A sophisticated social engineering campaign leveraging the trusted Zoom platform has emerged as the latest weapon in the arsenal of North Korean state-sponsored hackers.
The BlueNoroff group, a financially motivated subgroup of the notorious Lazarus Group, has been orchestrating targeted attacks against cryptocurrency and financial sector organizations through convincingly spoofed Zoom-related infrastructure and impersonation tactics.
The campaign, which has been active since at least March 2025, represents a significant evolution in cybercriminal tradecraft, exploiting the ubiquity of video conferencing platforms in modern business operations.
.png
)
Threat actors have successfully compromised victims by impersonating known business contacts during scheduled Zoom meetings, then manipulating targets into executing malicious scripts disguised as legitimate audio repair tools.
This approach capitalizes on the operational urgency and routine nature of technical troubleshooting in remote work environments.
Field Effect analysts identified a distinct incident involving a Canadian online gambling provider on May 28, 2025, where the threat actor employed advanced social engineering techniques to gain initial access to the victim’s system.
The attack demonstrates the group’s operational maturity and their continued focus on cryptocurrency-related targets, aligning with BlueNoroff’s historical mission to generate revenue for the North Korean regime through cybercrime activities.
The financial and operational impact of these attacks extends beyond immediate data theft, as the malware specifically targets cryptocurrency wallet extensions, browser credentials, and authentication keys.
Organizations in the gaming, entertainment, and fintech sectors across North America, Europe, and Asia-Pacific regions have been identified as primary targets, with the campaign’s scope indicating a coordinated effort to compromise high-value cryptocurrency assets and sensitive financial data.
Sophisticated Infection Mechanism and Multi-Stage Deployment
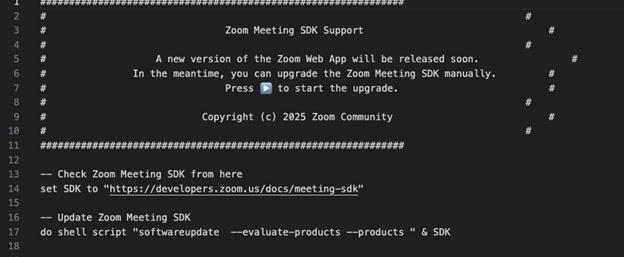
The attack chain begins with a meticulously crafted AppleScript that initially appears to perform legitimate Zoom SDK updates and maintenance tasks.
.webp)
However, analysis of the malicious script reveals approximately 10,000 blank lines designed to obscure the true payload.
The concealed commands execute on lines 10,017 and 10,018, where a curl request downloads and executes the primary infostealer component from the fraudulent domain zoom-tech[.]us.
The malware establishes persistence through multiple mechanisms, including LaunchDaemon configurations that ensure execution at boot time with administrator privileges.
The infection process involves downloading additional payloads from compromised infrastructure, including components masquerading as legitimate system utilities like “icloud_helper” and “Wi-Fi Updater.”
These components employ sophisticated anti-forensics techniques, automatically removing temporary files and staging directories to minimize their forensic footprint while maintaining operational capabilities for data exfiltration and command execution.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial
