Intel® Processor Innovations for Advanced API Security – Register for Free
