The entire database for the notorious BreachForums v1 hacking forum was released on Telegram Tuesday night, exposing a treasure trove of data, including members’ information, private messages, cryptocurrency addresses, and every post on the forum.
This data comes from a database backup allegedly sold by Conor Fitzpatrick, aka Pompompurin. In 2022, after the RaidForums hacking forum was seized, Fitzpatrick launched BreachForums v1, which was later seized by the FBI after Fitzpatrick was arrested.
Fitzpatrick allegedly sold this database in July while he was out on bail. The data has since been circulating among different threat actors, with one attempting to sell it for $150,000 later that month.
While the database was shared with Have I Been Pwned at the time, it was never publicly released until this past weekend.
Drip … drip … drip
Since the weekend, there has been a steady leak of data from the BreachForums v1 database.
It started with the threat actor Emo releasing a limited export of member data, including member names, email addresses, and IP addresses after they were banned from the current incarnation of BreachForums.
However, as infighting continued among the BreachForum community members, Emo leaked the entire database Tuesday night, exposing a tremendous amount of additional data.
“Find enclosed the full BreachForum v1 database, every record up to November 29th, 2022,” Emo posted to Telegram.
“This database includes everything, Private Messages, Threads, Payment logs, detailed IP logs for each user, etc. I originally only leaked the user table to discourage it from being sold behind the scenes by BreachForum staff, however it’s become apparent that so many people have the database now that it being leaked is an inevitability.”
“This will give everyone a chance to review their records and fix holes in their OPSEC.”
Source: BleepingComputer
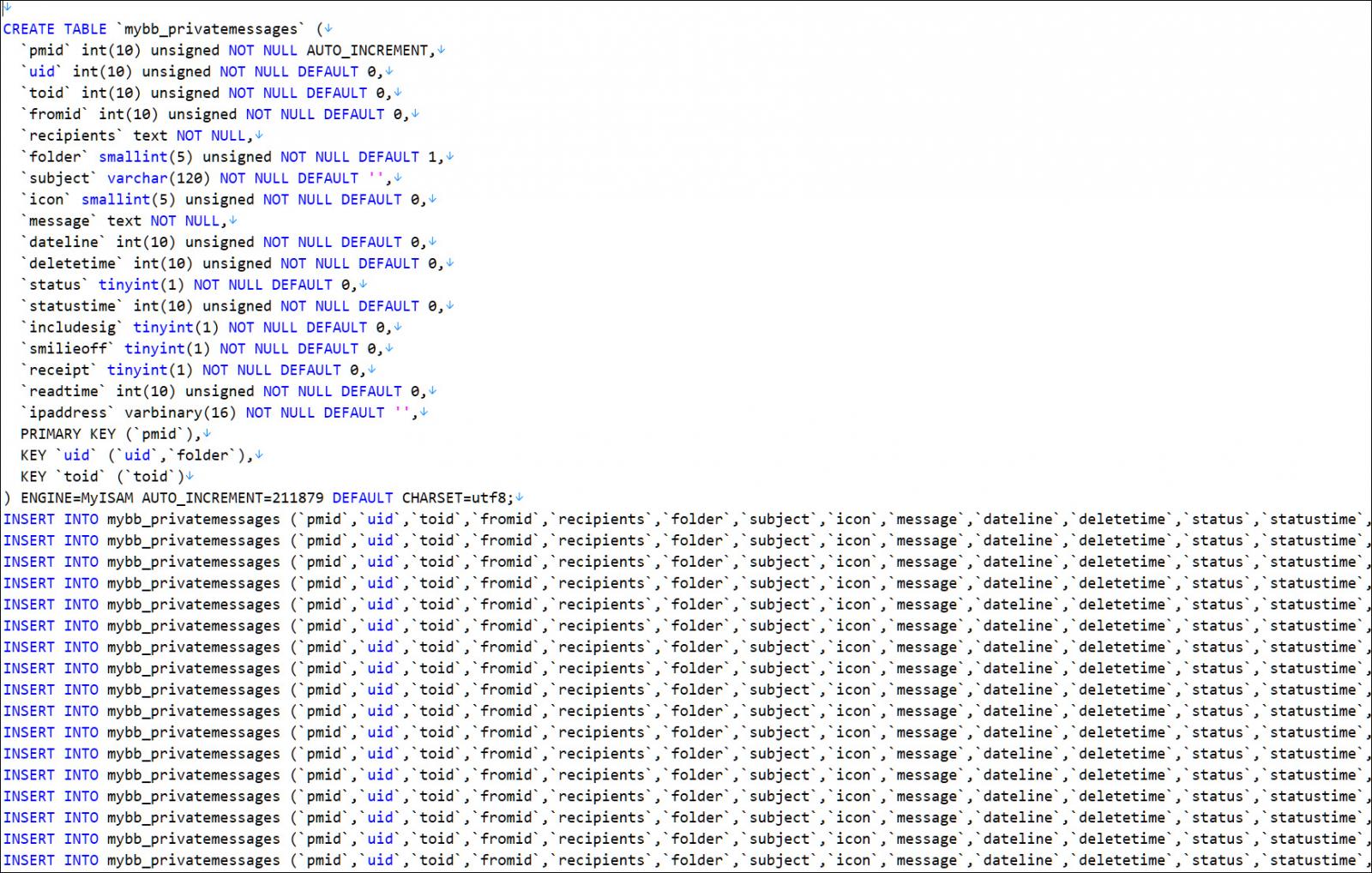
BleepingComputer has obtained the database and, based on timestamps in the database records, can confirm it is an entire backup of the MyBB forum that was created on November 28th, 2022, at approximately 7 PM ET.
The database contains all the forum data, including members’ hashed passwords, private messages between users, cryptocurrency addresses used to purchase forum credits, and every post on the site.
The private messages are particularly damaging, with threat actors messaging each other about their exploits, expressing a desire to purchase access to networks, or seeking access to the latest stolen data.
Source: BleepingComputer
The data also includes cryptocurrency addresses used to purchase site credits, which allowed members to view content hidden in forum posts.
These addresses will allow crypto intelligence firms to tie historic cryptocurrency payments to specific threat actors.
While law enforcement already has this database after they seized the site and arrested its owner in 2023, other threat actors, journalists, and researchers have not seen it until now.
Even though the data is nearly two years old, it will still be an operational security (OPSEC) test for many threat actors who frequented the forums.
OPSEC is a method used to protect sensitive information that could be used by adversaries to gain an advantage or identify you.
Did the hacking forum members adequately perform OPSEC by using VPNs or Tor when connecting to the site, using privated email addresses, or properly hiding their identities?
Only time will tell as researchers and journalists use this data to build threat actor profiles that tie them to other malicious activity.




