Category: CyberDefenseMagazine
The battle against cybercrime continues to be a significant topic for organizations across all industries, however the threat to the…
Dealerships handle sensitive information, such as credit applications and personal financial records, daily. A data breach can lead to profound…
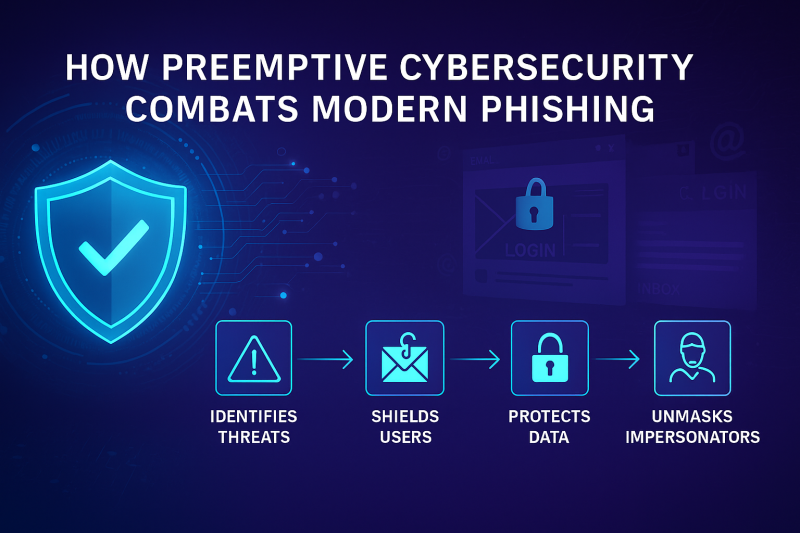
Phishing isn’t what it used to be. It’s no longer fake emails with bad grammar and sketchy links. With AI,…
Your team’s ability to identify phishing attempts in their inboxes has the potential to make or break your entire security…
Software is the invisible infrastructure of our world, powering everything from critical systems to everyday devices. But its ubiquity makes…
The figures are appalling – 60% of small businesses fail within six months of a cyber-attack. Cyber attackers are all…
The week of August 4th, I had the opportunity to attend two exciting conferences in the cybersecurity world: Black Hat…
According to recent study by Research Nester, the global insider threat protection market Size was valued at USD 4 billion in 2023…
According to recent study by Research Nester, the global insider threat protection market Size was valued at USD 4 billion in 2023…
The healthcare industry, one of the most targeted for data breaches, is facing an escalating crisis. According to the White House,…
The automotive world is transforming at breakneck speed. We’re seeing increasing connectivity, the rise of autonomous driving, and the emergence…
Generative artificial intelligence (AI) continues to be a hot topic as pundits, media outlets and entrepreneurs consider the opportunities presented…