A massive botnet of over 130,000 compromised devices is conducting password-spray attacks against Microsoft 365 (M365) accounts worldwide, targeting basic authentication to evade multi-factor authentication.
According to a report by SecurityScorecard, the attackers are leveraging credentials stolen by infostealer malware to target the accounts at a large scale.
The attacks rely on non-interactive sign-ins using Basic Authentication (Basic Auth) to bypass Multi-Factor Authentication (MFA) protections and gain unauthorized access without triggering security alerts.
“Organizations relying solely on interactive sign-in monitoring are blind to these attacks. Non-interactive sign-ins, commonly used for service-to-service authentication, legacy protocols (e.g., POP, IMAP, SMTP), and automated processes, do not trigger MFA in many configurations,” warns SecurityScorecard.
“Basic Authentication, still enabled in some environments, allows credentials to be transmitted in plain form, making it a prime target for attackers.”
Source: SecurityScorecard
Basic Auth is an outdated authentication method where a user’s credentials are sent in plaintext or base64 encoded form with every request to a server.
It lacks modern security features like MFA and token-based authentication, and Microsoft plans to deprecate it in favor of OAuth 2.0 in September 2025, already having disabled it for most Microsoft 365 services.
The newly discovered botnet uses Basic Auth attempts targeting a large number of accounts with common/leaked passwords.
Since Basic Auth is non-interactive, when there’s a match with the tried credentials, the attackers aren’t prompted for MFA and very often aren’t restricted by Conditional Access Policies (CAP), allowing the attackers to quietly verify account credentials.
Once credentials are verified, they can be used to access legacy services that do not require MFA or in more sophisticated phishing attacks to bypass the security feature and gain full access to the account.
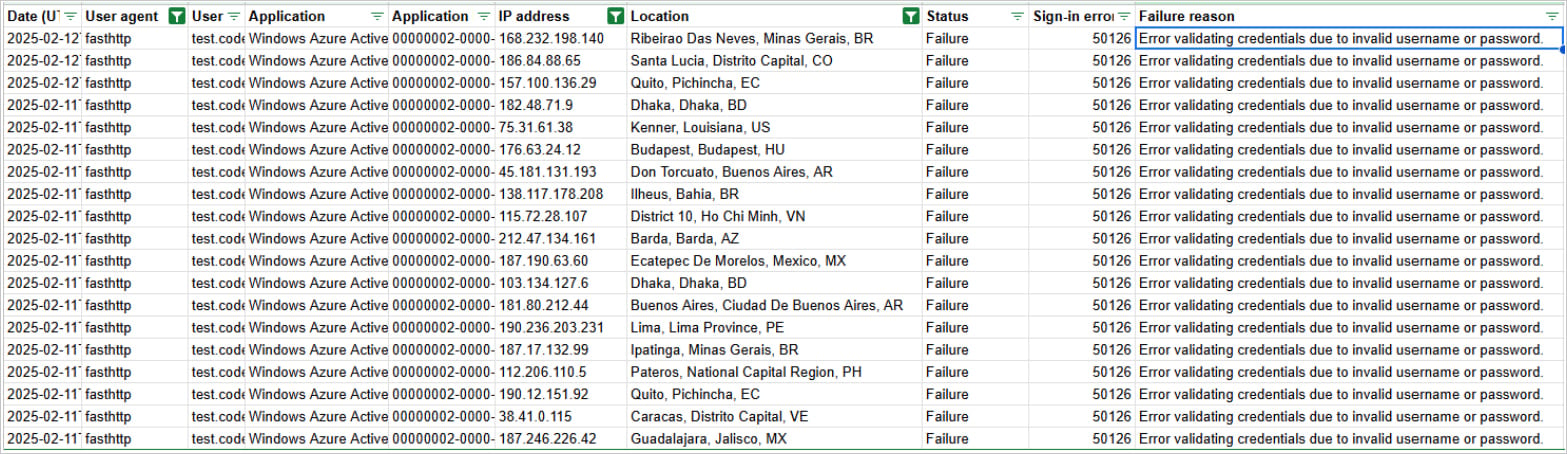
SecurityScorecard also highlights that you may be able to see signs of the password-spray attacks in Entra ID logs, which will show increased login attempts for non-interactive logins, multiple failed login attempts from different IPs, and the presence of the “fasthttp” user agent in the authentication logs.
In January, SpearTip warned of threat actors conducting Microsoft 365 password attacks using the FastHTTP Go library in a similar manner but did not mention the non-interactive logins. It is unclear if that is a newer development by the botnet to evade detection.
Possible link to Chinese threat actors
SecurityScorecard reports that the operators of the botnet are likely Chinese-affiliated, although there’s no clear or confident attribution yet.
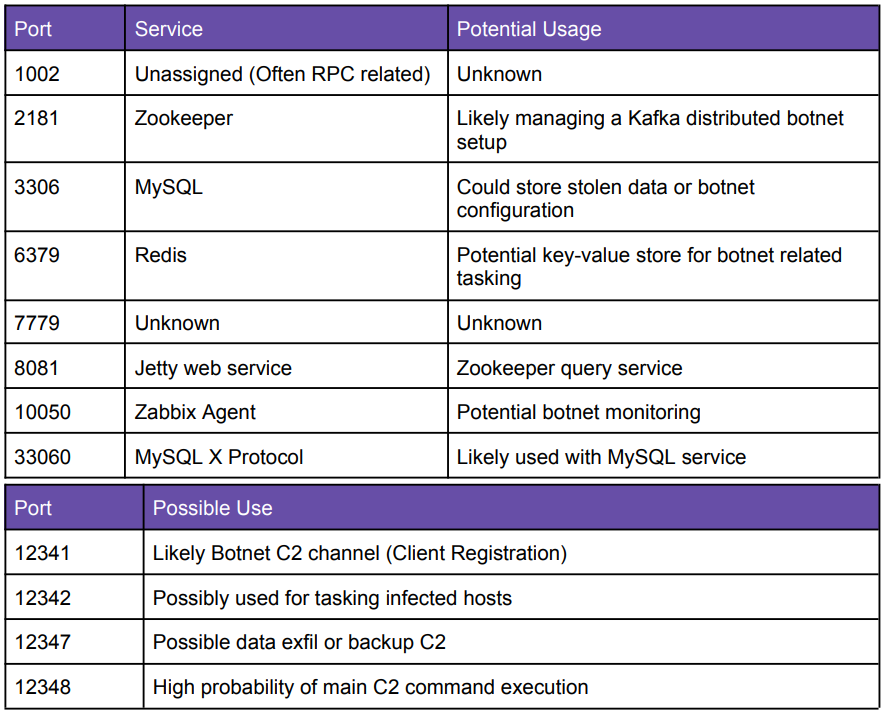
The botnet operates through six primary command and control (C2) servers hosted by U.S. provider Shark Tech, while it proxies traffic through Hong Kong-based UCLOUD HK and China-linked CDS Global Cloud.
The C2 servers run Apache Zookeeper and use Kafka to manage botnet operations.
The system timezone on the C2 servers is set to Asia/Shanghai, while their uptimes indicate the botnet has been active since at least December 2024.
Source: SecurityScorecard
The botnet uses over 130,000 compromised devices to spread out login attempts across different IP addresses, which helps evade getting flagged for suspicious activity and blocked.
Organizations should disable Basic Auth in Microsoft 365, block the IP addresses listed in the report, enable CAPs to restrict login attempts and use MFA on all accounts.
