The world has recently witnessed a surge in cyber attacks, and the United States is no exception.
A relatively new hacker collective called the Bluenet ransomware group has emerged as a prominent threat, following a pattern often associated with pro-Russian groups.
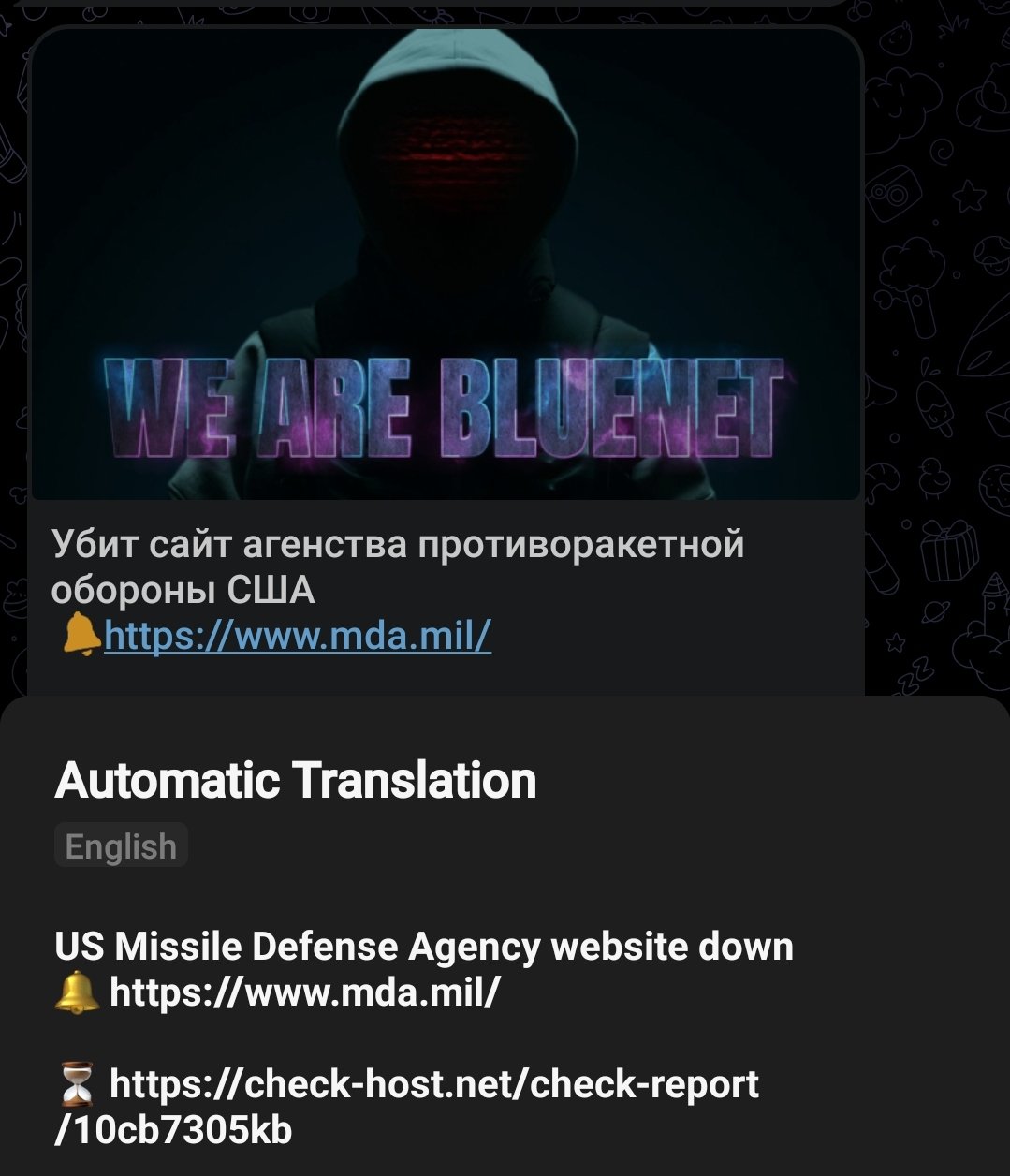
Bluenet ransomware group has brazenly claimed responsibility for launching cyber attack on US, targeting both US military sites and commercial airports.
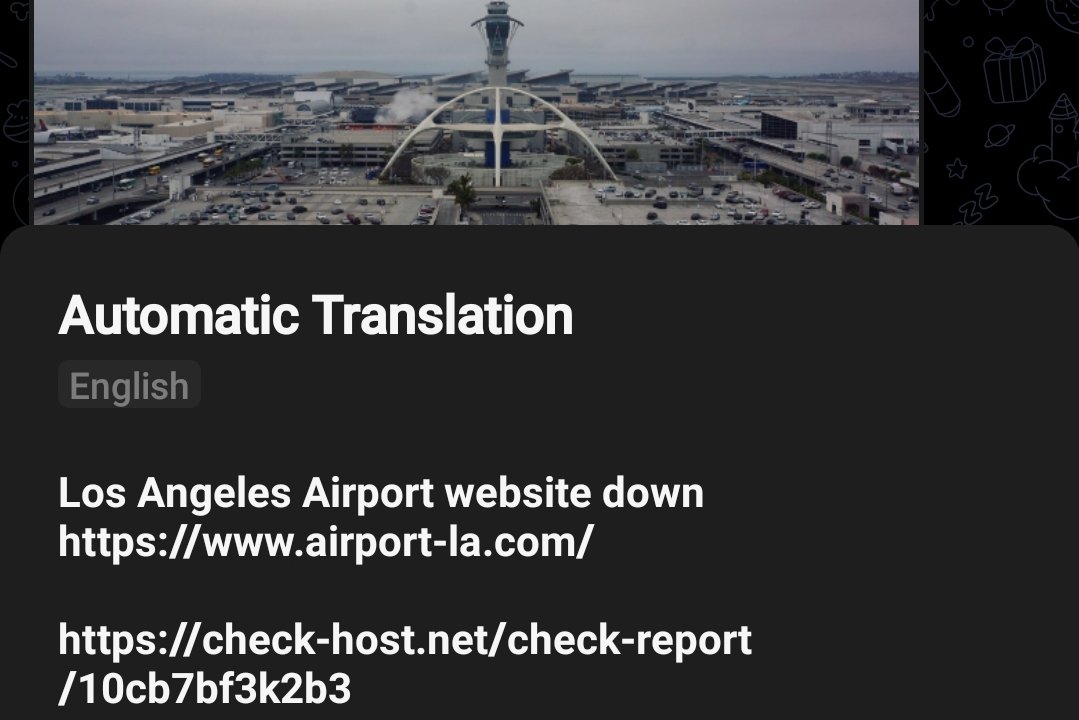
Among the notable targets are the US Missile Defense Agency and the Los Angeles International Airport.

The claims made by Bluenet were posted publicly, showcasing the group’s confidence in its ability to infiltrate high-profile targets.
The post included evidence of the successfully launching cyber attack on the US Missile Defense Agency (https://www.mda.mil/) and Los Angeles International Airport (https://www.airport-la.com/).
Bluenet Ransomware Group: A new threat claiming to associate with Killnet

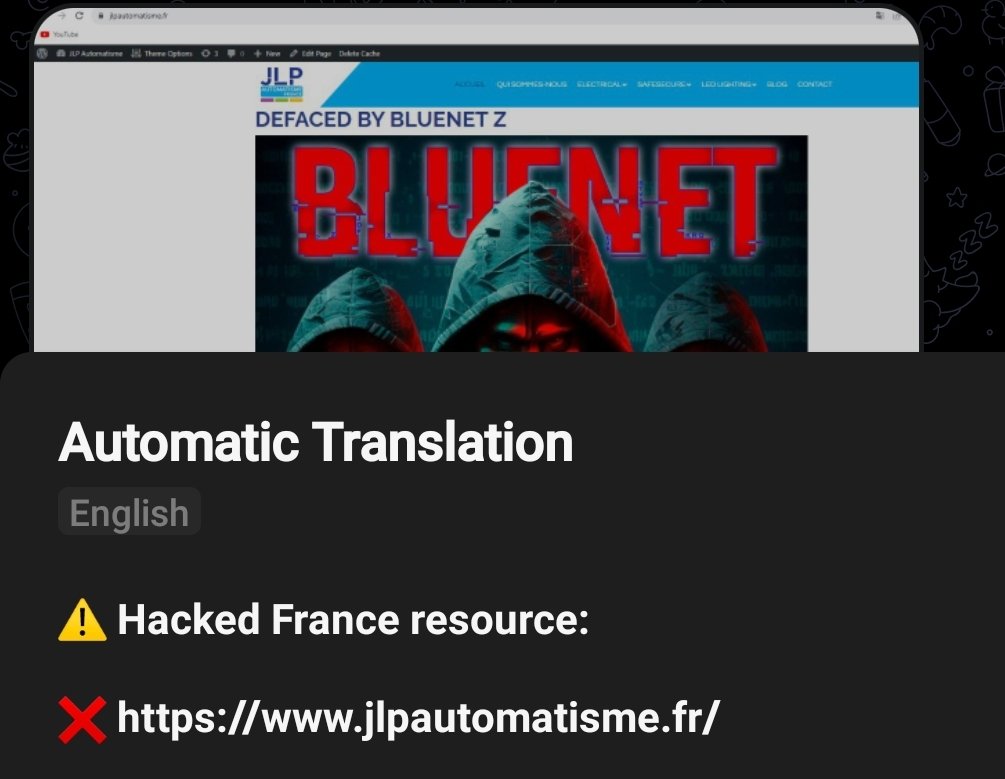
The hacker group’s post was captioned, “US Missile Defense Agency Website Killed,” signaling their achievement in taking down the crucial security agency’s website. In addition to these high-profile attacks, Bluenet ransomware group has also claimed responsibility for defacing a French website (https://www.jlpautomatisme.fr/), which remains defaced at the time of reporting, as verified by CyberKnow.
This indicates that the hacker group is not limiting its activities to the US but is expanding its reach internationally.
Reports from July 19, 2023, revealed that the Bluenet ransomware group had launched a cyber attack on US Department of Energy website, further solidifying its reputation as a potent cyber threat.
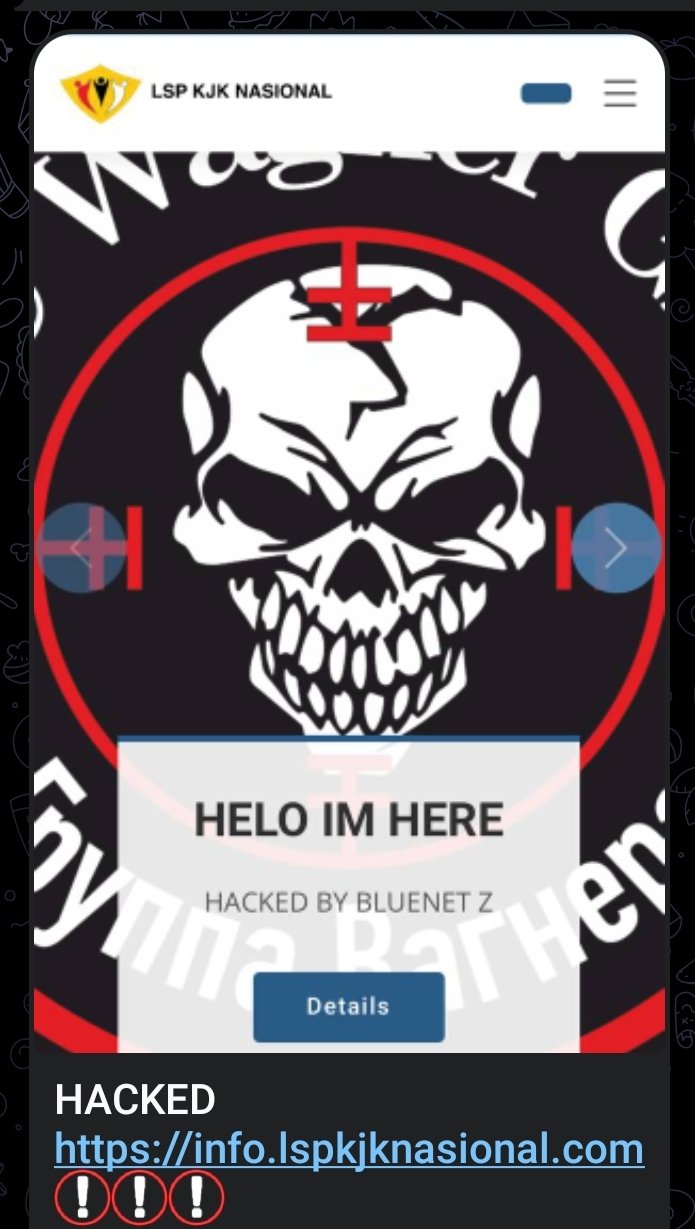
On July 23rd, 2023, it came to light that Bluenet ransomware group, with alleged ties to Killnet and Usersec, defaced an Indonesian website using what seemed to be the Wagner emblem. The exact geo-political motivations behind this attack remain unclear.
It is worth noting that the Bluenet ransomware group has claimed affiliation with Killnet but has only been active since July 4th. While this affiliation is yet to be confirmed, the group has been consistently carrying out attacks, possibly as a tribute to Killnet.
Cyber attack on US: A trail of ransomware groups targeting the country
According to data released by Chainalysis, ransomware groups received a staggering $449.1 million in ransom payments during the initial half of this year. R
emarkably, this amount already surpasses the total sum paid throughout the entirety of 2022, which did not even reach $500 million. The alarming trend suggests that if ransom payments continue at the current pace, the total figure for 2023 could reach a staggering $898.6 million.
If this projection holds true, 2023 would become the second-highest earning year for ransomware revenue, coming close to the infamous 2021 when attackers extorted an estimated $939.9 million from their victims.
Unsurprisingly, a majority of them comes from the US.
With its high-value government agencies, military, financial institutions, and advanced technologies, the USA remains a prime target for hackers like the Bluenet ransomware group. The country faces frequent cyber attacks as a global economic and political influencer.
Recently, several US companies experienced such incidents, including disruptions to business operations at Estee Lauder due to a cyber attack.
Moreover, Charter Oak Federal Credit Union, a university in Kentucky, Town of Cornelius in North Carolina, HCA Healthcare in Tennessee, and Hayward in California fell victim to data breaches and ransomware attacks, emphasizing the escalating cyber threats faced by the nation.
To fight this ongoing battle and to fight against hacker collectives like the Bluenet ransomware group, the US Securities and Exchange Commission (SEC) recently introduced a cybersecurity rule that mandates companies to promptly disclose any cyber breach within four days after confirming its significance to investors.
However, the rule permits disclosure delays if the Justice Department considers them essential to safeguard national security or ongoing police investigations, as stated by the SEC.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
