A 45-year-old from Irvine, California, has pleaded guilty to laundering at least $25 million stolen in a massive $230 million cryptocurrency heist.
Kunal Mehta (also known as “Papa,” “The Accountant,” and “Shrek”) is the eighth defendant to plead guilty for his participation in this scheme following charges brought by the Department of Justice in May 2025.
According to court documents, the defendant was part of a large group that, through social engineering, gained access to victims’ cryptocurrency accounts between October 2023 and March 2025 and transferred funds into crypto wallets under their control.

The crime ring included members (mostly 18-, 19-, and 20-year-olds) from California, Connecticut, New York, Florida, and abroad, and it grew through friendships developed while playing online games. Mehta served as a money launderer for the group, while others were involved in organizing, identifying targets, hacking, making calls, and stealing hardware crypto wallets.
In total, fourteen suspects were charged for their alleged involvement in the theft and laundering of $230 million in cryptocurrency, including 20-year-old Malone Lam (aka “Greavys,” “Anne Hathaway,” and “$$$”) and 21-year-old Jeandiel Serrano (aka “Box,” “VersaceGod,” and “@SkidStar”) who were arrested in Miami in September 2024.
The following defendants, who were indicted in May 2025, also face charges of obstruction of justice and conspiracy to commit wire fraud, besides cyber-enabled racketeering conspiracy and money laundering:
- Marlon Ferro, 19 (Santa Ana, California)
- Hamza Doost, 21 (Hayward, California)
- Conor Flansburg, 21 (Newport Beach, California)
- Ethan Yarally, 18 (Richmond Hill, New York)
- Cody Demirtas, 19 (Stuart, Florida)
- Aakash Anand, 22 (New Zealand)
- Evan Tangeman, 21 (Newport Beach, California)
- Joel Cortes, 21 (Laguna Niguel, California)
- First Name Unknown-1, Last Name Unknown-1 aka “Chen” and “Squiggly” (location unknown)
- First Name Unknown-2, Last Name Unknown-2 aka “Danny” and “Meech” (location unknown)
- John Tucker Desmond, 19 (Huntington Beach, California)
In an August 18th attack, Lam and another accomplice stole over 4,100 Bitcoin from a Washington, D.C., victim, which was worth over $230 million (now valued at more than $384.5 million). They reportedly laundered the stolen cryptocurrency using crypto mixers and exchanges, “peel chains,” pass-through wallets, and virtual private networks (VPNs) to hide their locations and identities.
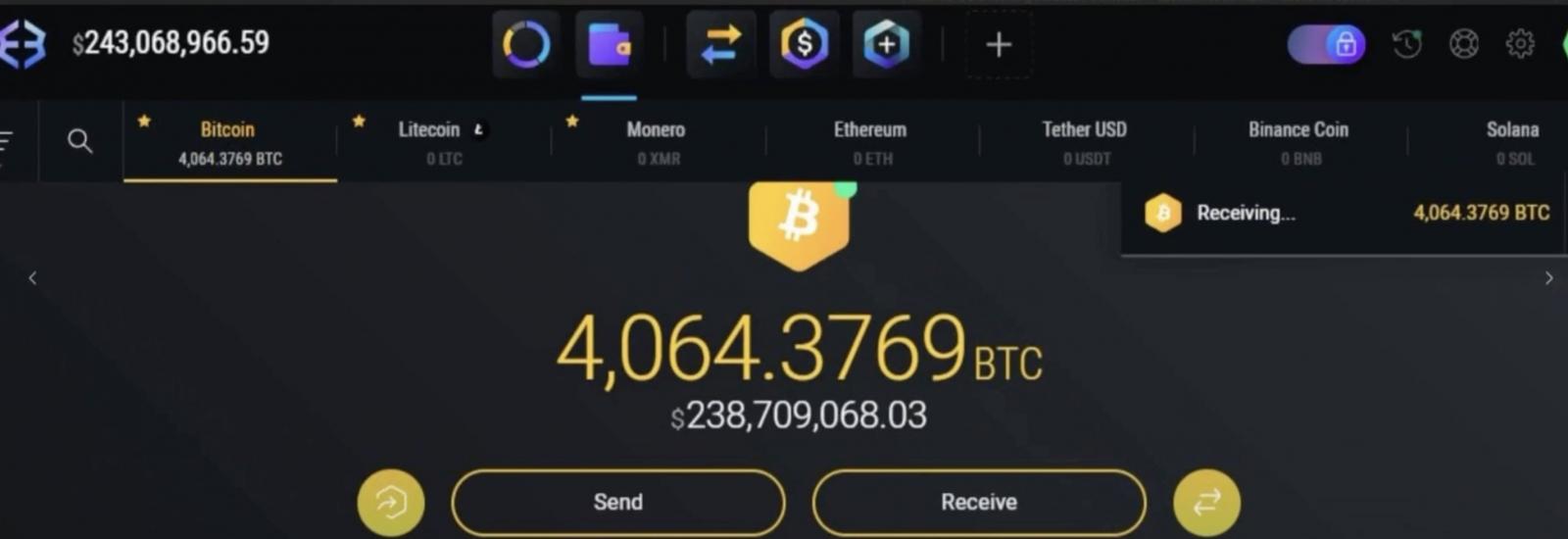
However, while most of the stolen cryptocurrency was converted to Monero to hide the attackers’ identity, they reportedly made critical errors, inadvertently linking the laundered funds to the original amounts stolen.
“Mehta created multiple shell companies in 2024 for the purpose of laundering funds through bank accounts created to give the appearance of legitimacy. To facilitate crypto-to-wire money laundering services, Mehta received stolen cryptocurrency from the group, which they had already laundered,” the DOJ said on Tuesday.
“Mehta then transferred the cryptocurrency to associates who further laundered it through sophisticated blockchain laundering techniques. The solen funds returned to Mehta’s shell company bank accounts through incoming wire transfers from additional shell companies organized by others throughout the United States.”
The investigators found that Mehta would typically charge a 10% fee for his services, which included converting stolen cryptocurrency to cash and making wire transfers for the group.
The stolen cryptocurrency was used to finance the group’s lavish lifestyles, which allegedly included spending the funds on private jet rentals, at least 28 luxury cars (worth between $100,000 and $3.8 million), private security guards, designer handbags, high-end watches, nightclub outings, and international travel.
“Mehta is the eighth defendant to plead guilty for his role in this scheme,” added FBI Special Agent in Charge Reid Davis this week. “Today’s plea reaffirms the FBI’s commitment to exposing fraudsters and should remind Americans to beware of online scammers: Do not reply to calls, emails, or texts that request personal information, such as your password, PIN, or any one-time passwords that are sent to your email or phone.”

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
