Category: CyberDefenseMagazine
Understanding Skills and Their Importance A skill is an individual’s ability to perform an action efficiently and effectively, providing a…
The battle didn’t begin today, and it’s not ending anytime soon, as cyber threats are changing at a rate never…
Digital Traces in Code Every program contains characteristic patterns of its developers, starting with the choice of variable names and…
Organizations across the world are facing mounting pressures to comply with a complex web of regulations. Failure to meet these…
Effective task delegation is a vital skill for any manager. Strategically transferring specific tasks to capable team members can boost…
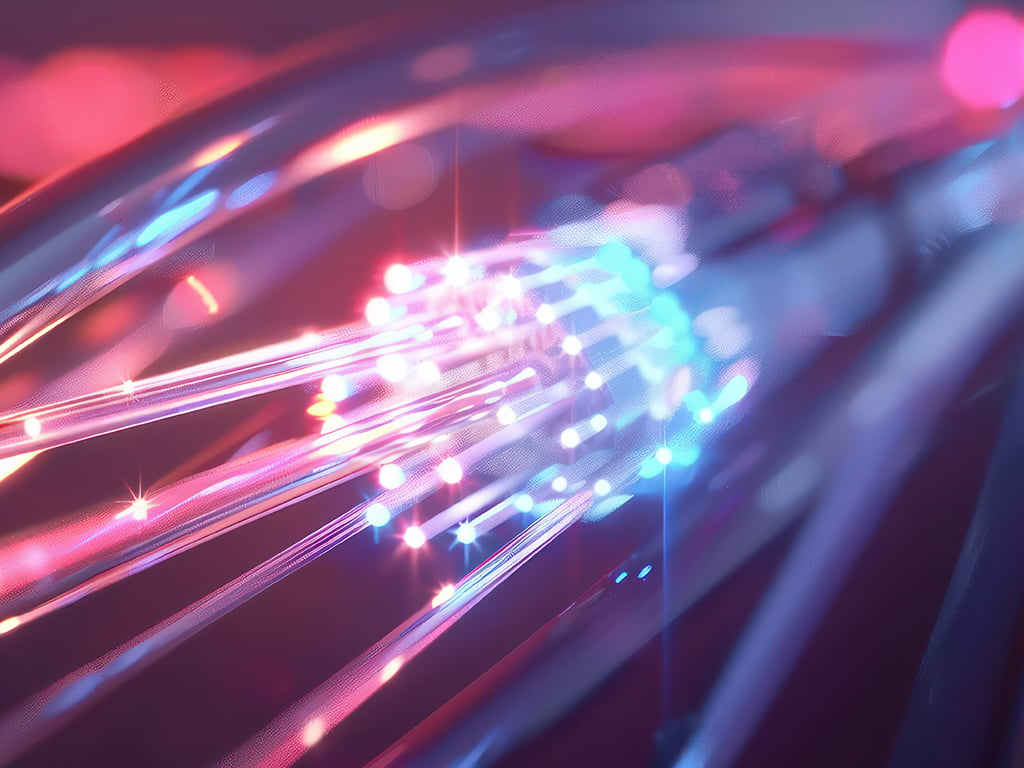
Fiber optic sensors have quickly become a cornerstone of modern technology. Renowned for their precision and versatility, they are used…
The recent implementation of the Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) program in late 2024 raises important…
Email has become both a lifeline for communication and a prime target for cybercriminals. For small and medium-sized businesses, it…
Online accounts are integral to cloud computing, encompassing private, public, and hybrid services that store vast amounts of data across…
Introduction In the business world, operational resilience can be compared to the physical concept of resilience, which defines the ability…
The scale of cyberattacks seen today is both unprecedented and harrowing. Crucial sectors including healthcare, finance, and education have found…
In today’s interconnected business world, organizations rely on a vast web of third-party vendors, suppliers, and partners. While these relationships…