Category: CyberDefenseMagazine
A business ecosystem is a borderless entity. Where organizations operate across vast, global networks, achieving a comprehensive view of their…
Welcome back to this series, introducing the IEC 62443 standard. The first article was a general introduction to IEC 62443,…
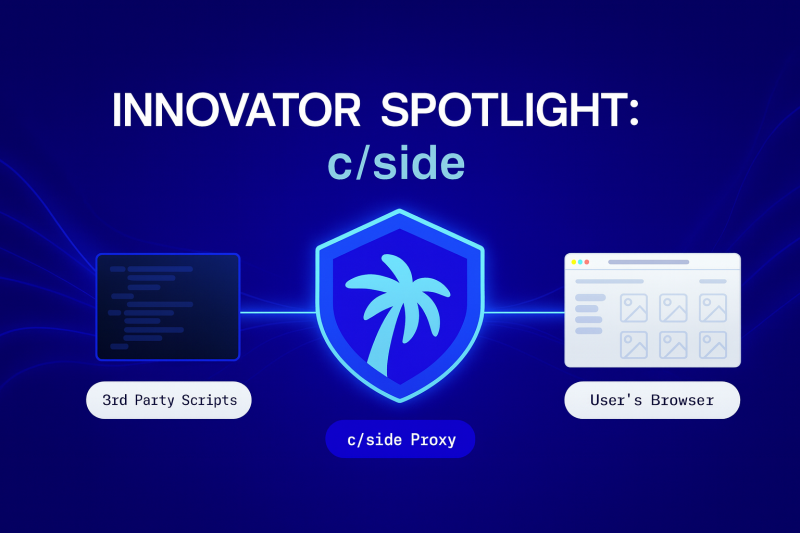
Securing the Browser’s Blind Spot By Victoria Hargrove, CDM Reporter What CSide Does Most security stacks fortify servers, databases, and…
Cross-domain solutions (CDS) consist of the secure exchange of information between security domains. This type of solution, which emerged as…
In a significant step to secure the defense industrial base (DIB), the Department of Defense (DoD) has officially released the…
Driving through the quiet, endless beauty of the Nevada desert, I let the raspy voice of Jim Morrison carry me…
There’s a lot of noise around compliance. New regulations seem to pop up every year, each promising to fix the…
Cybersecurity has emerged as a critical and ongoing battle against a dynamic and pervasive global threat. The landscape is evolving…
We live in an era where your next big idea could come from an employee working out of a cafe…
Among the variety of cyber-attacks that we witness happening around us, Zero-day attacks are remarkably insidious in nature. Due to…
The cybersecurity landscape is constantly evolving, and security operations centers (SOCs) are feeling the pressure to stay ahead of increasingly…
The term “In the Wild” is broadly used to refer to any activity that has been observed outside of a…