Security researchers are sounding the alarm over CastleLoader, a stealthy first-stage malware loader now implicated in campaigns targeting US-based government entities and multiple high-value industries.
According to a recent deep-dive by ANY.RUN’s malware analysis team, the loader has been observed in attacks against public sector networks, IT providers, logistics and travel companies, as well as critical infrastructure organizations across Europe, with one tracked campaign alone impacting at least 469 devices.
CastleLoader serves as the initial foothold in a broader intrusion chain, designed to silently deliver follow-on payloads such as information stealers and remote access trojans (RATs).
Once established, these secondary tools enable large-scale credential theft and persistent access to victim environments, significantly elevating the risk of data exfiltration and long-term compromise.
The loader has been in active use since early 2025 and has quickly gained popularity among threat actors due to its high infection rate and flexible deployment model.
In several campaigns, CastleLoader is deployed via the “ClickFix” social engineering technique, where victims are tricked into manually executing attacker-supplied commands under the guise of troubleshooting, verification, or software updates.
This setup, ClickFix provides the initial access vector, while CastleLoader operates as the second stage that injects and runs the main malicious payload entirely in memory.
ANY.RUN’s analysis reveals that CastleLoader relies on a deliberately complex, multi-stage execution chain to evade detection: an Inno Setup installer drops a set of auxiliary files, including AutoIt3.exe and a compiled AutoIt script, which then prepares the environment and launches a suspended instance of jsc.exe, an older JScript.NET compiler.
Through a carefully orchestrated process hollowing technique, CastleLoader injects a malicious PE image into the address space of jsc.exe, alters the process context, and resumes execution so that the final payload exists only as an in-memory module inside an apparently legitimate process.
Because each stage appears benign in isolation and the core payload never resides on disk in its final form, static signatures, simple heuristics, and basic process monitoring are largely ineffective.
Many EDR tools see only what looks like a normal installer and a legitimate Windows component, while the true malicious logic runs inside a modified but still “normal-looking” process.
To fully map CastleLoader’s behavior, ANY.RUN analysts combined interactive sandbox telemetry with in-depth reverse engineering.
To get a basic overview of the binary, let’s process it via DIE (Detect It Easy).
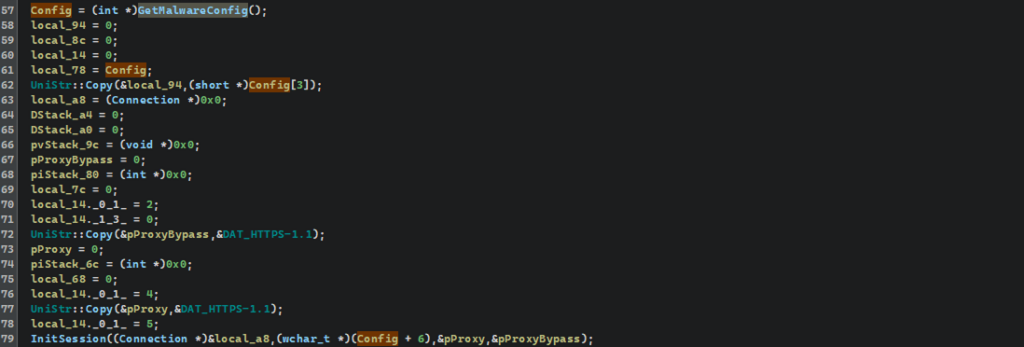
By dumping the injected module from memory and loading it into Ghidra, they uncovered a custom API-resolving routine based on hashed WinAPI names and a bespoke string decryption mechanism for configuration data.
Using a purpose-built parser, the team was able to automatically decode CastleLoader’s runtime configuration, including network parameters, mutex values, user-agent strings, and its command-and-control (C2) endpoint.
The configuration includes an HTTP-based C2 at 94[.]159[.]113[.]32, as well as hardcoded paths for tasking and status reporting, confirming that the malware is designed for structured, remotely controlled operations.
Static strings, but a mass of encrypted bytes packaged into DWORDs with two UTF-16LE characters and placed right on the stack.
Researchers emphasize that CastleLoader exemplifies a broader trend in which modern loaders are engineered to bypass both signature-based and simplistic behavioral defenses.
As a result, defenders are increasingly reliant on real-time threat intelligence derived from live malware executions.
ANY.RUN notes that telemetry and indicators harvested from thousands of sandboxed samples feed directly into threat intelligence services, enabling security operations centers (SOCs) to spot emerging loaders, stealers, and RATs as they appear in the wild, rather than waiting for traditional reporting cycles.
For US government entities and critical infrastructure operators, CastleLoader underscores the need to monitor for in-memory-only payloads, scrutinize unusual process chains involving system tools like jsc.exe, and integrate high-fidelity threat intelligence feeds.
IOCs
| File Name | Description | MD5 | SHA1 | SHA256 |
|---|---|---|---|---|
| 8b7c1657f4d5cf0cc82d68c1f1a385adf0de27d46fc544bba249698e6b427856.exe | Inno Setup Installer | 9A0960C674378A049B8D9AD0E1C641C3 | 0580A364AB986B051398A78D089300CF73481E70 | 8B7C1657F4D5CF0CC82D68C1F1A385ADF0DE27D46FC544BBA249698E6B427856 |
| freely.a3x | AutoIt Script | AFBABA49796528C053938E0397F238FF | DD029CD4711C773F87377D45A005C8D9785281A3 | FDDC186F3E5E14B2B8E68DDBD18B2BDA41D38A70417A38E67281EB7995E24BAC |
| payload.exe | CastleLoader Core Module | 1E0F94E8EC83C1879CCD25FEC59098F1 | 9E11E8866F40E5E9C20B1F012D0B68E0D56E85B3 | DFAF277D54C1B1CF5A3AF80783ED878CAC152FF2C52DBF17FB05A7795FE29E79 |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
