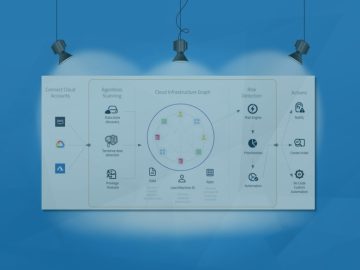
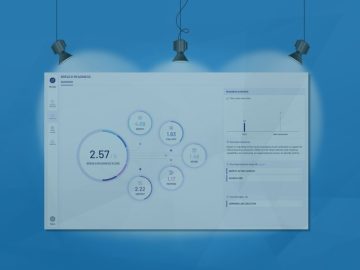
Category: CyberDefenseMagazine
Normalyze is a pioneering provider of data-first cloud security solutions that help global enterprises secure their data wherever it is…
Arctic Wolf is a global leader in security operations, enabling customers to manage their cyber risk in the face of…
Introduction There is ever increase in security breaches resulting in serious business implications despite the proliferation and sophistication of security…
Bias in artificial intelligence (AI) is one of the technology’s most prominent issues. Stories of AI repeating and even exaggerating…
By Miguel Clarke, GRC and Cybersecurity Lead at Armor and former FBI Special Agent I was first introduced to the…
Protecting Emerging Startups from Advanced Cyber Threats with Proactive Security Measures By Babar Khan Akhunzada, Founder, SecurityWall Startups are known…
Cigent Technologies is a data security company that is renowned for their data protection capabilities. They’ve had a long-standing relationship…
Cloud and SaaS have become the new nexus for today’s cyber attackers. Are you ready to respond to a breach? …
By Vrinda Khurjekar, Senior Director, AMER business, Searce The sky is the limit for cloud migration as Gartner predicts that…
By Anurag Lal, President and CEO of NetSfere Securing business communication in the financial services industry is now more than…
By Milica D. Djekic The industrial control systems (ICS) are usually the part of critical infrastructure to every country or…
Oligo Security is one of the leading open source cybersecurity platforms, pioneering the next wave of application security with a…