Effective cyber threat detection and response depend on the ability to access actionable, real-time intelligence. ANY.RUN, a trusted name in interactive malware analysis, offers Threat Intelligence (TI) Feeds Integration that gives SOC (Security Operations Center) and DFIR (Digital Forensics and Incident Response) teams a real time intelligence feed.
By combining interactive sandbox analysis with freshly updated Indicators of Compromise (IOCs), ANY.RUN enables organizations to proactively detect, investigate, and prepare against emerging threats.

Incorporating data and technical references from ANY.RUN’s blog post on TI Feeds Integration, this article explores how this integration works and why it is essential and how to boost and simplyfy your SOC/DFIR teams operations.
Get 50 free requests in TI Lookup to enrich your threat investigations
How Threat Intelligence Feeds Boost Business Performance
| Aspect | Details |
|---|---|
| Cost Savings | TI feeds reduce costs by proactively identifying and mitigating threats, preventing data breaches, and minimizing reactive measures. |
| Better Decision-Making | High-quality insights help organizations focus on the most critical threats, enabling effective resource allocation and maximizing impact. |
| Protecting Reputation | Early threat detection prevents incidents that could harm a company’s brand, building trust with customers and stakeholders. |
| Enhanced Operational Efficiency | Integrating TI feeds streamlines response processes, improving Mean Time to Resolution (MTTR) and ensuring faster containment and recovery. |
| Regulatory Compliance | TI feeds support compliance with frameworks like GDPR, HIPAA, and PCI by documenting incidents and strengthening security posture. |
Leveraging TI feeds is key to sustaining resilient and efficient operations in an increasingly complex threat landscape.
Features and Technical Functionality of ANY.RUN’s TI Feeds
ANY.RUN’s Threat Intelligence Feeds provide enriched IOC data, collected and pre-processed from malware and phishing samples uploaded by a global community of 500,000 cybersecurity researchers.
These feeds are designed to integrate seamlessly into SIEMs, TIPs, and other security platforms, offering both ease of use and context-rich insights.
Types of Indicators Provided
Malicious IP Addresses:
IPs linked to C2 (Command and Control) servers, phishing campaigns, and other malicious activities.
Use case: SOC teams can block these IPs in firewalls or investigate attack origins using contextual threat data.
type: ipv4-addr
id: ipv4-addr--75725b48-17a3-575d-a5de-b5d9798bde8d
value: 103.168.67.9
created: '2024-06-13T06:26:00.704Z'
modified: '2024-06-13T06:26:00.704Z'
external_references:
- source_name: ANY.RUN task 11ce507f-d535-4bf1-8973-989d7654017a
url: https://app.any.run/tasks/11ce507f-d535-4bf1-8973-989d7654017a
labels:
- RedLine
related_objects:
- relationship_type: contains
source_ref: ipv4-addr--75725b48-17a3-575d-a5de-b5d9798bde8d
target_ref: file--49ef9153-94eb-5d05-bac2-19a54738afab
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 90
revoked: falseExample: An IP may be flagged as part of a ransomware C2 infrastructure, offering additional parameters such as detection timestamps or file associations.
Domains:
Domains used in web-based attacks: ANY.RUN enriches these with historical detection details, threat names, types, and associated hashes, helping analysts track the scope of a campaign.
type: domain-name
id: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
value: mail.sdil.ac.ir
created: '2024-06-10T21:13:17.465Z'
modified: '2024-06-17T13:37:53.620Z'
external_references:
- source_name: ANY.RUN task 64e1d470-dcd4-4d78-b1f0-aa4d9bd6f225
url: https://app.any.run/tasks/64e1d470-dcd4-4d78-b1f0-aa4d9bd6f225
- source_name: ANY.RUN task 090c21da-a050-4f88-bb09-1bae142df1cb
url: https://app.any.run/tasks/090c21da-a050-4f88-bb09-1bae142df1cb
labels:
- AgentTesla
related_objects:
- relationship_type: contains
source_ref: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
target_ref: file--dbee2af2-3be4-5e2a-9bf3-94e3fe8637b3
- relationship_type: contains
source_ref: domain-name--f17dd142-08ac-54cb-bb88-97f1e07fb6fc
target_ref: file--9794dd40-085a-5c84-8d95-70cbd8efcf1d
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falseExample: A phishing domain distributing malware may provide insight into connected campaigns or additional compromised assets.
URLs:
URLs are frequently employed to distribute malware, initiate phishing attacks, or redirect users to malicious content.
type: url
id: url--001c0f70-93f8-583d-96ce-7c260da3a193
value: http://www.goog1evip15.com/dogw/
created: '2024-06-11T21:35:59.640Z'
modified: '2024-06-11T21:35:59.640Z'
external_references:
- source_name: ANY.RUN task 55051854-38c4-4d03-a70a-6dd2ce3d89ca
url: https://app.any.run/tasks/55051854-38c4-4d03-a70a-6dd2ce3d89ca
labels:
- Formbook
related_objects: []
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falseANY.RUN’s TI Feeds analyze these URLs, helping organizations block or investigate attack vectors in real time.
File Hashes and Ports:
File hashes tied to specific threats allow for cross-referencing against internal logs.
type: file
id: file--249382b0-209d-5904-b725-b47663c6c412
hashes:
SHA-256: d564eb94afb174fe3b854de086eda2a4e015d778a9aea9806e79f82044eac74e
SHA-1: 14b96459dff641245aea6dacd34512830d945ee2
MD5: 5edee175c5003771dea841893ea46602
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
file_name: d564eb94afb174fe3b854de086eda2a4e015d778a9aea9806e79f82044eac74e.exe
- type: url
id: url--d65b67ec-39f2-5309-8cc9-56e016b6a48f
value: http://109.248.151.196/rvBZyVEAb230.bin
created: '2024-06-11T18:44:15.898Z'
modified: '2024-06-11T18:44:15.898Z'
external_references:
- source_name: ANY.RUN task 35d75e14-c1a2-418c-b98f-f7d58cca93cb
url: https://app.any.run/tasks/35d75e14-c1a2-418c-b98f-f7d58cca93cb
labels:
- guloader
related_objects:
- relationship_type: contains
source_ref: url--d65b67ec-39f2-5309-8cc9-56e016b6a48f
target_ref: file--249382b0-209d-5904-b725-b47663c6c412
created_by_ref: identity--96a9cd9c-2f73-5ad3-a2ab-c14b3eba65c7
score: 100
revoked: falsePorts involved in malicious activity help trace usage patterns in C2 communication.
Malicious IP addresses are often linked to Command and Control (C2) servers, phishing campaigns, and other harmful activities.
Core Advantages of ANY.RUN’s TI Feeds for SOC/DFIR Teams
| Feature | Details |
|---|---|
| 1. Fresh, Processed Threat Intelligence | |
| Real-time Updates | IOCs are updated every few hours, leveraging the latest public data from malware samples uploaded to the ANY.RUN sandbox. |
| Pre-processed and Validated | Data is filtered using advanced algorithms and proprietary technology to ensure accurate, actionable intelligence, reducing noise and false positives. |
| 2. Rich Contextual Enrichment | |
| Sandbox Insights | Every IOC is enriched with direct links to the corresponding sandbox session, enabling analysts to view memory dumps, network traffic, behavior patterns, and more. |
| Threat Campaign Details | Analysts can inspect associated threat names, detection timestamps, and related files to understand an attack’s broader context. |
| 3. Seamless Integration with SIEMs and TIPs | |
| Standardized Formats | TI Feeds are delivered in widely-used formats such as STIX and MISP, ensuring compatibility with solutions like Splunk, OpenCTI, and ThreatConnect. |
| Plug-and-Play Compatibility | Feeds can be integrated into existing systems with minimal configuration, enabling organizations to enhance their threat detection capabilities quickly. |
| 4. Improved Operational Efficiency | |
| Streamlined Threat Hunting | Fresh IOCs empower threat hunters to focus on emerging threats with precision and speed. |
| Reduced MTTR | SOC and DFIR teams can lower Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by accessing enriched threat intelligence directly in workflows. |
How to Integrate ANY.RUN’s TI Feeds into Security Operations
Step 1: Setting Up the Integration
Log into the ANY.RUN dashboard with an account registered to a custom domain email.
First, navigate to the Feeds Dashboard and select the desired IOC categories (URLs, IPs, domains, etc.) and Copy the feed URL and API key.
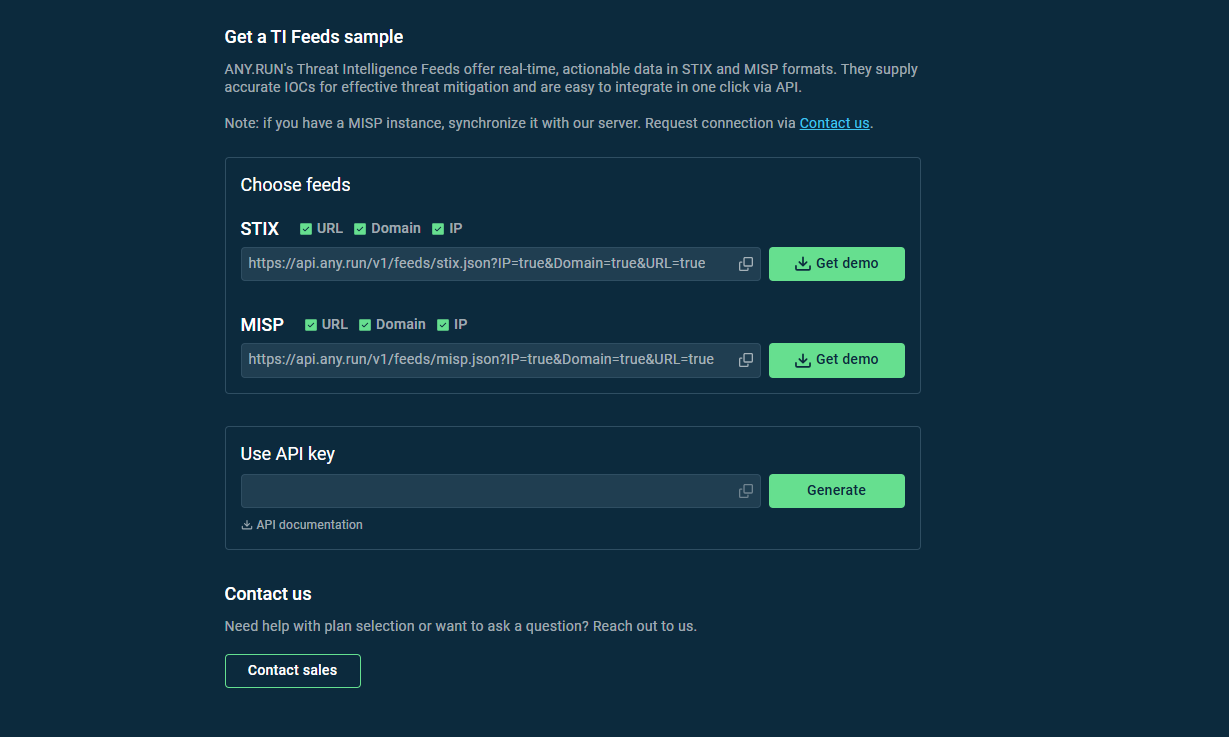
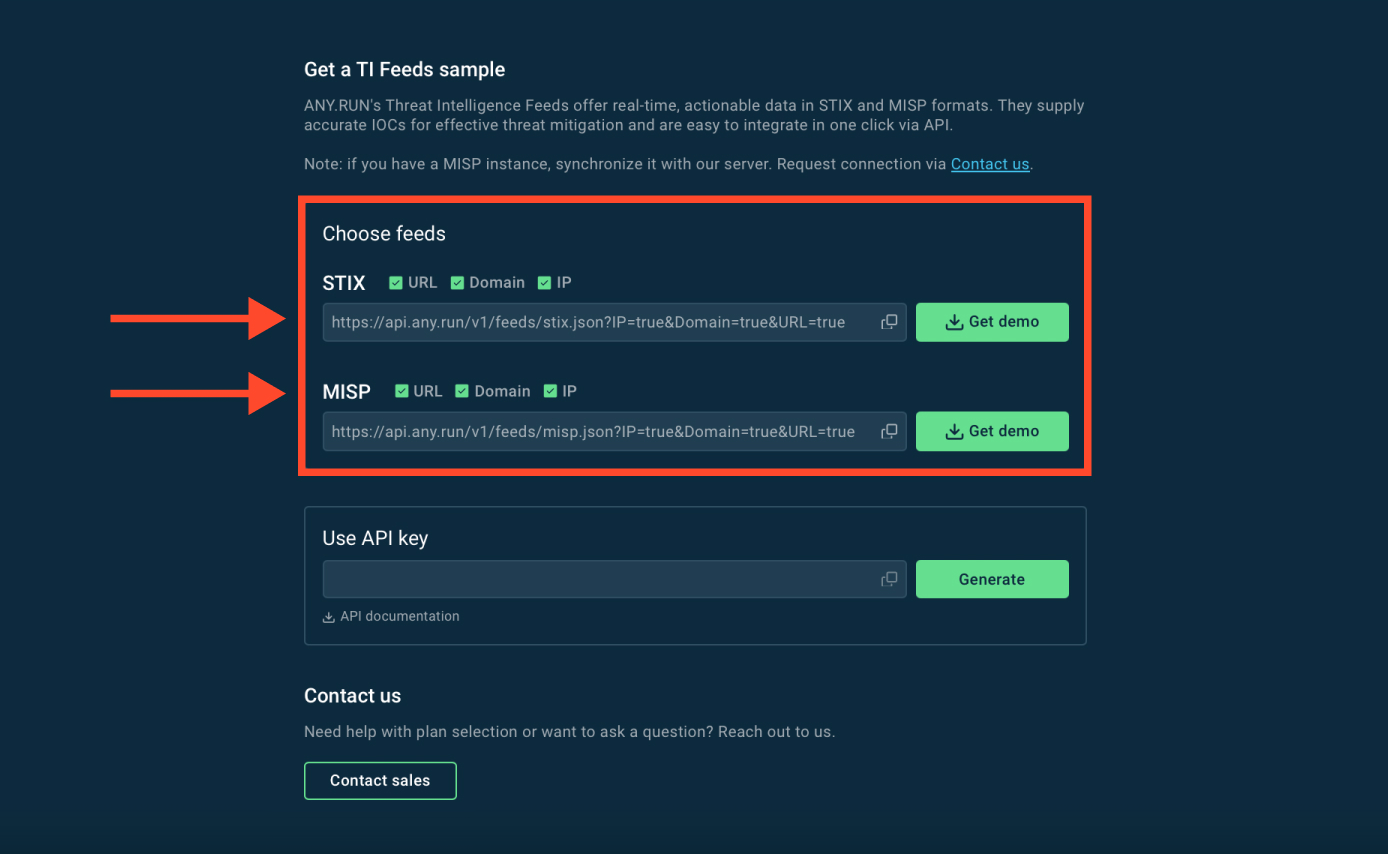
Paste these credentials into the Threat Intelligence Feeds section of your SIEM or TIP system. Details vary by vendor but typically involve finding a “source input” for threat intelligence.
Contact ANY.RUN To integrate ANY.RUN TI Feeds in your organization
ANY.RUN’s Threat Intelligence Feeds Integration offers a transformative approach to effective cybersecurity operations for SOC and DFIR teams.
By providing enriched, real-time IOC data collected from a global community of malware researchers, these feeds optimize threat detection and response processes.
The ability to integrate seamlessly with SIEMs and TIPs while providing direct access to sandbox-linked insights enables actionable, precise decision-making.
The emphasis on freshness, contextual enrichment, and compatibility with industry standards makes ANY.RUN’s TI Feeds indispensable for organizations aiming to strengthen their security posture.
Whether you are responding to incidents, hunting threats, or defending against evolving threats, ANY.RUN is a powerful partner in your cybersecurity strategy.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
