Category: CyberDefenseMagazine
Security Journey is a secure coding education provider that is focused on addressing the evolving landscape of cybersecurity threats with…
By Mohit Shrivastava, Chief Analyst ICT, Future Market Insights Zero trust security is a method of cybersecurity that undertakes that…
With security breaches on the rise, cybersecurity has become a serious enterprise-wide risk management issue that needs to be strategically…
Private equity fund-level technology leaders can play an impactful role in protecting their portfolio companies from cyber-attacks, from due diligence…
By Ameya Khankar, Cybersecurity Consultant for Critical Infrastructure Companies undergoing digital transformation have decided to take the plunge into modernizing…
By Milica D. Djekic According to many media’s releases – the Shodan is characterized as the scariest searching tool of…
By Howie Robleza, Freelance Writer, Avigilon Security is an important component for the development of any business. However, hackers are…
By Craig Burland, CISO, Inversion6 Computer-controlled devices are all around us. From delivery robots to smart buildings to shipping and…
Today’s cyber attackers are looking beyond network systems and devices to target organizations through digital platforms outside your perimeter. It’s…
Russian hacking efforts have highlighted weaknesses in U.S. cybersecurity infrastructure. By Jamie Eiseman, George Washington University Russia is invading Ukraine,…
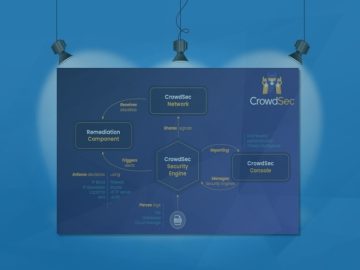
CrowdSec is a modern, collaborative cybersecurity company committed to proactively safeguarding digital assets. With a growing community of 65,000+ active…
Cycode’s modern approach to application security enables organizations to effectively secure their cloud-native applications with cost-efficient use of tooling and staff…