Category: CyberDefenseMagazine
Strategies for Preventing Data Breaches in the Translation Industry By Ofer Tirosh, CEO of Tomedes When it comes to translation,…
Call us Toll Free (USA): 1-833-844-9468 International: +1-603-280-4451 M-F 8am to 6pm EST Contact us: [email protected] Cyber Defense Magazine is…
Penetration Testing Market size worth over $5.5 Bn by 2031 By Aashi Mishra, Sr. Content Writer, Research Nester In January…
By Karthik Kannan, Founder and CEO, Anvilogic Watch any superhero movie and it follows the same playbook: the story revolves…
Black Hat, the producer of the cybersecurity industry’s most established and in-depth security events, today announced the successful completion of…
By Dr. Terence Liu, CEO, TXOne Networks Highly publicized cyberattacks have focused governments globally on re-examining and bolstering their cybersecurity…
By Matt Honea, Head of Security and Compliance, Forward Networks The challenge to adequately secure a large complex enterprise network,…
SIGN UP NOW Cyber threat adversary infrastructure refers to the combination of assets that cybercriminals and malicious actors use to…
By Howie Robleza, Freelance Writer, Avigilon Effective security strategies are fundamental to the success of any business with both physical…
Abstract: The topic of scientific works on the implementation of modern technologies and systems of automated management of the enterprise,…
Abstract: The topic of scientific works on the implementation of modern technologies and systems of automated management of the enterprise,…
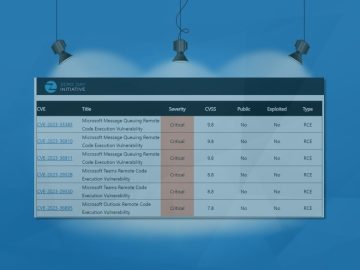
Formed by TrendMicro, the Zero Day Initiative (ZDI) was created to encourage the reporting of 0-day vulnerabilities privately to the…