Category: Bleeping Computer
The ALPHV/BlackCat ransomware gang has shut down its servers amid claims that they scammed the affiliate responsible for the attack on…
The European Commission has fined Apple €1.8 billion, or approximately $1.95 million, for allegedly abusing its market dominance in music…
American Express is warning customers that credit cards were exposed in a third-party data breach after one of its service…
The Main Intelligence Directorate (GUR) of Ukraine’s Ministry of Defense claims that it breached the servers of the Russian Ministry…
The National Intelligence Service (NIS) in South Korea warns that North Korean hackers target domestic semiconductor manufacturers in cyber espionage…
BleepingComputer has discovered a content farm operating some 60+ domains named after popular media outlets, including the BBC, CNBC, CNN,…
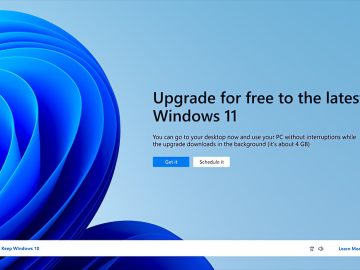
Starting next month, Microsoft nag screens pushing Windows 11 will also show up on non-managed enterprise devices running Windows 10 Pro…
Security researcher HaxRob discovered a previously unknown Linux backdoor named GTPDOOR, designed for covert operations within mobile carrier networks. The…
Microsoft patched a high-severity Windows Kernel privilege escalation vulnerability in February, six months after being informed that the flaw was…
A new phishing kit named CryptoChameleon is being used to target Federal Communications Commission (FCC) employees, using specially crafted single sign-on…
BleepingComputer has discovered a content farm operating some 60+ domains named after popular media outlets, including the BBC, CNBC, CNN,…
The Düsseldorf Police in Germany have seized Crimemarket, a massive German-speaking illicit trading platform with over 180,000 users, arresting six…